Recent from talks
Contribute something
Nothing was collected or created yet.
RIPEMD
View on Wikipedia| General | |
|---|---|
| Designers | Hans Dobbertin, Antoon Bosselaers and Bart Preneel |
| First published | 1992 |
| Certification | RIPEMD-160: CRYPTREC (Monitored) |
| Detail | |
| Digest sizes | 128, 160, 256, 320 bits |

RIPEMD (RIPE Message Digest) is a family of cryptographic hash functions developed in 1992 (the original RIPEMD) and 1996 (other variants). There are five functions in the family: RIPEMD, RIPEMD-128, RIPEMD-160, RIPEMD-256, and RIPEMD-320, of which RIPEMD-160 is the most common.[citation needed]
The original RIPEMD, as well as RIPEMD-128, is not considered secure because 128-bit result is too small and also (for the original RIPEMD) because of design weaknesses. The 256- and 320-bit versions of RIPEMD provide the same level of security as RIPEMD-128 and RIPEMD-160, respectively; they are designed for applications where the security level is sufficient but longer hash result is necessary.
While RIPEMD functions are less popular than SHA-1 and SHA-2, they are used, among others, in Bitcoin and other cryptocurrencies based on Bitcoin.[1]
History
[edit]The original RIPEMD function was designed in the framework of the EU project RIPE (RACE Integrity Primitives Evaluation) in 1992.[2][3] Its design was based on the MD4 hash function. In 1996, in response to security weaknesses found in the original RIPEMD,[4] Hans Dobbertin, Antoon Bosselaers and Bart Preneel at the COSIC research group at the Katholieke Universiteit Leuven in Leuven, Belgium published four strengthened variants: RIPEMD-128, RIPEMD-160, RIPEMD-256, and RIPEMD-320.[5]
In August 2004, a collision was reported for the original RIPEMD.[6] This does not apply to RIPEMD-160.[7]
In 2019, the best collision attack for RIPEMD-160 could reach 34 rounds out of 80 rounds, which was published at CRYPTO 2019.[8]
In February 2023, a collision attack for RIPEMD-160 was published at EUROCRYPT 2023, which could reach 36 rounds out of 80 rounds with time complexity of 264.5.[9]
In December 2023, an improved collision attack was found based on the technique from the previous best collision attack, this improved collision attack could reach 40 rounds out of 80 round with a theoretical time complexity of 249.9.[10]
RIPEMD-160 hashes
[edit]The 160-bit RIPEMD-160 hashes (also termed RIPE message digests) are typically represented as 40-digit hexadecimal numbers. The following demonstrates a 43-byte ASCII input and the corresponding RIPEMD-160 hash:
RIPEMD-160("The quick brown fox jumps over the lazy dog") =
37f332f68db77bd9d7edd4969571ad671cf9dd3b
RIPEMD-160 behaves with the desired avalanche effect of cryptographic hash functions (small changes, e.g. changing d to c, result in a completely different hash):
RIPEMD-160("The quick brown fox jumps over the lazy cog") =
132072df690933835eb8b6ad0b77e7b6f14acad7
The hash of a zero-length string is:
RIPEMD-160("") =
9c1185a5c5e9fc54612808977ee8f548b2258d31
Implementations
[edit]Below is a list of cryptography libraries that support RIPEMD (specifically RIPEMD-160):
See also
[edit]References
[edit]- ^ "Transactions — Bitcoin". developer.bitcoin.org. Retrieved 2025-06-27.
- ^ Dobbertin, Hans; Bosselaers, Antoon; Preneel, Bart (21–23 February 1996). RIPEMD-160: A strengthened version of RIPEMD (PDF). Fast Software Encryption. Third International Workshop. Cambridge, UK. pp. 71–82. doi:10.1007/3-540-60865-6_44.
- ^ Bosselaers, Antoon; Preneel, Bart (1995). Bosselaers, Antoon; Preneel, Bart (eds.). Integrity Primitives for Secure Information Systems. Final Report of RACE Integrity Primitives Evaluation (RIPE-RACE 1040). Lecture Notes in Computer Science. Vol. 1007. doi:10.1007/3-540-60640-8. ISBN 978-3-540-60640-6. S2CID 12895857.
- ^ Dobbertin, Hans (December 1997). "RIPEMD with two-round compress function is not collision-free". Journal of Cryptology. 10 (1): 51–69. doi:10.1007/s001459900019. S2CID 15662054.
- ^ Bosselaers, Antoon. "The hash function RIPEMD-160".
- ^ Wang, Xiaoyun; Feng, Dengguo; Lai, Xuejia; Yu, Hongbo (2004-08-17). "Collisions for Hash Functions MD4, MD5, HAVAL-128 and RIPEMD". Cryptology ePrint Archive. Retrieved 2017-03-03.
- ^ Mendel, Florian; Pramstaller, Norbert; Rechberger, Christian; Rijmen, Vincent (2006). "On the Collision Resistance of RIPEMD-160". Information Security. Lecture Notes in Computer Science. Vol. 4176. pp. 101–116. doi:10.1007/11836810_8. ISBN 978-3-540-38341-3. Retrieved 2017-03-03.
- ^ Liu, Fukang; Dobraunig, Christoph; Mendel, Florian; Isobe, Takanori; Wang, Gaoli; Cao, Zhenfu (2019). "Efficient Collision Attack Frameworks for RIPEMD-160". In Alexandra Boldyreva; Daniele Micciancio (eds.). Advances in Cryptology – CRYPTO 2019, Proceesings vol 2. 39th Annual International Cryptology Conference, Santa Barbara, CA, USA, August 18–22, 2019. Lecture Notes in Computer Science. Vol. 11693. pp. 117–149. doi:10.1007/978-3-030-26951-7_5. ISBN 978-3-030-26950-0. S2CID 51860634.
- ^ Liu, Fukang; Wang, Gaoli; Sarkar, Santanu; Anand, Ravi; Meier, Willi; Li, Yingxin; Isobe, Takanori (February 2023). "Analysis of RIPEMD-160: New Collision Attacks and Finding Characteristics with MILP". In Carmit Hazay; Martijn Stam (eds.). Advances in Cryptology – EUROCRYPT 2023, Proceedings vol. 4. 42nd Annual International Conference on the Theory and Applications of Cryptographic Techniques, Lyon, France, April 23–27, 2023. Lecture Notes in Computer Science. Vol. 14007. pp. 189–219. doi:10.1007/978-3-031-30634-1_7. ISBN 978-3-031-30633-4. S2CID 257235244.
- ^ Li, Yingxin; Liu, Fukang; Wang, Gaoli (2023-12-08). "Automating Collision Attacks on RIPEMD-160". IACR Transactions on Symmetric Cryptology. 2023 (4): 112–142. doi:10.46586/tosc.v2023.i4.112-142. ISSN 2519-173X.
External links
[edit]RIPEMD
View on GrokipediaOverview
Definition and Purpose
RIPEMD is a family of cryptographic hash functions designed to produce a fixed-size output, typically 128 to 320 bits, from messages of arbitrary length, serving as one-way functions for secure message digestion.[3] These functions map input data to a compact digest that uniquely represents the original message without allowing easy reversal.[1] The primary purpose of RIPEMD in cryptography is to ensure data integrity by detecting unauthorized modifications, support message authentication through verifiable digests, and enable digital signatures by providing a secure basis for signing fixed-length values.[3] It resists key attacks including preimage (finding an input for a given output), second-preimage (finding a different input for the same output), and collision (finding two inputs with the same output) attacks, with security levels scaling to the output size, such as approximately 2^80 operations for collisions in 160-bit variants.[1] Key design goals for the RIPEMD family include providing a European-developed alternative to the MD4 and MD5 hash functions, with an emphasis on strong collision resistance and the avalanche effect, where even a single-bit change in the input produces a significantly different output (at least 50% bit flips on average).[3] The functions are deterministic, computationally efficient for software implementation on 32-bit processors, and maintain these properties across variants, with RIPEMD-160 being the most widely adopted for its balanced security and performance.[1]Family of Variants
The RIPEMD family encompasses several cryptographic hash functions designed primarily for message authentication and integrity verification, evolving from the original proposal to address emerging security needs. The original RIPEMD, introduced in 1992, produces a 128-bit output with an internal state of 128 bits (four 32-bit words), utilizing two parallel branches inspired by MD4 to enhance collision resistance. In 1996, strengthened variants were developed to mitigate identified weaknesses in the original design, including a plug-in replacement RIPEMD-128 with a 128-bit output and 128-bit internal state (four 32-bit words), and RIPEMD-160 with a 160-bit output and 160-bit internal state (five 32-bit words).[3] These updates incorporated refinements such as increased round counts and differentiated operations between branches. The family further includes RIPEMD-256 and RIPEMD-320, both proposed in 1996 as double-length extensions of RIPEMD-128 and RIPEMD-160, respectively, yielding 256-bit and 320-bit outputs with corresponding internal states of 256 bits and 320 bits to support applications requiring longer digests.[3] These variants were created to bolster security margins against brute-force attacks, where larger output sizes exponentially increase the effort required for preimage or collision searches, while maintaining compatibility with the core double-branch architecture.[3]| Variant | Output Size (bits) | Internal State Size (bits) | Publication Year | Primary Design Improvements |
|---|---|---|---|---|
| Original RIPEMD | 128 | 128 | 1992 | Parallel MD4-like branches with varied shifts and constants |
| RIPEMD-128 | 128 | 128 | 1996 | Plug-in strengthening with four rounds and refined message ordering[3] |
| RIPEMD-160 | 160 | 160 | 1996 | Five rounds, enhanced branch differences, and rotation mechanisms for added security[3] |
| RIPEMD-256 | 256 | 256 | 1996 | Double-length extension of RIPEMD-128 with register swapping for inter-branch interaction[3] |
| RIPEMD-320 | 320 | 320 | 1996 | Double-length extension of RIPEMD-160 with register swapping for inter-branch interaction[3] |
History
Development in the RIPE Project
The RIPE (RACE Integrity Primitives Evaluation) project was an initiative funded by the European Commission's RACE (Research and Development in Advanced Communications Technologies in Europe) program, running from 1988 to 1992, with the primary goal of developing a suite of cryptographic integrity primitives suitable for open networks, particularly the emerging Integrated Broadband Communication (IBC) systems.[7] This effort focused on creating secure mechanisms for data integrity, message authentication, and related functions, excluding confidentiality primitives, to foster interoperability and security in pan-European telecommunications infrastructure.[8] The consortium involved academic and industrial partners, including Katholieke Universiteit Leuven (KU Leuven), which played a central role in the design of hash functions.[7] Within this framework, the original RIPEMD (RIPE Message Digest) hash function emerged as a key output, designed by Antoon Bosselaers and Bart Preneel at KU Leuven. Hans Dobbertin later contributed to its cryptanalysis and the development of strengthened variants.[9] Proposed in 1992 as RIPEMD-0, it was structured as an enhanced variant of Ronald Rivest's MD4 algorithm, incorporating a 128-bit output length to provide robust collision resistance for practical applications.[10] The design emphasized software efficiency on 32-bit processors while addressing early vulnerabilities identified in MD4 through structural modifications, such as parallel processing lines.[9] The project's motivations were driven by concerns over the security of U.S.-developed hash functions like MD4 and the subsequent MD5, which had shown susceptibility to partial attacks, prompting a need for independent European alternatives.[11] RIPEMD was thus positioned as a European standard for integrity primitives, aiming to support secure information systems in distributed environments without relying on proprietary designs.[10] This initial version laid the groundwork for subsequent refinements within the RIPEMD family.[12]Evolution of Variants
Following the initial development of RIPEMD in 1992 as part of the European RACE Integrity Primitives Evaluation (RIPE) project, significant weaknesses were identified in its design by early 1995, prompting major revisions. Specifically, cryptanalyst Hans Dobbertin demonstrated collisions in the last two rounds of the original RIPEMD, exploiting similarities to the vulnerable MD4 hash function.[3] In response, Dobbertin, along with Antoon Bosselaers and Bart Preneel, introduced strengthened variants in 1996: RIPEMD-128, which retained a 128-bit output but added an extra round for improved resistance, and RIPEMD-160, which extended the output to 160 bits with five rounds total.[3] These revisions addressed the original's insufficient security margin against brute-force attacks, where a 128-bit hash could theoretically be collided in days using specialized hardware costing around $10 million.[3] A key evolutionary refinement in RIPEMD-160 was the enhancement of its parallel branch structure for superior diffusion of changes across the message digest. Unlike the original RIPEMD's more uniform parallel MD4-like branches, RIPEMD-160 incorporated distinct Boolean functions, shifted message word orders, and periodic exchanges of chaining variables between branches every round, making differential attacks significantly harder.[3] This design directly countered the early collision findings while maintaining compatibility with 32-bit processors for efficient implementation. RIPEMD-160 quickly gained traction as a secure alternative to MD5, influencing subsequent European cryptographic efforts by providing a model for parallel-branch hashes resistant to known MD-family vulnerabilities.[1] To accommodate emerging needs for longer hash outputs without proportionally increasing computational security requirements, RIPEMD-256 and RIPEMD-320 were introduced as double-length extensions of RIPEMD-128 and RIPEMD-160, respectively, in the same 1996 framework.[3] These variants apply the core compression function twice per block, with register swapping between iterations to ensure avalanche effects, targeting applications like digital signatures where 256- or 320-bit digests enhance collision resistance for larger key spaces.[1] Standardization efforts solidified the family's role in international cryptography. RIPEMD-160 and RIPEMD-128 were formally adopted in the ISO/IEC 10118-3 standard for dedicated hash functions in 2004, with revisions in 2018 confirming their specifications and object identifiers for interoperability. RIPEMD-256 received an object identifier from TeleTrusT.[13][1] This timeline reflected growing recognition of RIPEMD's contributions to secure hash design in Europe, bridging the gap between research prototypes and deployable standards.[1]Algorithm Design
General Structure
The RIPEMD family of cryptographic hash functions employs the Merkle-Damgård construction to process input messages securely. The overall process begins with padding the input message to a length that is a multiple of the 512-bit block size. This involves appending a single '1' bit, followed by sufficient '0' bits to reach 448 bits modulo 512, and concluding with a 64-bit little-endian representation of the original message length in bits. This ensures unambiguous recovery of the message length and prevents ambiguities in padding.[3] The hashing iteration initializes a set of chaining variables that maintain the intermediate state across blocks. Variants differ in state size: earlier ones like the original RIPEMD and RIPEMD-128 use four 32-bit words (A, B, C, D), while RIPEMD-160 and later use five (A, B, C, D, E). These are initialized to fixed constants derived from the fractional parts of the square roots of the first few prime numbers (√2, √3, etc.), scaled by and taken as integers. For example, in RIPEMD-160:- h0 = 0x67452301 (from √2)
- h1 = 0xefcdab89 (from √3)
- h2 = 0x98badcfe (from √5)
- h3 = 0x10325476 (from √7)
- h4 = 0xc3d2e1f0 (from √11)
RIPEMD-128 uses the first four of these. These "nothing-up-my-sleeve" constants provide a verifiable, non-arbitrary starting point to enhance trust in the design.[3][11]
Compression Function
The compression function in RIPEMD variants processes a 512-bit message block together with the current chaining variables (e.g., 128-bit for RIPEMD-128 or 160-bit for RIPEMD-160) to produce updated chaining variables of the same length, forming the core of the Merkle-Damgård construction used across the family.[15] This mechanism iteratively compresses the input message by incorporating block data and prior state through a series of bitwise and arithmetic operations designed for collision resistance.[3] The number of rounds varies by variant, with each round consisting of 16 steps (e.g., five rounds for 80 steps in RIPEMD-160).[15] Each round applies nonlinear Boolean functions operating on three 32-bit words x, y, z via bitwise operations to introduce nonlinearity. The functions differ by variant: earlier ones use f1 to f3 or f4; RIPEMD-160 uses five, denoted f1 to f5:[3]- f1(x, y, z) = x ⊕ y ⊕ z
- f2(x, y, z) = (x ∧ y) ∨ (¬x ∧ z)
- f3(x, y, z) = (x ∨ ¬y) ⊕ z
- f4(x, y, z) = (x ∧ z) ∨ (y ∧ ¬z)
- f5(x, y, z) = x ⊕ (y ∨ ¬z)
RIPEMD-160
Specifications
RIPEMD-160 produces a 160-bit hash value, represented as five 32-bit words, serving as the output from the final state of the compression function.[3] The algorithm initializes five 32-bit registers, denoted as A, B, C, D, and E, with the following hexadecimal constants:A = 0x67452301
B = 0xEFCDAB89
C = 0x98BADCFE
D = 0x10325476
E = 0xC3D2E1F0
These values are the same as the initial chaining variables used in MD5.[3] Message padding follows the MD4 convention: a single '1' bit is appended to the input message, followed by zero or more '0' bits to ensure the total length is congruent to 448 modulo 512 bits; then, the original message length in bits is appended as a 64-bit big-endian integer, making the padded message a multiple of 512 bits.[16] The compression function employs 80 steps divided into five rounds, with distinct constants for the left branch and for the right branch, applied across the steps to . These constants are selected as fractional parts of the square roots of prime numbers, scaled and truncated to 32 bits, and vary by round as shown in the table below:
| Step Range | Left Constant (hex) | Right Constant (hex) |
|---|---|---|
| 0–15 | 0x00000000 | 0x50A28BE6 |
| 16–31 | 0x5A827999 | 0x5C4DD124 |
| 32–47 | 0x6ED9EBA1 | 0x6D703EF3 |
| 48–63 | 0x8F1BBCDC | 0x7A6D76E9 |
| 64–79 | 0xA953FD4E | 0x00000000 |
| Step Range | Left Rotations | Right Rotations |
|---|---|---|
| 0–15 | 11,14,15,12,5,8,7,9,11,13,14,15,6,7,9,8 | 8,9,9,11,13,15,15,5,7,7,8,11,14,14,12,6 |
| 16–31 | 7,6,8,13,11,9,7,15,7,12,15,9,11,7,13,12 | 9,13,15,7,12,8,9,11,7,7,12,7,6,15,13,11 |
| 32–47 | 11,13,6,7,14,9,13,15,14,8,13,6,5,12,7,5 | 9,7,15,11,8,6,6,14,12,13,5,14,13,13,7,5 |
| 48–63 | 11,12,14,15,14,15,9,8,9,14,5,6,8,6,5,12 | 15,5,8,11,14,14,6,14,6,9,12,9,12,5,15,8 |
| 64–79 | 9,15,5,11,6,8,13,12,5,12,13,14,11,8,5,6 | 8,5,12,9,12,5,14,6,8,13,6,5,15,13,11,11 |
| Step Range | Left Indices | Right Indices |
|---|---|---|
| 0–15 | 0,1,2,3,4,5,6,7,8,9,10,11,12,13,14,15 | 5,14,7,0,9,2,11,4,13,6,15,8,1,10,3,12 |
| 16–31 | 7,4,13,1,10,6,15,3,12,0,9,5,2,14,11,8 | 6,11,3,7,0,13,5,10,14,15,8,12,4,9,1,2 |
| 32–47 | 3,10,14,4,9,15,8,1,2,7,0,6,13,11,5,12 | 15,5,1,3,7,14,6,9,11,8,12,2,10,0,4,13 |
| 48–63 | 1,9,11,10,0,8,12,4,13,3,7,15,14,5,6,2 | 8,6,4,1,3,11,15,0,5,12,2,13,9,7,10,14 |
| 64–79 | 4,0,5,9,7,12,2,10,14,1,3,8,11,6,15,13 | 12,9,15,5,0,4,8,6,2,7,13,1,3,10,11,14 |
Step-by-Step Process
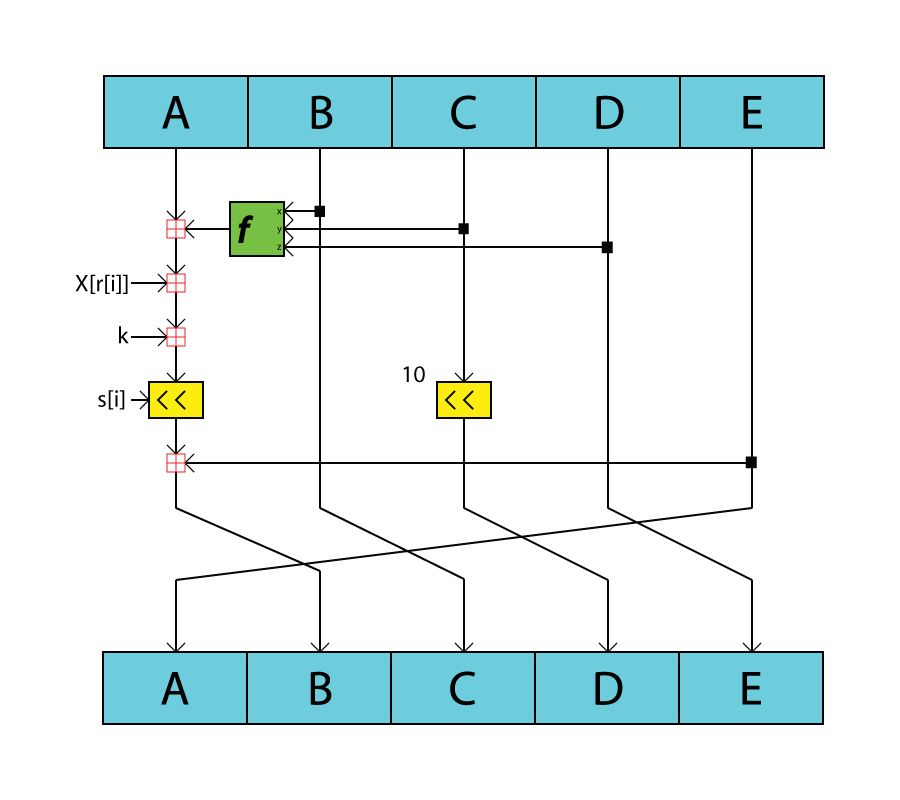
The preprocessing step in RIPEMD-160 pads the input message to ensure its length is a multiple of 512 bits, following the same method as MD4.[3] Specifically, a single '1' bit (represented as the byte 0x80) is appended to the message, followed by zero or more '0' bits until the total length modulo 512 equals 448 bits.[3] Then, the original message length in bits is appended as a 64-bit big-endian integer, resulting in a padded message divided into t blocks of 512 bits each, where each block comprises 16 32-bit words denoted X to X[17].[3] For example, an empty message of 0 bits is padded by appending 0x80, followed by 55 zero bytes (440 zero bits), making the total length 448 bits, and then eight zero bytes for the length, forming a single 512-bit block.[3] The computation begins by initializing five 32-bit chaining variables: h₀ = 0x67452301, h₁ = 0xEFCDAB89, h₂ = 0x98BADCFE, h₃ = 0x10325476, h₄ = 0xC3D2E1F0.[3] For each 512-bit message block Xᵢ, these chaining variables are copied to two sets of working variables for parallel processing: the left line (A = h₀, B = h₁, C = h₂, D = h₃, E = h₄) and the right line (A' = h₀, B' = h₁, C' = h₂, D' = h₃, E' = h₄).[3] Each line then performs 80 iterative steps, grouped into five rounds of 16 steps each (j = 0 to 79), where all operations are modulo 2³².[3] In each step j of the left line, a temporary value T is computed aswhere denotes a left rotation by s bits, is the round-dependent nonlinear function, selects the message word index, and is the round constant; the working variables are then updated as A ← E, E ← D, D ← , C ← B, B ← T.[3] The right line follows an analogous process but applies the nonlinear functions in reverse order (f5 to f1 across the five rounds):
followed by A' ← E', E' ← D', D' ← , C' ← B', B' ← T', with distinct , , and .[3] The nonlinear functions , rotation amounts and , message word orders and , and constants and are predefined per round as specified in the RIPEMD-160 parameters.[3] After completing the 80 steps, the final working variables from both lines are combined to update the chaining variables as follows:
h₀ ← h₁ + C + D',
h₁ ← h₂ + D + E',
h₂ ← h₃ + E + A',
h₃ ← h₄ + A + B',
h₄ ← h₀ + B + C'.[3] This updated 160-bit chaining value (concatenation of h₀ to h₄) is fed as input to the next block, and after all blocks are processed, it forms the final hash output.[3] The following pseudocode outlines the compression function for a single 512-bit block:
procedure RIPEMD160_Compress(h0, h1, h2, h3, h4, X[0..15])
// Copy chaining vars to left and right lines
A = h0; B = h1; C = h2; D = h3; E = h4
A_ = h0; B_ = h1; C_ = h2; D_ = h3; E_ = h4 // Right line with prime notation
for j = 0 to 79 do
// Left line step
if j < 16 then
f = B xor C xor D
K = 0x00000000
s = s_left[j]
r_idx = r_left[j]
else if j < 32 then
f = (B and C) or (not B and D)
K = 0x5A827999
s = s_left[j]
r_idx = r_left[j]
else if j < 48 then
f = (B or not C) xor D
K = 0x6ED9EBA1
s = s_left[j]
r_idx = r_left[j]
else if j < 64 then
f = (B and D) or (C and not D)
K = 0x8F1BBCDC
s = s_left[j]
r_idx = r_left[j]
else
f = B xor (C or not D)
K = 0xA953FD4E
s = s_left[j]
r_idx = r_left[j]
T = rol_s(A + f + X[r_idx] + K) + E
A = E; E = D; D = rol_10(C); C = B; B = T
// Right line step (reversed rounds)
if j < 16 then
f_ = B_ xor (C_ or not D_)
K_ = 0x50A28BE6
s_ = s_right[j]
r_idx_ = r_right[j]
else if j < 32 then
f_ = (B_ and D_) or (C_ and not D_)
K_ = 0x5C4DD124
s_ = s_right[j]
r_idx_ = r_right[j]
else if j < 48 then
f_ = (B_ or not C_) xor D_
K_ = 0x6D703EF3
s_ = s_right[j]
r_idx_ = r_right[j]
else if j < 64 then
f_ = (B_ and C_) or (not B_ and D_)
K_ = 0x7A6D76E9
s_ = s_right[j]
r_idx_ = r_right[j]
else
f_ = B_ xor C_ xor D_
K_ = 0x00000000
s_ = s_right[j]
r_idx_ = r_right[j]
T_ = rol_{s_}(A_ + f_ + X[r_idx_] + K_) + E_
A_ = E_; E_ = D_; D_ = rol_10(C_); C_ = B_; B_ = T_
// Finalization: Update chaining variables
h0 = h1 + C + D_
h1 = h2 + D + E_
h2 = h3 + E + A_
h3 = h4 + A + B_
h4 = h0 + B + C_
return (h0, h1, h2, h3, h4)
procedure RIPEMD160_Compress(h0, h1, h2, h3, h4, X[0..15])
// Copy chaining vars to left and right lines
A = h0; B = h1; C = h2; D = h3; E = h4
A_ = h0; B_ = h1; C_ = h2; D_ = h3; E_ = h4 // Right line with prime notation
for j = 0 to 79 do
// Left line step
if j < 16 then
f = B xor C xor D
K = 0x00000000
s = s_left[j]
r_idx = r_left[j]
else if j < 32 then
f = (B and C) or (not B and D)
K = 0x5A827999
s = s_left[j]
r_idx = r_left[j]
else if j < 48 then
f = (B or not C) xor D
K = 0x6ED9EBA1
s = s_left[j]
r_idx = r_left[j]
else if j < 64 then
f = (B and D) or (C and not D)
K = 0x8F1BBCDC
s = s_left[j]
r_idx = r_left[j]
else
f = B xor (C or not D)
K = 0xA953FD4E
s = s_left[j]
r_idx = r_left[j]
T = rol_s(A + f + X[r_idx] + K) + E
A = E; E = D; D = rol_10(C); C = B; B = T
// Right line step (reversed rounds)
if j < 16 then
f_ = B_ xor (C_ or not D_)
K_ = 0x50A28BE6
s_ = s_right[j]
r_idx_ = r_right[j]
else if j < 32 then
f_ = (B_ and D_) or (C_ and not D_)
K_ = 0x5C4DD124
s_ = s_right[j]
r_idx_ = r_right[j]
else if j < 48 then
f_ = (B_ or not C_) xor D_
K_ = 0x6D703EF3
s_ = s_right[j]
r_idx_ = r_right[j]
else if j < 64 then
f_ = (B_ and C_) or (not B_ and D_)
K_ = 0x7A6D76E9
s_ = s_right[j]
r_idx_ = r_right[j]
else
f_ = B_ xor C_ xor D_
K_ = 0x00000000
s_ = s_right[j]
r_idx_ = r_right[j]
T_ = rol_{s_}(A_ + f_ + X[r_idx_] + K_) + E_
A_ = E_; E_ = D_; D_ = rol_10(C_); C_ = B_; B_ = T_
// Finalization: Update chaining variables
h0 = h1 + C + D_
h1 = h2 + D + E_
h2 = h3 + E + A_
h3 = h4 + A + B_
h4 = h0 + B + C_
return (h0, h1, h2, h3, h4)
Security Analysis
Known Weaknesses and Attacks
The original RIPEMD hash function, proposed in 1992, was found to have significant weaknesses shortly after its publication. Hans Dobbertin demonstrated a collision attack on the reduced two-round version of its compression function, achieving collisions with a complexity of approximately hash computations, which highlighted structural vulnerabilities in the design and prompted the development of strengthened variants like RIPEMD-160. This attack exploited differential paths in the MD4-like structure, revealing that the parallel branch design did not sufficiently mitigate propagation of differences, though it did not directly break the full three-round function in practical time. For RIPEMD-160, cryptanalytic efforts have focused on reduced-round variants, with no practical full collisions known as of 2025. In 2013, researchers presented a semi-free-start collision attack on 36 steps (out of 80) starting from the first step, with a practical time complexity of compression function evaluations, using advanced differential path searches and message modification techniques tailored to the dual-branch architecture.[18] This result demonstrated vulnerabilities in the early rounds but remained far from threatening the full function, as the complexity exceeds brute-force bounds only for the reduced version. Subsequent improvements in 2023 achieved a collision attack on 36 steps with time complexity , and a practical collision on 40 steps (found in 16 hours using 115 threads), using MILP to optimize differential characteristics and SAT/SMT solvers for message pair finding.[19][20] In 2025, further advances presented semi-free-start collision attacks on up to 44 steps with complexity , including practical attacks on 41 steps () and 42 steps (), employing enhanced automatic search models, differential clustering, and dedicated message modification techniques.[4] These advances underscore ongoing concerns about the function's long-term security margin, though full collisions remain infeasible with current computational resources. Among other variants, RIPEMD-128 has been subjected to a pseudo-preimage attack on a 36-step reduced version with complexity , and a preimage attack with , leveraging meet-in-the-middle techniques on the double-branch structure to find messages mapping to the same hash value more efficiently than generic bounds.[17] In contrast, RIPEMD-256 and RIPEMD-320 have withstood significant cryptanalysis and remain unbroken against practical collision or preimage attacks as of 2025, owing to their larger output sizes and enhanced round structures. Overall, while RIPEMD-160 resists practical full attacks, its age and the incremental progress in reduced-round cryptanalysis have led to recommendations against its use in new cryptographic systems, favoring modern alternatives with stronger proven security.[1]Comparison with Other Hash Functions
RIPEMD, developed as a European successor to the MD4 hash function, was designed to address vulnerabilities in the MD family, particularly MD5. While MD5, with its 128-bit output, succumbed to practical collision attacks with a complexity of approximately operations as demonstrated by Wang et al. in 2004, RIPEMD-160 provides stronger resistance, maintaining its full 160-bit collision security at the birthday bound of without known practical breaks. This makes RIPEMD-160 a more robust alternative for legacy systems requiring 160-bit hashes, though its design emphasizes parallel processing of two streams to enhance security margins over MD5's sequential approach.[22][1] In comparison to the SHA family, RIPEMD-160 offers comparable output length to SHA-1 but superior practical security, as SHA-1 has been compromised with collisions achievable at complexity via differential cryptanalysis by Wang et al. in 2005, leading to its deprecation. SHA-256, with a 256-bit output, achieves a higher collision resistance of , making it preferable for modern applications demanding long-term security. RIPEMD-160's 160-bit design thus provides security, which is adequate for many uses but inferior to SHA-256 or SHA-512's level against brute-force threats.[23] Performance-wise, RIPEMD-160 is slower than SHA-1 on 32-bit systems, requiring about 1013 cycles per 512-bit block compared to SHA-1's 837 cycles on a Pentium processor, due to its dual-line computation. However, it outperforms SHA-512 on the same architecture, as SHA-512's 64-bit word operations incur overhead on 32-bit hardware, often doubling or tripling cycle counts relative to 32-bit-optimized hashes like RIPEMD-160. As of 2025, RIPEMD-160 remains in legacy adoption, notably for Bitcoin address generation alongside SHA-256, while SHA-1 faces full phase-out by 2030 per NIST guidelines, and SHA-2/SHA-3 variants are recommended for new deployments.[1][24]| Hash Function | Collision Resistance | Relative Speed (32-bit Systems) | Adoption Status (2025) |
|---|---|---|---|
| MD5 | Broken () | Fastest | Deprecated |
| RIPEMD-160 | Medium (1013 cycles/block) | Legacy (e.g., Bitcoin) | |
| SHA-1 | Broken () | Faster than RIPEMD-160 (837 cycles/block) | Deprecated (phase-out by 2030) |
| SHA-256 | Fast | Widely used | |
| SHA-512 | Slow (64-bit overhead) | Widely used |
Applications
Cryptographic Uses
RIPEMD-160 has been employed in digital signature schemes for message authentication, particularly within the OpenPGP protocol for creating and verifying signatures on electronic messages and files.[25] Although newer implementations discourage its use for new signatures due to security considerations, it remains supported for compatibility in tools like GnuPG that handle legacy PGP keys.[26] In X.509 certificate infrastructures, RIPEMD-160 has been utilized to hash certificate data before signing with algorithms such as RSA, appearing in some end-entity certificates for authentication in public key infrastructures.[27][28] A prominent application of RIPEMD-160 persists in blockchain technology, where it is integral to Bitcoin's address generation process. To derive a Bitcoin address, the public key is first hashed with SHA-256, and the resulting 256-bit digest is then processed through RIPEMD-160 to produce a 160-bit hash, which is further encoded with versioning and checksums to form the final address.[19] This double-hashing approach enhances security by combining the strengths of both functions, and RIPEMD-160's role remains unchanged in Bitcoin's protocol as of 2025, supporting the network's ongoing operations. In other protocols, RIPEMD-160 provides legacy support for cryptographic operations, such as in older SSL/TLS implementations where it could be selected as a hash function for handshake integrity, though modern configurations favor SHA-based alternatives via providers like OpenSSL's legacy module. For file integrity verification, Unix-like systems leverage RIPEMD-160 through command-line tools like OpenSSL'sdgst -ripemd160 to compute checksums, ensuring data has not been altered during transfer or storage.[29] However, its adoption has declined broadly following NIST recommendations to prioritize the SHA-2 and SHA-3 families for approved cryptographic hash functions, citing their standardized security profiles over non-FIPS options like RIPEMD-160.[30]
RIPEMD-160 finds continued niche applications in resource-constrained environments, such as smart cards and embedded systems, where its 160-bit output provides adequate security for legacy-compatible authentication while minimizing computational overhead compared to longer-hash alternatives. These deployments often pair it with hardware accelerators optimized for its parallel structure, suitable for scenarios like payment token verification or device firmware signing where 160-bit collision resistance suffices.[31]
Software Implementations
RIPEMD-160 implementations are available in several prominent open-source cryptographic libraries, enabling integration into various software projects for legacy or specific use cases. The OpenSSL library provides support for RIPEMD-160 through its EVP_MD API, though in version 3.0 and later, it is included in the legacy provider rather than the default one, requiring explicit loading for use.[32][33] Bouncy Castle, a widely used library for Java and .NET environments, offers comprehensive RIPEMD-160 support via its provider classes, including digest computation and integration with JCA/JCE standards.[34][35] Similarly, the Crypto++ C++ library includes a dedicated RIPEMD160 class for efficient message digest computation, supporting 160-bit output as part of its hash function suite.[36] Language-specific support for RIPEMD-160 is provided through standard or extended cryptographic APIs, often relying on underlying libraries like those mentioned above. In Python, the hashlib module allows creation of RIPEMD-160 hashes usinghashlib.new('ripemd160'), though availability depends on the system's OpenSSL configuration, as newer versions (3.0+) may disable it by default. For example:
import hashlib
data = b"Hello, RIPEMD-160!"
h = hashlib.new('ripemd160')
h.update(data)
digest = h.hexdigest()
print(digest) # Outputs the 40-character hex digest
import hashlib
data = b"Hello, RIPEMD-160!"
h = hashlib.new('ripemd160')
h.update(data)
digest = h.hexdigest()
print(digest) # Outputs the 40-character hex digest
java.security.MessageDigest.getInstance("RIPEMD160"), but this typically requires a third-party provider like Bouncy Castle, as it is not natively included in the JDK.[37] A basic usage example with Bouncy Castle registered is:
import java.security.MessageDigest;
import org.bouncycastle.jce.provider.BouncyCastleProvider;
import java.security.Security;
Security.addProvider(new BouncyCastleProvider());
MessageDigest md = MessageDigest.getInstance("RIPEMD160");
md.update("Hello, RIPEMD-160!".getBytes());
byte[] digest = md.digest();
System.out.println(bytesToHex(digest)); // Custom method to convert to hex
import java.security.MessageDigest;
import org.bouncycastle.jce.provider.BouncyCastleProvider;
import java.security.Security;
Security.addProvider(new BouncyCastleProvider());
MessageDigest md = MessageDigest.getInstance("RIPEMD160");
md.update("Hello, RIPEMD-160!".getBytes());
byte[] digest = md.digest();
System.out.println(bytesToHex(digest)); // Custom method to convert to hex
References
- A pseudo-preimage and second preimage attacks on the first 47 steps of RIPEMD (full version: 48 steps) are proposed with complexities of 2119 and 2124.5 ...