Recent from talks
Nothing was collected or created yet.
X.509
View on Wikipedia| X.509 | |
|---|---|
| Information technology - Open Systems Interconnection - The Directory: Public-key and attribute certificate frameworks | |
| Status | In force (Recommendation) |
| First published | 1.0 at November 25, 1988 |
| Latest version | 9.2 October 29, 2023 |
| Organization | ITU-T |
| Committee | ITU-T Study Group 17 |
| Series | X |
| Base standards | ASN.1 |
| Related standards | ISO/IEC 9594-8:2020, X.500 |
| Domain | Cryptography |
| Website | www |
In cryptography, X.509 is an International Telecommunication Union (ITU) standard defining the format of public key certificates.[1] X.509 certificates are used in many Internet protocols, including TLS/SSL, which is the basis for HTTPS,[2] the secure protocol for browsing the web. They are also used in offline applications, like electronic signatures.[3]
An X.509 certificate binds an identity to a public key using a digital signature. A certificate contains an identity (a hostname, or an organization, or an individual) and a public key (RSA, DSA, ECDSA, ed25519, etc.), and is either signed by a certificate authority or is self-signed. When a certificate is signed by a trusted certificate authority, or validated by other means, someone holding that certificate can use the public key it contains to establish secure communications with another party, or validate documents digitally signed by the corresponding private key.
X.509 also defines certificate revocation lists, which are a means to distribute information about certificates that have been deemed invalid by a signing authority, as well as a certification path validation algorithm, which allows for certificates to be signed by intermediate CA certificates, which are, in turn, signed by other certificates, eventually reaching a trust anchor.
X.509 is defined by the ITU's "Standardization Sector" (ITU-T's SG17), in ITU-T Study Group 17 and is based on Abstract Syntax Notation One (ASN.1), another ITU-T standard.
History and usage
[edit]X.509 was initially issued on July 3, 1988, and was begun in association with the X.500 standard. The first tasks of it was providing users with secure access to information resources and avoiding a cryptographic man-in-the-middle attack. It assumes a strict hierarchical system of certificate authorities (CAs) for issuing the certificates. This contrasts with web of trust models, like PGP, where anyone (not just special CAs) may sign and thus attest to the validity of others' key certificates.
Version 3 of X.509 includes the flexibility to support other topologies like bridges and meshes.[2] It can be used in a peer-to-peer, OpenPGP-like web of trust,[citation needed] but was rarely used that way as of 2004[update]. The X.500 system has only been implemented by sovereign nations[which?] for state identity information sharing treaty fulfillment purposes, and the IETF's Public-Key Infrastructure (X.509) (PKIX) working group has adapted the standard to the more flexible organization of the Internet. In fact, the term X.509 certificate usually refers to the IETF's PKIX certificate and CRL profile of the X.509 v3 certificate standard, as specified in RFC 5280, commonly called PKIX for Public Key Infrastructure (X.509).[4]
An early issue with Public Key Infrastructure (PKI) and X.509 certificates was the well known "which directory" problem. The problem is the client does not know where to fetch missing intermediate certificates because the global X.500 directory never materialized. The problem was mitigated by including all intermediate certificates in a request. For example, early web servers only sent the web server's certificate to the client. Clients that lacked an intermediate CA certificate or where to find them failed to build a valid path from the CA to the server's certificate. To work around the problem, web servers now send all the intermediate certificates along with the web server's certificate.[5]
While PKIX refers to the IETF's or Internet's PKI standard, there are many other PKIs with different policies. For example, the US Government has its own PKI with its own policies, and the CA/Browser Forum has its own PKI with its own policies. The US Government's PKI is a massive book of over 2500 pages. If an organization's PKI diverges too much from that of the IETF or CA/Browser Forum, then the organization risks losing interoperability with common tools like web browsers, cURL, and Wget. For example, if a PKI has a policy of only issuing certificates on Monday, then common tools like cURL and Wget will not enforce the policy and allow a certificate issued on a Tuesday.[5]
Certificates
[edit]| X.509 certificate | |
|---|---|
| Internet media type |
application/pkix-cert[6] |
| Uniform Type Identifier (UTI) | public.x509-certificate[7] |
X.509 certificates bind an identity to a public key using a digital signature. In the X.509 system, there are two types of certificates. The first is a CA certificate. The second is an end-entity certificate. A CA certificate can issue other certificates. The top level, self-signed CA certificate is sometimes called the Root CA certificate. Other CA certificates are called intermediate CA or subordinate CA certificates. An end-entity certificate identifies the user, like a person, organization or business. An end-entity certificate cannot issue other certificates. An end-entity certificate is sometimes called a leaf certificate since no other certificates can be issued below it.
An organization that wants a signed certificate requests one from a CA using a protocol like Certificate Signing Request (CSR), Simple Certificate Enrollment Protocol (SCEP) or Certificate Management Protocol (CMP). The organization first generates a key pair, keeping the private key secret and using it to sign the CSR. The CSR contains information identifying the applicant and the applicant's public key that is used to verify the signature of the CSR - and the Distinguished Name (DN) that is unique for the person, organization or business. The CSR may be accompanied by other credentials or proofs of identity required by the certificate authority.
The CSR will be validated using a Registration Authority (RA), and then the certification authority will issue a certificate binding a public key to a particular distinguished name. The roles registration authority and certification authority are usually separate business units under separation of duties to reduce the risk of fraud.
An organization's trusted root certificates can be distributed to all employees so that they can use the company PKI system. Browsers such as Internet Explorer, Firefox, Opera, Safari and Chrome come with a predetermined set of root certificates pre-installed, so SSL certificates from major certificate authorities will work instantly; in effect the browsers' developers determine which CAs are trusted third parties for the browsers' users. For example, Firefox provides a CSV and/or HTML file containing a list of Included CAs.[8]
X.509 and RFC 5280 also include standards for certificate revocation list (CRL) implementations. Another IETF-approved way of checking a certificate's validity is the Online Certificate Status Protocol (OCSP). Firefox 3.0 enabled OCSP checking by default, as did versions of Windows from at least Vista and later.[9]
Structure of a certificate
[edit]The structure foreseen by the standards is expressed in a formal language, Abstract Syntax Notation One (ASN.1).
The structure of an X.509 v3 digital certificate is as follows:
- Certificate
- Version Number
- Serial Number
- Signature Algorithm ID
- Issuer Name
- Validity period
- Not Before
- Not After
- Subject name
- Subject Public Key Info
- Public Key Algorithm
- Subject Public Key
- Issuer Unique Identifier (optional)
- Subject Unique Identifier (optional)
- Extensions (optional)
- ...
- Certificate Signature Algorithm
- Certificate Signature
The Extensions field, if present, is a sequence of one or more certificate extensions.[10]: §4.1.2.9: Extensions Each extension has its own unique ID, expressed as object identifier (OID), which is a set of values, together with either a critical or non-critical indication. A certificate-using system must reject the certificate if it encounters a critical extension that it does not recognize, or a critical extension that contains information that it cannot process. A non-critical extension may be ignored if it is not recognized, but must be processed if it is recognized.[10]: §4.2: Certificate Extensions
The structure of version 1 is given in RFC 1422.
The inner format of issuer and subject unique identifiers specified in X.520 The Directory: Selected attribute types recommendation.
ITU-T introduced issuer and subject unique identifiers in version 2 to permit the reuse of issuer or subject name after some time. An example of reuse will be when a CA goes bankrupt and its name is deleted from the country's public list. After some time another CA with the same name may register itself, even though it is unrelated to the first one. However, IETF recommends that no issuer and subject names be reused. Therefore, version 2 is not widely deployed in the Internet.[citation needed]
Extensions were introduced in version 3. A CA can use extensions to issue a certificate only for a specific purpose (e.g. only for signing digital objects).
In all versions, the serial number must be unique for each certificate issued by a specific CA (as mentioned in RFC 5280).
Extensions informing a specific usage of a certificate
[edit]RFC 5280 (and its predecessors) defines a number of certificate extensions which indicate how the certificate should be used. Most of them are arcs from the joint-iso-ccitt(2) ds(5) id-ce(29) OID. Some of the most common, defined in section 4.2.1, are:
- Basic Constraints,
{ id-ce 19 },[10]: §4.2.1.9 are used to indicate whether the certificate is a CA certificate and can certify or issue other certificates. A constraint can be marked as critical. If a constraint is marked critical, then an agent must fail to process the certificate if the agent does not understand the constraint. An agent can continue to process a non-critical constraint it does not understand. - Key Usage,
{ id-ce 15 },[10]: §4.2.1.3 provides a bitmap specifying the cryptographic operations which may be performed using the public key contained in the certificate; for example, it could indicate that the key should be used for signatures but not for encipherment. - Extended Key Usage,
{ id-ce 37 },[10]: §4.2.1.12 is used, typically on a leaf certificate, to indicate the purpose of the public key contained in the certificate. It contains a list of OIDs, each of which indicates an allowed use. For example,{ id-pkix 3 1 }indicates that the key may be used on the server end of a TLS or SSL connection;{ id-pkix 3 4 }indicates that the key may be used to secure email.
In general when using RFC 5280, if a certificate has several extensions restricting its use, all restrictions must be satisfied for a given use to be appropriate. The RFC gives the specific example of a certificate containing both keyUsage and extendedKeyUsage: in this case, both must be processed and the certificate can only be used if both extensions are coherent in specifying the usage of a certificate. For example, NSS uses both extensions to specify certificate usage.[11]
Extended Validation certificates
[edit]Certification authorities operating under the CA/Browser Forum's PKI issue certificates with varying levels of validation. The different validations provide different levels of assurances that a certificate represents what it is supposed to. For example, a web server can be validated at the lowest level of assurances using an email called Domain Validation (DV). Or a web server can be validated at a higher level of assurances using more detailed methods called Extended Validation (EV).
In practice, a DV certificate means a certificate was issued for a domain like example.com after control over that domain was asserted, e.g. by responding to an email sent to webmaster@example.com. An EV certificate means a certificate was issued for a domain like example.com, and a company like Example, LLC is the owner of the domain, and the owner was verified by Articles of Incorporation.
Extended validation does not add any additional security controls, so the secure channel setup using an EV certificate is not "stronger" than a channel setup using a different level of validation like DV.
Extended validation is signaled in a certificate using X.509 v3 extension. Each CA uses a different Object Identifier (OID) to assert extended validation. There is no single OID to indicate extended validation, which complicates user agent programming. Each user agent must have a list of OIDs that indicate extended validation.
The CA/Browser Forum's PKI recognizes extended validation. Other PKIs, like the Internet's PKI (PKIX), do not place any special emphasis on extended validation. Tools using PKIX policies, like cURL and Wget, simply treat an EV certificate like any other certificate. Until 2019, many browsers used to provide strong visual feedback in the URL bar to the user to indicate a site provides an EV certificate. Following studies and reports that showed the ineffectiveness of EV certificates and their utility to criminals for injecting misleading elements into the central part of the browser's UI, all major browsers removed their previous prominent visual feedback from the URL bar.[12] [13] [14] Instead, since 2019, browsers such as Chromium and Firefox hide the EV issued-to information in sub-menus, where it is displayed in a neutral way, without any highlighting or mentioning of extended validation.
Security expert Peter Gutmann states CA's created EV certificates to restore profit levels after the Race to the Bottom cut into profits. During the race to the bottom CA's cut prices to lure consumers to purchase their certificates. As a result, profits were reduced and CA's dropped the level of validation they were performing to the point there were nearly no assurances on a certificate.[5]
Certificate filename extensions
[edit]There are several commonly used filename extensions for X.509 certificates. Some of these extensions are also used for other data such as private keys.
.pem– (Privacy-enhanced Electronic Mail) Base64 encoded DER certificate, enclosed between-----BEGIN CERTIFICATE-----and-----END CERTIFICATE-----.cer,.crt,.der– usually in binary DER form, but Base64-encoded certificates are common too (see.pemabove).p8,.p8e,.pk8– exported private key as specified in PKCS#8. May be in DER or PEM form that starts with-----BEGIN PRIVATE KEY-----. The encrypted key starts with-----BEGIN ENCRYPTED PRIVATE KEY-----and may have the.p8eextension..p10,.csr– PKCS#10 a certificate signing request (CSR). In PEM form starts with-----BEGIN CERTIFICATE REQUEST-----. These are generated for submission to certificate-authorities (CA). It includes key details of the requested certificate such as Common Name (/CN), subject, organization, state, country, as well as the public key of the certificate to get signed. These get signed by the CA and a certificate is returned. The returned certificate is the public certificate (which includes the public key but not the private key), which itself can be in a couple of formats but usually in.p7r.[15].p7r– PKCS#7 response to CSR. Contains the newly signed certificate, and the CA's own cert..p7s– PKCS#7 Digital Signature. May contain the original signed file or message. Used in S/MIME for email signing. Defined in RFC 2311..p7m– PKCS#7 (SignedData, EnvelopedData) Message e.g. encrypted ("enveloped") file, message or MIME email letter. Defined in RFC 2311..p7c– PKCS#7 degenerated SignedData "certs-only" structure, without any data to sign. Defined in RFC 2311..p7b,.keystore– PKCS#7 SignedData structure without data, just certificate(s) bundle and/or CRLs (rarely) but not a private key. Uses DER form or BER or PEM that starts with-----BEGIN PKCS7-----. The format used by Windows for certificate interchange. Supported by Java but often has.keystoreas an extension instead. Unlike.pemstyle certificates, this format has a defined way to include certification-path certificates..p12,.pfx,.pkcs12– PKCS#12, may contain certificate(s) (public) and private keys (password protected) in a single file..pfx– Personal Information eXchange PFX, predecessor of PKCS#12 (usually contains data in PKCS#12 format, e.g. with PFX files generated in IIS)..crl– A Certificate Revocation List (CRL). Certificate Authorities produce these as a way to de-authorize certificates before expiration.
PKCS#7 is a standard for signing or encrypting (officially called "enveloping") data. Since the certificate is needed to verify signed data, it is possible to include them in the SignedData structure.
Certificate chains and cross-certification
[edit]A certificate chain (also known as a "certification path"[10]: §3.2 ) is a list of certificates (usually starting with an end-entity certificate) followed by one or more CA certificates (usually the last one being a self-signed certificate), with the following properties:
- The Issuer of each certificate (except the last one) matches the Subject of the next certificate in the list.
- Each certificate (except the last one) is signed by the secret key corresponding to the next certificate in the chain (i.e. the signature of one certificate can be verified using the public key contained in the following certificate).
- The last certificate in the list is a trust anchor: a certificate that you trust because it was delivered to you by some trustworthy procedure.
Certificate chains are used in order to check that the public key (PK) contained in a target certificate (the first certificate in the chain) and other data contained in it effectively belongs to its subject. In order to ascertain this, the signature on the target certificate is verified by using the PK contained in the following certificate, whose signature is verified using the next certificate, and so on until the last certificate in the chain is reached. As the last certificate is a trust anchor, successfully reaching it will prove that the target certificate can be trusted.
The description in the preceding paragraph is a simplified view on the certification path validation process,[10]: §6 which involves additional checks, such as verifying validity dates on certificates, looking up CRLs, etc.

Examining how certificate chains are built and validated, it is important to note that a concrete certificate can be part of very different certificate chains (all of them valid). This is because several CA certificates can be generated for the same subject and public key, but be signed with different private keys (from different CAs or different private keys from the same CA). So, although a single X.509 certificate can have only one issuer and one CA signature, it can be validly linked to more than one certificate, building completely different certificate chains. This is crucial for cross-certification between PKIs and other applications.[16] See the following examples:
Examples
[edit]In these diagrams:
- Each box represents a certificate, with its Subject in bold.
- A → B means "A is signed by B" (or, more precisely, "A is signed by the secret key corresponding to the public key contained in B").
- Certificates with the same color (that are not white/transparent) contain the same public key.
Example 1: Cross-certification at root Certification Authority (CA) level between two PKIs
[edit]In order to manage that user certificates existing in PKI 2 (like "User 2") are trusted by PKI 1, CA1 generates a certificate (cert2.1) containing the public key of CA2.[17] Now both "cert2 and cert2.1 (in green) have the same subject and public key, so there are two valid chains for cert2.2 (User 2): "cert2.2 → cert2" and "cert2.2 → cert2.1 → cert1".
Similarly, CA2 can generate a certificate (cert1.1) containing the public key of CA1 so that user certificates existing in PKI 1 (like "User 1") are trusted by PKI 2.
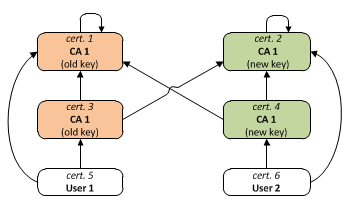
Example 2: CA certificate renewal
[edit]Understanding Certification Path Construction (PDF). PKI Forum. September 2002. Archived from the original (PDF) on 2019-02-04. Retrieved 2014-11-07. To allow for graceful transition from the old signing key pair to the new signing key pair, the CA should issue a certificate that contains the old public key signed by the new private signing key and a certificate that contains the new public key signed by the old private signing key. Both of these certificates are self-issued, but neither is self-signed. Note that these are in addition to the two self-signed certificates (one old, one new).
Since both cert1 and cert3 contain the same public key (the old one), there are two valid certificate chains for cert5: "cert5 → cert1" and "cert5 → cert3 → cert2", and analogously for cert6. This allows that old user certificates (such as cert5) and new certificates (such as cert6) can be trusted indifferently by a party having either the new root CA certificate or the old one as trust anchor during the transition to the new CA keys.[18]
Sample X.509 certificates
[edit]This is an example of a decoded X.509 certificate that was used in the past by wikipedia.org and several other Wikipedia websites. It was issued by GlobalSign, as stated in the Issuer field. Its Subject field describes Wikipedia as an organization, and its Subject Alternative Name (SAN) field for DNS describes the hostnames for which it could be used. The Subject Public Key Info field contains an ECDSA public key, while the signature at the bottom was generated by GlobalSign's RSA private key. (The signatures in these examples are truncated.)
End-entity certificate
[edit]Certificate:
Data:
Version: 3 (0x2)
Serial Number:
10:e6:fc:62:b7:41:8a:d5:00:5e:45:b6
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=BE, O=GlobalSign nv-sa, CN=GlobalSign Organization Validation CA - SHA256 - G2
Validity
Not Before: Nov 21 08:00:00 2016 GMT
Not After : Nov 22 07:59:59 2017 GMT
Subject: C=US, ST=California, L=San Francisco, O=Wikimedia Foundation, Inc., CN=*.wikipedia.org
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
00:c9:22:69:31:8a:d6:6c:ea:da:c3:7f:2c:ac:a5:
af:c0:02:ea:81:cb:65:b9:fd:0c:6d:46:5b:c9:1e:
9d:3b:ef
ASN1 OID: prime256v1
NIST CURVE: P-256
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Agreement
Authority Information Access:
CA Issuers - URI:http://secure.globalsign.com/cacert/gsorganizationvalsha2g2r1.crt
OCSP - URI:http://ocsp2.globalsign.com/gsorganizationvalsha2g2
X509v3 Certificate Policies:
Policy: 1.3.6.1.4.1.4146.1.20
CPS: https://www.globalsign.com/repository/
Policy: 2.23.140.1.2.2
X509v3 Basic Constraints:
CA:FALSE
X509v3 CRL Distribution Points:
Full Name:
URI:http://crl.globalsign.com/gs/gsorganizationvalsha2g2.crl
X509v3 Subject Alternative Name:
DNS:*.wikipedia.org, DNS:*.m.mediawiki.org, DNS:*.m.wikibooks.org, DNS:*.m.wikidata.org, DNS:*.m.wikimedia.org, DNS:*.m.wikimediafoundation.org, DNS:*.m.wikinews.org, DNS:*.m.wikipedia.org, DNS:*.m.wikiquote.org, DNS:*.m.wikisource.org, DNS:*.m.wikiversity.org, DNS:*.m.wikivoyage.org, DNS:*.m.wiktionary.org, DNS:*.mediawiki.org, DNS:*.planet.wikimedia.org, DNS:*.wikibooks.org, DNS:*.wikidata.org, DNS:*.wikimedia.org, DNS:*.wikimediafoundation.org, DNS:*.wikinews.org, DNS:*.wikiquote.org, DNS:*.wikisource.org, DNS:*.wikiversity.org, DNS:*.wikivoyage.org, DNS:*.wiktionary.org, DNS:*.wmfusercontent.org, DNS:*.zero.wikipedia.org, DNS:mediawiki.org, DNS:w.wiki, DNS:wikibooks.org, DNS:wikidata.org, DNS:wikimedia.org, DNS:wikimediafoundation.org, DNS:wikinews.org, DNS:wikiquote.org, DNS:wikisource.org, DNS:wikiversity.org, DNS:wikivoyage.org, DNS:wiktionary.org, DNS:wmfusercontent.org, DNS:wikipedia.org
X509v3 Extended Key Usage:
TLS Web Server Authentication, TLS Web Client Authentication
X509v3 Subject Key Identifier:
28:2A:26:2A:57:8B:3B:CE:B4:D6:AB:54:EF:D7:38:21:2C:49:5C:36
X509v3 Authority Key Identifier:
keyid:96:DE:61:F1:BD:1C:16:29:53:1C:C0:CC:7D:3B:83:00:40:E6:1A:7C
Signature Algorithm: sha256WithRSAEncryption
8b:c3:ed:d1:9d:39:6f:af:40:72:bd:1e:18:5e:30:54:23:35:
...
To validate this end-entity certificate, one needs an intermediate certificate that matches its Issuer and Authority Key Identifier:
| Issuer | C=BE, O=GlobalSign nv-sa, CN=GlobalSign Organization Validation CA - SHA256 - G2 |
|---|---|
| Authority Key Identifier | 96:DE:61:F1:BD:1C:16:29:53:1C:C0:CC:7D:3B:83:00:40:E6:1A:7C |
In a TLS connection, a properly-configured server would provide the intermediate as part of the handshake. However, it's also possible to retrieve the intermediate certificate by fetching the "CA Issuers" URL from the end-entity certificate.
Intermediate certificate
[edit]This is an example of an intermediate certificate belonging to a certificate authority. This certificate signed the end-entity certificate above, and was signed by the root certificate below. Note that the subject field of this intermediate certificate matches the issuer field of the end-entity certificate that it signed. Also, the "subject key identifier" field in the intermediate matches the "authority key identifier" field in the end-entity certificate.
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
04:00:00:00:00:01:44:4e:f0:42:47
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=BE, O=GlobalSign nv-sa, OU=Root CA, CN=GlobalSign Root CA
Validity
Not Before: Feb 20 10:00:00 2014 GMT
Not After : Feb 20 10:00:00 2024 GMT
Subject: C=BE, O=GlobalSign nv-sa, CN=GlobalSign Organization Validation CA - SHA256 - G2
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:c7:0e:6c:3f:23:93:7f:cc:70:a5:9d:20:c3:0e:
...
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Certificate Sign, CRL Sign
X509v3 Basic Constraints: critical
CA:TRUE, pathlen:0
X509v3 Subject Key Identifier:
96:DE:61:F1:BD:1C:16:29:53:1C:C0:CC:7D:3B:83:00:40:E6:1A:7C
X509v3 Certificate Policies:
Policy: X509v3 Any Policy
CPS: https://www.globalsign.com/repository/
X509v3 CRL Distribution Points:
Full Name:
URI:http://crl.globalsign.net/root.crl
Authority Information Access:
OCSP - URI:http://ocsp.globalsign.com/rootr1
X509v3 Authority Key Identifier:
keyid:60:7B:66:1A:45:0D:97:CA:89:50:2F:7D:04:CD:34:A8:FF:FC:FD:4B
Signature Algorithm: sha256WithRSAEncryption
46:2a:ee:5e:bd:ae:01:60:37:31:11:86:71:74:b6:46:49:c8:
...
Root certificate
[edit]This is an example of a self-signed root certificate representing a certificate authority. Its issuer and subject fields are the same, and its signature can be validated with its own public key. Validation of the trust chain has to end here. If the validating program has this root certificate in its trust store, the end-entity certificate can be considered trusted for use in a TLS connection. Otherwise, the end-entity certificate is considered untrusted.
Certificate:[19] Data: Version: 3 (0x2) Serial Number: 04:00:00:00:00:01:15:4b:5a:c3:94 Signature Algorithm: sha1WithRSAEncryption Issuer: C=BE, O=GlobalSign nv-sa, OU=Root CA, CN=GlobalSign Root CA Validity Not Before: Sep 1 12:00:00 1998 GMT Not After : Jan 28 12:00:00 2028 GMT Subject: C=BE, O=GlobalSign nv-sa, OU=Root CA, CN=GlobalSign Root CA Subject Public Key Info: Public Key Algorithm: rsaEncryption Public-Key: (2048 bit) Modulus: 00:da:0e:e6:99:8d:ce:a3:e3:4f:8a:7e:fb:f1:8b: ... Exponent: 65537 (0x10001) X509v3 extensions: X509v3 Key Usage: critical Certificate Sign, CRL Sign X509v3 Basic Constraints: critical CA:TRUE X509v3 Subject Key Identifier: 60:7B:66:1A:45:0D:97:CA:89:50:2F:7D:04:CD:34:A8:FF:FC:FD:4B Signature Algorithm: sha1WithRSAEncryption d6:73:e7:7c:4f:76:d0:8d:bf:ec:ba:a2:be:34:c5:28:32:b5: ...
Security
[edit]There are a number of publications about PKI problems by Bruce Schneier, Peter Gutmann and other security experts.[20][21][22]
Architectural weaknesses
[edit]- Use of blocklisting invalid certificates (using CRLs and OCSP),
- If the client only trusts certificates when CRLs are available, then they lose the offline capability that makes PKI attractive. So most clients do trust certificates when CRLs are not available, but in that case an attacker that controls the communication channel can disable the CRLs. Adam Langley of Google has said soft-fail CRL checks are like a safety belt that works except when you have an accident.[23]
- CRLs are notably a poor choice because of large sizes and convoluted distribution patterns,
- Ambiguous OCSP semantics and lack of historical revocation status,
- Revocation of root certificates is not addressed,
- Aggregation problem: Identity claims (authenticate with an identifier), attribute claims (submit a bag of vetted attributes), and policy claims are combined in a single container. This raises privacy, policy mapping, and maintenance issues.[clarification needed]
- Delegation problem: CAs cannot technically restrict subordinate CAs from issuing certificates outside a limited namespaces or attribute set; this feature of X.509 is not in use. Therefore, a large number of CAs exist on the Internet, and classifying them and their policies is an insurmountable task. Delegation of authority within an organization cannot be handled at all, as in common business practice.[24][failed verification]
- Federation problem: Certificate chains that are the result of subordinate CAs, bridge CAs, and cross-signing make validation complex and expensive in terms of processing time. Path validation semantics may be ambiguous. The hierarchy with a third-party trusted party is the only model. This is inconvenient when a bilateral trust relationship is already in place.
- Issuance of an Extended Validation (EV) certificate for a hostname doesn't prevent issuance of a lower-validation certificate valid for the same hostname, which means that the higher validation level of EV doesn't protect against man-in-the-middle attacks.[25]
Problems with certification authorities
[edit]- The person or organization that purchases a certificate will often utilize the least expensive certification authority. In response, CA's have cut prices and removed more expensive validation checks in what is known as a Race to the Bottom. The Race to the Bottom is partly addressed by Extended Validation (EV) certificates, yet trust value in the eyes of security experts are diminishing.[26] According to Peter Gutmann, EV certificates do not add any additional security controls. Rather, EV certificates merely restore CA profits to levels prior to the Race to the Bottom by allowing a CA to charge more for a service they should have been providing all along.[5] The Race to the Bottom is also partly addressed by certificate authorities like Let's Encrypt that provide certificates free of charge.[27] Let's Encrypt has also become the largest provider of certificates with over 500 million websites using it.[28][29]
- Certification authorities attempt to deny almost all warranties to the user and relying parties in their Certification Practice Statement (CPS). For example, Apple Inc states in their CPS, "To the extent permitted by applicable law, Subscriber agreements, if applicable, disclaim warranties from Apple, including any warranty of merchantability or fitness for a particular purpose".[30]
- According to Peter Gutmann, "Users use an undefined certification request protocol to obtain a certificate which is published in an unclear location in a nonexistent directory with no real means to revoke it"[22]
- Like all businesses, CAs are subject to the legal jurisdictions they operate within, and may be legally compelled to compromise the interests of their customers and their users. Intelligence agencies have also made use of false certificates issued through extralegal compromise of CAs, such as DigiNotar, to carry out man-in-the-middle attacks.[citation needed] Another example is a revocation request of the CA of the Dutch government, because of a Dutch law passed in 2018, giving new powers for the Dutch intelligence and security services[31]
Implementation issues
[edit]Implementations suffer from design flaws, bugs, different interpretations of standards and lack of interoperability of different standards. Some problems are:
- Many implementations turn off revocation check:
- Seen as obstacle, policies are not enforced
- If it was turned on in all browsers by default, including code signing, it would probably crash the infrastructure
- DNs are complex and little understood (lack of canonicalization, internationalization problems)
- rfc822Name has two notations
- Name and policy constraints hardly supported
- Key usage ignored, first certificate in a list being used
- Enforcement of custom OIDs is difficult
- Attributes should not be made critical because it makes clients crash
- Unspecified length of attributes lead to product-specific limits
- There are implementation errors with X.509 that allow e.g. falsified subject names using null-terminated strings[32] or code injection attacks in certificates
- By using illegal[33] 0x80 padded subidentifiers of object identifiers, wrong implementations or by using integer overflows of the client's browsers, an attacker can include an unknown attribute in the CSR, which the CA will sign, which the client wrongly interprets as "CN" (OID=2.5.4.3). Dan Kaminsky demonstrated this at the 26th Chaos Communication Congress "Black OPs of PKI"[34]
Cryptographic weaknesses
[edit]Digital signature systems depend on secure cryptographic hash functions to work. When a public key infrastructure allows the use of a hash function that is no longer secure, an attacker can exploit weaknesses in the hash function to forge certificates. Specifically, if an attacker is able to produce a hash collision, they can convince a CA to sign a certificate with innocuous contents, where the hash of those contents is identical to the hash of another, malicious set of certificate contents, created by the attacker with values of their choosing. The attacker can then append the CA-provided signature to their malicious certificate contents, resulting in a malicious certificate that appears to be signed by the CA. Because the malicious certificate contents are chosen solely by the attacker, they can have different validity dates or hostnames than the innocuous certificate. The malicious certificate can even contain a "CA: true" field making it able to issue further trusted certificates.
- MD2-based certificates were used for a long time and were vulnerable to preimage attacks. Since the root certificate already had a self-signature, attackers could use this signature and use it for an intermediate certificate.
- In 2005, Arjen Lenstra and Benne de Weger demonstrated "how to use hash collisions to construct two X.509 certificates that contain identical signatures and that differ only in the public keys", achieved using a collision attack on the MD5 hash function.[35]
- In 2008, Alexander Sotirov and Marc Stevens presented at the Chaos Communication Congress a practical attack that allowed them to create a rogue Certificate Authority, accepted by all common browsers, by exploiting the fact that RapidSSL was still issuing X.509 certificates based on MD5.[36]
- In April 2009 at the Eurocrypt Conference,[37] Australian Researchers of Macquarie University presented "Automatic Differential Path Searching for SHA-1".[38] The researchers were able to deduce a method which increases the likelihood of a collision by several orders of magnitude.[39]
- In February 2017, a group of researchers led by Marc Stevens produced a SHA-1 collision, demonstrating SHA-1's weakness.[40]
Mitigations for cryptographic weaknesses
[edit]Exploiting a hash collision to forge X.509 signatures requires that the attacker be able to predict the data that the certificate authority will sign. This can be somewhat mitigated by the CA generating a random component in the certificates it signs, typically the serial number. The CA/Browser Forum has required serial number entropy in its Baseline Requirements Section 7.1 since 2011.[41]
As of January 1, 2016[update], the Baseline Requirements forbid issuance of certificates using SHA-1. As of early 2017[update], Chrome[42] and Firefox[43] reject certificates that use SHA-1. As of May 2017[update] both Edge[44] and Safari[45] are also rejecting SHA-1 certificate. OpenSSL began rejecting SHA-1 certificates by default in version 3.0, released September 2021.[46]
PKI standards for X.509
[edit]- PKCS7 (Cryptographic Message Syntax Standard — public keys with proof of identity for signed and/or encrypted message for PKI)[47]
- Transport Layer Security (TLS) and its predecessor SSL — cryptographic protocols for Internet secure communications.[48]
- Online Certificate Status Protocol (OCSP)[49] / certificate revocation list (CRL)[10] — this is to check certificate revocation status
- PKCS12 (Personal Information Exchange Syntax Standard) — used to store a private key with the appropriate public key certificate[50]
- RFC 4158 — Certification Path Building — guidance and recommendations for building X.509 public-key certification paths within applications (i.e., validating an end-entity certificate using a CA certificate)
PKIX Working Group
[edit]In 1995, the Internet Engineering Task Force in conjunction with the National Institute of Standards and Technology[51] formed the Public-Key Infrastructure (X.509) working group. The working group, concluded in June 2014,[52] is commonly referred to as "PKIX." It produced RFCs and other standards documentation on using and deploying X.509 in practice. In particular it produced RFC 3280 and its successor RFC 5280, which define how to use X.509 in Internet protocols.
Major protocols and standards using X.509 certificates
[edit]TLS/SSL and HTTPS use the RFC 5280 profile of X.509, as do S/MIME (Secure Multipurpose Internet Mail Extensions) and the EAP-TLS method for WiFi authentication. Any protocol that uses TLS, such as SMTP, POP, IMAP, LDAP, XMPP, and many more, inherently uses X.509.
IPsec can use the RFC 4945 profile for authenticating peers.
The OpenCable security specification defines its own profile of X.509 for use in the cable industry.
Devices like smart cards and TPMs often carry certificates to identify themselves or their owners. These certificates are in X.509 form.
The WS-Security standard defines authentication either through TLS or through its own certificate profile.[19] Both methods use X.509.
The Microsoft Authenticode code signing system uses X.509 to identify authors of computer programs. Secure Boot feature of UEFI uses X.509 to authenticate UEFI drivers or bootloaders during booting and disallow blocklisted drivers or bootloaders (by using Forbidden Key Exchange or dbx database).[53]
The OPC UA industrial automation communication standard uses X.509.
SSH generally uses a Trust On First Use security model and doesn't have need for certificates. However, the popular OpenSSH implementation does support a CA-signed identity model based on its own non-X.509 certificate format.[54]
See also
[edit]References
[edit]- ^ "X.509: Information technology - Open Systems Interconnection - The Directory: Public-key and attribute certificate frameworks". ITU. Retrieved 6 November 2019.
- ^ a b Hesse, Peter; Cooper, Matt; Dzambasow, Yuriy A.; Joseph, Susan; Nicholas, Richard (September 2005). Internet X.509 Public Key Infrastructure: Certification Path Building. Network Working Group. doi:10.17487/RFC4158. RFC 4158. Informational.
- ^ "Monumental Cybersecurity Blunders". circleid.com. Retrieved 2022-09-03.
- ^ Cooper, D.; Santesson, S.; Farrell, S.; Boeyen, S.; Housley, R.; Polk, W. (May 2008). Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. doi:10.17487/RFC5280. RFC 5280. Proposed Standard. Updated by RFC 9549, 9598, 8398, 8399 and 6818. Obsoletes RFC 4630, 4325 and 3280.
Following is a simplified view of the architectural model assumed by the Public-Key Infrastructure using X.509 (PKIX) specifications.
- ^ a b c d Gutmann, Peter (April 2014). "Engineering Security" (PDF).
- ^ Housley, R.; Hoffman, P. (May 1999). Internet X.509 Public Key Infrastructure Operational Protocols: FTP and HTTP. Network Working Group. doi:10.17487/RFC2585. RFC 2585. Proposed Standard. sec. 4: MIME registrations.
- ^ "x509Certificate". Apple Developer Documentation: Uniform Type Identifiers. Apple Inc.
- ^ "CA:IncludedCAs". Mozilla Wiki. Retrieved 17 January 2017.
- ^ "Bug 110161 - (ocspdefault) enable OCSP by default". Mozilla. Retrieved 17 March 2016.
- ^ a b c d e f g h Cooper, D.; Santesson, S.; Farrell, S.; Boeyen, S.; Housley, R.; Polk, W. (May 2008). Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. doi:10.17487/RFC5280. RFC 5280. Proposed Standard. Updated by RFC 9549, 9598, 8398, 8399 and 6818. Obsoletes RFC 4630, 4325 and 3280.
- ^ Nelson B Boyard (9 May 2002). "All About Certificate Extensions". Mozilla. Archived from the original on 15 December 2018. Retrieved 10 September 2020.
- ^ "EV UI Moving to Page Info". Chromium Docs. 2021. Retrieved 2025-07-12.
- ^ "Improved Security and Privacy Indicators in Firefox 70". Mozilla Security Blog. 2019-10-15. Retrieved 2025-07-12.
- ^ "Extended Validation Certificates are (Really, Really) Dead". Troy Hunt. 2019-08-13. Retrieved 2025-07-12.
- ^ sysadmin1138 (May 19, 2009). "What is a Pem file and how does it differ from other OpenSSL Generated Key File Formats?". Server Fault. Retrieved 19 October 2023.
{{cite web}}: CS1 maint: numeric names: authors list (link) This article incorporates text from this source, which is available under the CC BY-SA 2.5 license.
This article incorporates text from this source, which is available under the CC BY-SA 2.5 license.
- ^ Lloyd, Steve (September 2002). Understanding Certification Path Construction (PDF). PKI Forum. Archived from the original (PDF) on 2019-02-04. Retrieved 2014-11-07.
- ^ "Cross-Certification Between Root CAs". Qualified Subordination Deployment Scenarios. Microsoft. August 2009.
- ^ Nash; Duane; Joseph; Brink (2001). "Key and Certificate Life Cycles. CA Certificate Renewal". PKI: Implementing and Managing E-Security. RSA Press - Osborne/McGraw-Hill. ISBN 0-07-213123-3.
- ^ a b "Web Services Security X.509 Token Profile Version 1.1.1". Oasis. Retrieved 14 March 2017.
- ^ Carl Ellison and Bruce Schneier. "Top 10 PKI risks" (PDF). Computer Security Journal (Volume XVI, Number 1, 2000). Archived from the original (PDF) on 2015-11-24. Retrieved 2014-04-02.
- ^ Peter Gutmann. "PKI: it's not dead, just resting" (PDF). IEEE Computer (Volume:35, Issue: 8).
- ^ a b Gutmann, Peter. "Everything you Never Wanted to Know about PKI but were Forced to Find Out" (PDF). Retrieved 14 November 2011.
- ^ Langley, Adam (5 February 2012). "Revocation checking and Chrome's CRL". Imperial Violet. Retrieved 2 February 2017.
- ^ "Security Systems Business Plan Sample [2021]". OGScapital. 2014-01-27. Retrieved 2021-06-30.
- ^ Michael Zusman; Alexander Sotirov (July 2009). "Sub-Prime PKI: Attacking Extended Validation SSL" (PDF). Blackhat. Retrieved 10 September 2020.
- ^ Hunt, Troy (17 September 2018). "Extended Validation Certificates are Dead". TroyHunt.com. Retrieved 26 February 2019.
- ^ "Let's Encrypt". Let's Encrypt. 2023-07-10. Retrieved 2025-04-08.
- ^ "For A Better Internet - ISRG 2020 Annual Report" (PDF). Internet Security Research Group. 2020-11-17. Retrieved 2021-05-11.
- ^ "Let's Encrypt Stats". Let's Encrypt. 2023-07-10. Retrieved 2025-04-08.
- ^ "Certification Authority — Certification Practice Statement" (PDF). Version 6.1. Apple, Inc. August 19, 2016.
- ^ van Pelt, Cris. "Logius: Dutch Government CA trust issue". Bugzilla. Retrieved 31 October 2017.
- ^ Moxie Marlinspike (2009). "More Tricks for Defeating SSL in Practice" (PDF). Institute For Disruptive Studies. Blackhat. Retrieved 10 September 2020.
- ^ Rec. ITU-T X.690, clause 8.19.2
- ^ Dan Kaminsky (29 December 2009). "26C3: Black Ops Of PKI". CCC Events Blog. Der Chaos Computer Club. Retrieved 29 September 2013.
- ^ Lenstra, Arjen; de Weger, Benne (19 May 2005). On the possibility of constructing meaningful hash collisions for public keys (PDF) (Technical report). Lucent Technologies, Bell Laboratories & Technische Universiteit Eindhoven. Archived (PDF) from the original on 14 May 2013. Retrieved 28 September 2013.
- ^ "MD5 considered harmful today". Eindhoven University of Technology. 16 June 2011. Retrieved 29 September 2013.
- ^ "Eurocrypt 2009". International Association for Cryptologic Research.
- ^ Cameron McDonald; Philip Hawkes; Josef Pieprzyk (2009). "SHA-1 collisions now" (PDF). Macquarie University and Qualcomm. Retrieved 10 September 2020.
- ^ Dennis Dwyer (2 June 2009). "SHA-1 Collision Attacks Now 252". SecureWorks Insights. Retrieved 24 February 2016.
- ^ Marc Stevens; Elie Bursztein; Pierre Karpman; Ange Albertini; Yarik Markov. "The first collision for full SHA-1" (PDF). CWI Amsterdam & Google Research. Retrieved 10 September 2020 – via Shattered.
- ^ "Baseline Requirements Documents". CA Browser Forum. Retrieved 19 March 2017.
- ^ Andrew Whalley (16 November 2016). "SHA-1 Certificates in Chrome". Google Online Security Blog. Retrieved 19 March 2017.
- ^ "The end of SHA-1 on the Public Web". Mozilla Security Blog. 23 February 2017. Retrieved 19 March 2017.
- ^ "Microsoft Security Advisory 4010323". Technet. Microsoft. Retrieved 16 May 2017.
- ^ "Safari and WebKit do not support SHA-1 certificates". Apple Support. 16 August 2018. Retrieved 10 September 2020.
- ^ "openssl/NEWS.md at master · openssl/openssl". GitHub. Retrieved 2025-02-16.
- ^ B. Kaliski (March 1998). PKCS #7: Cryptographic Message Syntax Version 1.5. Network Working Group. doi:10.17487/RFC2315. RFC 2315. Informational.
- ^ T. Dierks; E. Rescorla (August 2008). The Transport Layer Security (TLS) Protocol Version 1.2. IETF TLS workgroup. doi:10.17487/RFC5246. RFC 5246. Obsolete. Obsoleted by RFC 8446. Obsoletes RFC 3268, 4346 and 4366; updates RFC 4492.
- ^ S. Santesson; M. Myers; R. Ankey; S. Galperin; C. Adams (June 2013). X.509 Internet Public Key Infrastructure Online Certificate Status Protocol - OCSP. Internet Engineering Task Force. doi:10.17487/RFC6960. RFC 6960. Proposed Standard. Updated by RFC 8954. Obsoletes RFC 6277 and 2560. Updates RFC 5912.
- ^ "PKCS 12: Personal Information Exchange Syntax Standard". EMC.com. RSA Laboratories. Archived from the original on 6 July 2017. Retrieved 19 March 2017.
- ^ "Public-Key Infrastructure (X.509) (pkix) - Charter". IETF Datatracker. Internet Engineering Task Force. Retrieved 1 October 2013.
- ^ "Pkix Status Pages". IETF Tools. Retrieved 10 March 2017.
- ^ Smith, Roderick W. (2012-11-04). "Managing EFI Boot Loaders for Linux: Controlling Secure Boot (Managing Keys from Linux)". Roderick W. Smith's Web Page. Retrieved 2025-02-20.
- ^ "How To Create an SSH CA to Validate Hosts and Clients with Ubuntu". DigitalOcean. Retrieved 19 March 2017.
External links
[edit]- ITU-T's X.509 standards
- Peter Gutmann's articles:
- "Crypto FAQ from RSA Labs". RSA Laboratories. Archived from the original on 30 December 2006.
- Secure code guidelines Sun
- RFC 4158 – "Internet X.509 Public Key Infrastructure: Certification Path Building," Informational.
- RFC 5280 – "Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile," Proposed Standard.
- Understanding Digital Certificates Microsoft TechNet
X.509
View on GrokipediaIntroduction
Definition and Purpose
X.509 is an ITU-T Recommendation that defines the syntax and frameworks for public-key and attribute certificates as part of the Open Systems Interconnection (OSI) X.500 directory services standard.[4] Originally published in November 1988, it establishes a standardized format for certificates within directory-based authentication systems.[3] The primary purpose of X.509 is to bind public keys to the identities of their owners, thereby enabling trusted digital signatures, encryption, and secure communication protocols such as Transport Layer Security (TLS) and Secure Sockets Layer (SSL).[3] This binding ensures that entities can verify the authenticity of public keys used in cryptographic operations, supporting authentication in distributed systems.[4] Within the broader context of Public Key Infrastructure (PKI), X.509 certificates function as digital identities issued by trusted Certificate Authorities (CAs), facilitating secure exchange of information across networks without relying on prior shared secrets.[3] Over time, the standard has evolved from its initial X.500 directory-centric design to accommodate non-directory applications, including widespread use in web security and Internet PKI.[3]Historical Development
The X.509 standard originated in 1988 as part of the ITU-T X.500 series for directory services, specifically within the authentication framework of Recommendation X.509 (Edition 1, dated November 25, 1988), which introduced concepts such as public key certificates, certification paths, and certificate revocation lists (CRLs) to support simple and strong authentication in directory-based systems.[5] This initial version was developed by ITU-T Study Group 7 to enable secure authentication mechanisms within the broader X.500 directory infrastructure.[5] In 1993, Edition 2 (November 16, 1993) introduced fields like issuerUniqueIdentifier and subjectUniqueIdentifier to enhance certificate identification and flexibility, marking the transition to version 2 of the standard.[5] Version 3 followed in Edition 3 (August 9, 1997), adding critical extensions to certificates and CRLs, including CRL distribution points, delta CRLs, and support for attribute certificates, which significantly improved adaptability for diverse applications.[5] Subsequent editions built on this foundation: Edition 4 (March 31, 2000) retitled the recommendation to focus on public-key and attribute certificate frameworks, incorporating privilege management infrastructure (PMI) models and attribute certificate extensions.[5] Further refinements occurred in Edition 5 (August 29, 2005) with enhancements to PMI models and the timeSpecification extension, followed by Edition 6 (November 13, 2008), which introduced federated PMI models, policy decision points (PDPs), and policy enforcement points (PEPs).[5] Edition 7 (October 14, 2012) extended federated PMI and policy attribute certificates, while Edition 8 (October 14, 2016) added trust brokers, attribute value lists (AVLs), wrapper protocols, and relocated directory authentication to X.500 specifications.[5] Edition 9 (October 14, 2019) incorporated extensions for quantum-safe algorithms and moved protocols to the X.510 series, with subsequent Corrigendum 1 (October 2021), Corrigendum 2 (October 2023), and Amendment 1 (October 2024) introducing miscellaneous enhancements.[5][6] Adoption accelerated with the IETF's Public-Key Infrastructure (X.509) (PKIX) Working Group, established in 1995 to adapt X.509 for Internet applications, culminating in RFC 2459 (January 1999), which profiled X.509 version 3 certificates and version 2 certificate revocation lists (CRLs) for Internet use.[7] This integration drove widespread deployment, particularly following the 1995 release of SSL 2.0, which utilized X.509 certificates for secure web communications, influencing global PKI growth through subsequent protocols like SSL 3.0 (1996) and TLS.[8]Certificate Format
Core Structure and ASN.1 Encoding
X.509 certificates are specified using Abstract Syntax Notation One (ASN.1), an International Telecommunication Union Telecommunication Standardization Sector (ITU-T) standard for defining data structures in a platform-independent manner. This notation allows for the description of complex data types, which are then encoded for transmission or storage. The primary encoding rule for X.509 certificates is the Distinguished Encoding Rules (DER), a deterministic subset of Basic Encoding Rules (BER) defined in ITU-T X.690, ensuring unique binary representations suitable for cryptographic operations like signing and verification.[9] For human-readable or text-based applications, certificates are commonly converted to Privacy-Enhanced Mail (PEM) format, which encapsulates the DER binary data in Base64 encoding with ASCII headers and footers such as "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----".[10] At the highest level, an X.509 certificate is structured as an ASN.1 SEQUENCE comprising three mandatory components: the To Be Signed certificate (TBSCertificate), the signature algorithm identifier, and the signature value.[9] The TBSCertificate contains the substantive information about the certificate, including its version, serial number, issuer and subject identities, validity period, and public key details; this portion is hashed and signed by the issuer's private key to produce the signatureValue.[11] The signatureAlgorithm specifies the cryptographic algorithm (e.g., RSA with SHA-256) used for the signature, matching the one in the TBSCertificate for consistency.[12] This top-level SEQUENCE ensures the integrity of the certificate's contents through the appended digital signature. The TBSCertificate itself is an ASN.1 SEQUENCE with the following key fields, supporting versions 1, 2, or 3 of the X.509 standard (version 3 is the basis for modern usage and includes support for extensions).[11] The version field, explicitly tagged as context-specific , is an INTEGER defaulting to v1 (0) but set to v3 (2) when extensions are present.[13] The serialNumber is a unique positive INTEGER (up to 20 octets) assigned by the issuing authority to distinguish this certificate from others it issues.[14] An additional signature field within the TBSCertificate identifies the algorithm used by the issuer.[15] The issuerName and subjectName fields represent the identities of the issuer and subject as X.500 distinguished names (DNs), which are hierarchical identifiers composed of a sequence of relative distinguished names (RDNs); each RDN is a multivalued SET of attribute type-value pairs (e.g., countryName=US, organizationName=Example Corp), encoded according to ITU-T X.500 standards.[16] The validity field is a SEQUENCE of two time values—notBefore and notAfter—marking the start and end of the certificate's operational period, represented as either UTCTime (for dates before 2050) or GeneralizedTime formats.[17] The subjectPublicKeyInfo field is a SEQUENCE detailing the subject's public key algorithm (via AlgorithmIdentifier) and the key itself as a BIT STRING, enabling verification of signatures made with this key.[18] Versions 2 and 3 also permit optional issuerUniqueID and subjectUniqueID fields (tagged [19] and [20], respectively) as BIT STRINGS for additional identification in large-scale directories, though they are rarely used today; version 3 further includes an optional extensions field (tagged [21]) for extensible attributes.[22] The full ASN.1 schema for an X.509 version 3 certificate, as profiled for Internet use, is defined in the following notation (excerpted from the PKIX ASN.1 module, with supporting types for completeness):Certificate ::= SEQUENCE {
tbsCertificate TBSCertificate,
signatureAlgorithm AlgorithmIdentifier,
signatureValue BIT STRING }
TBSCertificate ::= SEQUENCE {
version [0] EXPLICIT Version DEFAULT v1,
serialNumber CertificateSerialNumber,
signature AlgorithmIdentifier,
issuer Name,
validity Validity,
subject Name,
subjectPublicKeyInfo SubjectPublicKeyInfo,
issuerUniqueID [1] IMPLICIT UniqueIdentifier OPTIONAL,
subjectUniqueID [2] IMPLICIT UniqueIdentifier OPTIONAL,
extensions [3] EXPLICIT Extensions OPTIONAL }
Version ::= INTEGER { v1(0), v2(1), v3(2) }
CertificateSerialNumber ::= INTEGER
Name ::= CHOICE { rdnSequence RDNSequence }
RDNSequence ::= SEQUENCE OF RelativeDistinguishedName
RelativeDistinguishedName ::= SET SIZE (1..MAX) OF AttributeTypeAndValue
AttributeTypeAndValue ::= SEQUENCE {
type AttributeType,
value AttributeValue }
Validity ::= SEQUENCE {
notBefore Time,
notAfter Time }
Time ::= CHOICE {
utcTime UTCTime,
generalTime GeneralizedTime }
SubjectPublicKeyInfo ::= SEQUENCE {
algorithm AlgorithmIdentifier,
subjectPublicKey BIT STRING }
Certificate ::= SEQUENCE {
tbsCertificate TBSCertificate,
signatureAlgorithm AlgorithmIdentifier,
signatureValue BIT STRING }
TBSCertificate ::= SEQUENCE {
version [0] EXPLICIT Version DEFAULT v1,
serialNumber CertificateSerialNumber,
signature AlgorithmIdentifier,
issuer Name,
validity Validity,
subject Name,
subjectPublicKeyInfo SubjectPublicKeyInfo,
issuerUniqueID [1] IMPLICIT UniqueIdentifier OPTIONAL,
subjectUniqueID [2] IMPLICIT UniqueIdentifier OPTIONAL,
extensions [3] EXPLICIT Extensions OPTIONAL }
Version ::= INTEGER { v1(0), v2(1), v3(2) }
CertificateSerialNumber ::= INTEGER
Name ::= CHOICE { rdnSequence RDNSequence }
RDNSequence ::= SEQUENCE OF RelativeDistinguishedName
RelativeDistinguishedName ::= SET SIZE (1..MAX) OF AttributeTypeAndValue
AttributeTypeAndValue ::= SEQUENCE {
type AttributeType,
value AttributeValue }
Validity ::= SEQUENCE {
notBefore Time,
notAfter Time }
Time ::= CHOICE {
utcTime UTCTime,
generalTime GeneralizedTime }
SubjectPublicKeyInfo ::= SEQUENCE {
algorithm AlgorithmIdentifier,
subjectPublicKey BIT STRING }
Key Fields and Components
The X.509 certificate structure includes several core fields that provide essential information for identifying, validating, and using the certificate in public key infrastructure (PKI) systems. These fields form the tbsCertificate (to-be-signed certificate) portion, which is digitally signed by the issuer to ensure integrity and authenticity.[9] The serial number is a unique positive integer assigned by the issuing certificate authority (CA) to distinguish this certificate from others issued by the same CA. It serves as a permanent identifier for the certificate throughout its lifecycle, typically represented as a 20-octet or shorter value to prevent collisions in large-scale deployments.[14] The signature algorithm field specifies the cryptographic algorithm used by the CA to sign the certificate, including the hashing function and public key algorithm, such as SHA-256 with RSA or ECDSA with SHA-384. This identifies the method for verifying the certificate's signature against the issuer's public key, ensuring the certificate has not been tampered with. Modern profiles recommend secure algorithms like those from the RSA and elliptic curve families to resist current cryptanalytic attacks.[12] The issuer name is the distinguished name (DN) of the CA that issued the certificate, typically including attributes like country, organization, and common name to uniquely identify the authority. This field enables traceability back to the issuing entity in a certificate chain and is crucial for validation processes.[16] The validity period defines the time window during which the certificate is considered valid, specified by two UTC timestamps: notBefore (the start of validity) and notAfter (the end). Certificates must include both fields, with notBefore typically set to or shortly before issuance and notAfter up to 398 days later in modern browser-enforced policies as of 2023, to balance security and usability by limiting exposure to key compromise. Systems reject certificates used outside this period.[17] The subject name is the DN of the entity to which the certificate is issued, such as a person, device, or organization, often including commonName (e.g., a hostname like "www.example.com"), organization, and organizational unit. It binds the public key to a specific identity, allowing relying parties to associate the key with the intended subject.[24] The subject public key info field contains the public key of the subject along with its algorithm identifier, such as RSA (with modulus and exponent) or ECDSA (with curve parameters and point). This encapsulates the key material in a bit string format, enabling encryption, signature verification, or key exchange using the specified algorithm. It is the primary payload for secure communications.[18] Introduced in version 2 certificates, the optional issuer unique ID and subject unique ID fields provide bit strings to resolve ambiguities when multiple issuers or subjects share the same DN. These were designed for environments with name reuse but are rarely used in contemporary PKI due to improved naming practices and are not recommended for new certificates.[22] In self-signed root certificates, the issuer name equals the subject name, as the CA signs its own certificate using its private key. These serve as trust anchors in PKI hierarchies, where the public key is explicitly trusted by relying parties without further chain validation.[25]Extensions for Specific Usages
X.509 version 3 introduced a flexible extension mechanism to tailor certificates for diverse applications without altering the core structure. Each extension consists of an object identifier (OID) that uniquely identifies its type, a criticality flag indicating whether the extension must be recognized (if critical, unrecognized extensions render the certificate invalid), and an extension value encoded as an ASN.1 DER OCTET STRING containing the specific data.[26] This structure allows for both standard and private extensions, enabling customization while maintaining interoperability.[26] The basicConstraints extension, identified by OID 2.5.29.19, specifies whether the subject can act as a certification authority (CA) and constrains the certification path length. It includes a cA boolean flag (TRUE for CAs, default FALSE for end-entity certificates) and an optional pathLenConstraint integer that limits the maximum number of non-self-issued CA certificates in the path following this one, preventing excessively deep hierarchies.[27] For instance, a pathLenConstraint of 2 allows up to two additional CA levels beyond the issuing CA. This extension is typically marked critical in CA certificates to enforce hierarchy limits.[27] Key usage, defined under OID 2.5.29.15, restricts the cryptographic operations permissible with the public key, using a bit string to indicate allowed purposes. Relevant bits include digitalSignature (bit 0) for verifying digital signatures on data, keyEncipherment (bit 2) for encrypting private keys during key transport, dataEncipherment (bit 3) for encrypting user data, keyAgreement (bit 4) for key derivation in agreements like Diffie-Hellman, certSign (bit 5) for signing certificates, and cRLSign (bit 6) for signing certificate revocation lists.[28] In CA certificates, this extension must be critical to ensure keys are used only for authorized functions, such as certSign without dataEncipherment.[28] The extended key usage (EKU) extension, OID 2.5.29.37, supplements key usage by specifying application-specific purposes through a sequence of OIDs, allowing finer-grained policy enforcement. Standard KeyPurposeIds include serverAuth (1.3.6.1.5.5.7.3.1) for authenticating TLS/SSL servers and clientAuth (1.3.6.1.5.5.7.3.2) for client authentication in TLS/SSL.[29] This non-critical extension (by default) enables protocols to verify if a certificate suits a particular role, such as requiring serverAuth for web server certificates. A recent addition, defined in 2025, introduces an Instant Messaging URI KeyPurposeId (id-kp-imUri, 1.3.6.1.5.5.7.3.40) for certificates binding keys to instant messaging URIs, supporting secure identity in messaging protocols like XMPP.[30] Subject alternative name (SAN), OID 2.5.29.17, extends the subject's distinguished name by listing additional identities in a GeneralNames structure, accommodating modern naming schemes. It supports dNSName for domain names (e.g., example.com), iPAddress for IP addresses (e.g., 192.0.2.1 as an OCTET STRING), and rfc822Name for email addresses (e.g., [email protected]).[31] This extension is critical if the subject DN is empty and is essential for protocols like TLS where multiple identifiers (e.g., DNS and IP) must be validated against the presented name.[31] Authority key identifier (OID 2.5.29.35) and subject key identifier (OID 2.5.29.14) facilitate certificate chain construction and validation by uniquely identifying public keys. The authority key identifier typically contains a keyIdentifier field as a SHA-1 hash of the issuing CA's public key, optionally including the issuer name and serial number for precise matching.[32] The subject key identifier, a non-critical extension, uses a similar hash of the subject's public key to link certificates to keys without relying on names.[33] Together, they enable efficient path building by matching the subject key identifier of one certificate to the authority key identifier of the next.[32] CRL distribution points (OID 2.5.29.31) provide URIs where certificate revocation lists can be retrieved, using a sequence of DistributionPoint structures with GeneralNames for locations (e.g., HTTP or LDAP endpoints).[34] This non-critical extension supports revocation checking by directing relying parties to the appropriate CRL sources. Similarly, authority information access (OID 1.3.6.1.5.5.7.1.1) offers access methods for CA services, such as OCSP responders (via id-ad-ocsp, 1.3.6.1.5.5.7.48.1) or CA issuer certificates (id-ad-caIssuers, 1.3.6.1.5.5.7.48.2), each paired with a URI.[35] These extensions, typically non-critical, enhance operational efficiency in public key infrastructures by streamlining access to revocation and authority data.[34][35]PKI Fundamentals
Certificate Authorities and Hierarchy
In the X.509 public key infrastructure (PKI), Certificate Authorities (CAs) serve as trusted entities responsible for issuing, managing, and signing digital certificates that bind public keys to identified subjects, thereby establishing a framework for secure authentication and authorization.[36] The hierarchical structure of CAs enables a distributed trust model, where higher-level authorities delegate signing capabilities to subordinates while maintaining control through constraints and oversight.[37] CAs are categorized into distinct types based on their position and role within the hierarchy. A root CA represents the apex of the trust chain, issuing a self-signed certificate that serves as the ultimate trust anchor; these are typically maintained offline to minimize exposure to compromise.[38] Intermediate or subordinate CAs, signed by a root or higher-level CA, act as intermediaries that issue certificates to other CAs or end entities, often constrained by the basicConstraints extension to limit delegation depth.[27] End-entity certificates, also known as leaf certificates, are issued to final users or devices and do not permit further issuance, focusing instead on specific operational keys.[37] The trust model in X.509 relies on root CAs being pre-installed in system trust stores, such as those in web browsers and operating systems, allowing relying parties to validate certification paths back to a known trusted root. For instance, roots like ISRG Root X1 from Let's Encrypt and historical VeriSign roots (now managed under DigiCert) are included in major browser trust stores to support public web PKI.[39] Hierarchies are generally limited to 2-3 levels to reduce risk propagation, enforced via the pathLenConstraint in the basicConstraints extension, which specifies the maximum number of non-self-issued certificates that may follow in a path.[27] CA responsibilities encompass generating key pairs for their own operations, vetting the identities of subjects before issuance, digitally signing certificates to affirm bindings, and managing key rollovers to ensure continuity and security.[9] These duties are outlined in standards to promote interoperability, with CAs required to maintain consistent naming and provide mechanisms for status updates.[40] X.509 supports both public and private PKIs, differing in scope and trust distribution. Public PKIs, such as the Web PKI, involve globally trusted CAs whose roots are embedded in widespread trust stores for Internet-scale applications like HTTPS.[41] In contrast, private PKIs are deployed within enterprises or closed networks, using organization-specific root CAs not reliant on external trust stores, allowing customized policies and reduced exposure to global threats.[42] This hierarchy facilitates chain construction, where end-entity certificates trace upward through intermediates to a root for validation.[38]Chains, Paths, and Validation
In X.509 public key infrastructure (PKI), a certificate chain, also known as a certification path, consists of an ordered sequence of one or more certificates that establishes a binding from an end-entity certificate to a trust anchor. The path begins with the end-entity certificate and proceeds through intermediate certificates, each signed by the issuer of the subsequent certificate, culminating in a self-signed root certificate or equivalent trust anchor. This sequence ensures that the public key of the end entity is traceable back to a trusted authority, with no duplicate certificates permitted in the path.[43] Path construction involves assembling this sequence by matching the subject distinguished name (DN) and public key of one certificate to the issuer DN and key of the next. To facilitate efficient identification, especially when multiple certificates share the same subject DN, implementations use the Authority Key Identifier (AKID) extension in the issued certificate, which includes the issuer's subject public key identifier (SKID) and optionally the issuer DN or serial number, allowing precise linkage without relying solely on DN matching. Additional mechanisms include Authority Information Access (AIA) extension chasing, where the AIA provides URIs to retrieve the issuer's certificate via protocols like HTTP or LDAP, or bundle provision, where the full chain is supplied directly in application protocols such as TLS. Path building algorithms typically employ forward building (starting from the end-entity and chasing issuers toward the trust anchor) or reverse building (starting from the trust anchor and descending to the end-entity), often using depth-first search to explore possible paths while avoiding cycles through visited certificate tracking.[44][45][35] Validation of a certification path, as defined in the basic path validation algorithm, proceeds in phases: initialization, basic certificate processing for each certificate in the path, and final wrap-up. During initialization, the relying party selects a trust anchor—typically a pre-trusted root CA certificate or public key with associated name and parameters—and sets initial state variables such as the current time and policy set. For each certificate, validation verifies the digital signature using the issuer's public key from the prior certificate (or trust anchor for the first), confirms the certificate's validity period encompasses the current time (using UTCTime for dates before 2050 and GeneralizedTime thereafter), ensures appropriate key usage via the keyUsage extension (e.g., keyCertSign for CA certificates), and checks revocation status through mechanisms like Certificate Revocation Lists (CRLs) or the Online Certificate Status Protocol (OCSP), confirming the certificate is not revoked as of the current time. Additional checks include compliance with name constraints (permitted or excluded subtrees in the nameConstraints extension) and policy requirements, such as processing certificatePolicies OIDs and applying policy mappings where allowed. The wrap-up phase evaluates the final policy tree against the initial policy set to determine if the path validates successfully.[38][17][28][46] In cross-domain or hierarchical scenarios, validation incorporates name constraints to restrict the namespaces (e.g., DNS names or directory names) allowable in subordinate certificates, ensuring the end-entity name falls within permitted subtrees defined by higher-level CAs and excluding prohibited ones. Policy mapping, facilitated by the policyMappings extension, allows equivalence between certification policies across domains (e.g., mapping a policy OID from one PKI to another), but this can be inhibited by policyConstraints extensions that prohibit mapping or require explicit policy identifiers at specific path lengths. These mechanisms enforce trust boundaries in multi-domain PKIs while maintaining the integrity of the validation process.[47][48][49]Certificate Lifecycle
Issuance, Renewal, and Revocation
The issuance of an X.509 certificate begins with the end entity generating a public-private key pair and creating a Certificate Signing Request (CSR) that includes the public key, subject distinguished name, and optional attributes, signed with the private key as defined in PKCS#10.[50] The CSR is submitted to a Certificate Authority (CA), which performs vetting to verify the requester's identity or control according to standardized levels: Domain Validated (DV) confirms only domain ownership through automated methods like email or DNS challenges; Organization Validated (OV) additionally verifies the legal existence and operational status of the organization; and Extended Validated (EV) requires rigorous checks including physical address, operational history, and legal documents to provide the highest assurance. Upon successful vetting, the CA constructs the X.509 v3 certificate by embedding the subject's public key, validity period, and extensions, then signs it with the CA's private key to bind the identity to the key.[3] Certificate renewal involves re-issuing a new certificate before the existing one's validity period expires, often generating a fresh key pair to enhance security, though key reuse is permitted in some cases if no compromise is suspected.[3] This process mirrors issuance, typically via automated protocols like ACME (Automated Certificate Management Environment), which supports short-lived certificates with 90-day validity periods, as implemented by services such as Let's Encrypt to minimize exposure risks from prolonged validity. Recent industry trends have shortened maximum validity periods; for instance, since September 2020, Google Chrome has enforced a 398-day (approximately 13-month) limit on publicly trusted TLS certificates. The CA/B Forum passed Ballot SC081v3 in April 2025, establishing a phased reduction in maximum validity periods for publicly trusted TLS subscriber certificates: to 200 days effective March 15, 2026; 100 days effective March 15, 2027; and 47 days effective March 15, 2029,[51] to promote automation and reduce compromise windows. Certificate Transparency (CT) logs, append-only public records of issued certificates, enable real-time monitoring of issuance and renewal events to detect anomalies or unauthorized activity. Revocation invalidates a certificate before its expiration due to reasons such as key compromise, CA compromise, or supersession by a new certificate, as enumerated in the CRLReason extension.[3] CAs publish revocation status through Certificate Revocation Lists (CRLs), which are signed X.509 structures defined as a SEQUENCE containing the issuer name, thisUpdate and nextUpdate timestamps, and a revokedCertificates SEQUENCE of entries each with the certificate's serial number, revocationDate, and optional reason code.[3] Alternatively, the Online Certificate Status Protocol (OCSP) provides real-time checks via a single request-response exchange, where the client queries a responder for a specific certificate's status (good, revoked, or unknown), and the response includes a nonce extension—an OCTET STRING—to ensure freshness and prevent replays.[52] Revocation impacts certificate chain validation by requiring status checks at each step, though detailed path processing is handled separately.[3]Cross-Certification Examples
Cross-certification in X.509 public key infrastructures (PKIs) enables the establishment of trust relationships between separate PKI domains by having one certification authority (CA) issue a certificate attesting to the public key of a CA in another domain. This mechanism supports interoperability without requiring a complete merger of hierarchies, using X.509 v3 certificates that include extensions like policyMappings and nameConstraints to define the scope and assurance levels of the trust.[53][54] A prominent root-level cross-certification example is the U.S. Federal Bridge Certification Authority (FBCA), which links the Department of Defense (DoD) PKI with civilian federal agency roots to facilitate secure electronic transactions across government domains. The FBCA issues cross-certificates to participating entity CAs, incorporating the policyMappings extension to align assurance policies—such as medium hardware or PIV authentication—between domains, while nameConstraints limit the trust to specific distinguished names or organizational units, preventing unintended expansion of authority. This setup ensures that DoD-issued certificates can be validated by civilian systems and vice versa, supporting applications like email signing and web authentication under the Federal PKI framework.[53] For intermediate-level cross-certification, consider a scenario where an enterprise CA cross-signs a vendor's subordinate CA to extend trust for a specific subdomain, such as supply chain integrations. In this unidirectional or bidirectional arrangement, the enterprise CA signs the vendor CA's public key in a cross-certificate, applying nameConstraints to restrict issuance to names under a permitted subtree (e.g., ou=vendor-partners.dc=enterprise.com), thereby allowing vendor-issued end-entity certificates to be trusted only within the enterprise's namespace without broader transitive risks. This approach is common in partial mesh PKIs, where the bridge or intermediate CA acts as a nexus, as outlined in PKIX path-building standards.[54] Another application involves CA renewal during key rollover, where a cross-certificate from the predecessor CA maintains validation chains without necessitating re-trusting of root anchors. When a CA undergoes key changeover—such as generating a new key pair before the old one's expiration—the predecessor CA signs the successor's public key in a rollover certificate, ensuring continuity for existing paths while the new key assumes signing duties. This preserves trust for subordinate certificates issued under the old key, with the rollover certificate published in repositories to support path validation until full migration.[55] The core mechanics of cross-certification involve the issuing CA digitally signing the subject CA's public key within an X.509 certificate, often stored in a crossCertificatePair attribute for forward and reverse trust indications. Trust can be unidirectional (one-way signing for limited interoperability) or bidirectional (mutual signing for symmetric reliance), with the certificate including basicConstraints to designate CA status and keyUsage extensions specifying digitalSignature and cRLSign permissions. During validation, relying parties construct paths using these cross-certificates, applying algorithm constraints and revocation checks as per PKIX profiles.[54] Key challenges in cross-certification include policy mapping, where the issuing CA must explicitly map the subject's certificate policies to its own via the policyMappings extension to avoid assurance dilution across domains, and constraint enforcement, such as nameConstraints and pathLenConstraint, to halt transitive trust propagation that could lead to unauthorized certificate acceptance. Failure to enforce these can result in "trust explosion," where indirect paths amplify risks; thus, standards mandate audit-approved mappings and periodic reviews by policy authorities.[53][54]Illustrative Examples
End-Entity Certificate
An end-entity certificate, also known as a leaf certificate, is the terminal node in an X.509 public key infrastructure (PKI) chain, issued to a specific entity such as a web server or user for purposes like authentication and key exchange in protocols such as TLS. Unlike intermediate or root certificates, it lacks the authority to issue other certificates, enforced by the basicConstraints extension set to CA:FALSE. These certificates bind a public key to an identity, typically a domain name, and are validated against the issuer's chain to establish trust.[27] For a web server deployment, an end-entity certificate might identify the domain example.com with a Subject Alternative Name (SAN) extension including DNS:www.example.com, enabling secure HTTPS connections. The certificate is signed by an intermediate CA, ensuring it cannot serve as a signing authority itself. To complete the trust chain, it relies on intermediate and root certificates provided separately during TLS handshakes.[31] A representative example of an end-entity certificate in PEM format for a web server is as follows (adapted from standard structures in RFC 5280 for illustrative purposes; actual certificates vary by issuer):-----BEGIN CERTIFICATE-----
MIID... (base64-encoded DER data)
...
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIID... (base64-encoded DER data)
...
-----END CERTIFICATE-----
- Serial Number: A unique positive integer assigned by the issuing CA to distinguish this certificate, e.g., 18 (in decimal) or 12 (in hex). This ensures uniqueness within the CA's scope and aids in revocation tracking.[14]
- Issuer: The distinguished name (DN) of the intermediate CA that signed the certificate, e.g., CN=Example Intermediate CA, DC=example, DC=com. This links the certificate to its signer in the PKI hierarchy.[16]
- Validity Period: The time range during which the certificate is valid, e.g., Not Before: 2025-01-01 00:00:00 UTC, Not After: 2025-12-31 23:59:59 UTC. Certificates outside this period are considered expired and rejected.[17]
- Subject: The DN of the end entity, e.g., CN=example.com, DC=example, DC=com. For web servers, the Common Name (CN) typically matches the primary domain.[24]
- Subject Public Key Info: The public key of the end entity and its algorithm, e.g., ECDSA with the prime256v1 (P-256) curve, including the key parameters and the encoded public key point. This key is used for TLS operations like signature verification or key agreement.[18]
- Basic Constraints: Set to CA:FALSE, explicitly prohibiting the certificate from acting as a CA to issue subordinate certificates. This is critical for end-entity security.[27]
- Key Usage: Limited to digitalSignature, permitting the key for signing TLS handshakes, but not for certificate signing or other purposes.[28]
- Extended Key Usage (EKU): Includes serverAuth (OID 1.3.6.1.5.5.7.3.1), restricting the certificate to TLS server authentication scenarios.[29]
- Subject Alternative Name (SAN): Lists additional identifiers, e.g., DNS:www.example.com, allowing the certificate to secure multiple hostnames without relying solely on the CN.[31]
openssl x509 -in example.com.pem -text -noout. This outputs a human-readable rendition of all fields, extensions, and the signature algorithm (e.g., ecdsa-with-SHA256), verifying the structure without altering the file.[56]
Intermediate and Root Certificates
Intermediate and root certificates form the backbone of trust delegation in X.509 public key infrastructures, allowing root certificate authorities to issue subordinate certificates that extend trust without compromising the root key's security. Root certificates are self-signed and serve as the ultimate trust anchors, pre-installed in operating system and browser trust stores to bootstrap validation chains. They typically feature minimal extensions, long validity periods (often 10–20 years or more), and critical flags designating them as CAs to enable signing capabilities.[57] A real-world example is the ISRG Root X1 certificate from the Internet Security Research Group (ISRG), which underpins Let's Encrypt's operations. This self-signed root has issuer and subject both set to "O=Internet Security Research Group, CN=ISRG Root X1", a 20-year validity from June 4, 2015, to June 4, 2035, basicConstraints with cA=TRUE (no pathLenConstraint), and keyUsage restricted to certificateSign and cRLSign. It includes an authorityKeyIdentifier matching its own subjectKeyIdentifier for self-consistency, though roots often omit explicit AKID since they are not chained further. The full PEM representation is:-----BEGIN CERTIFICATE-----
MIIFazCCA1OgAwIBAgIRAIIQz7DSQONZRGPgu2OCiwAwDQYJKoZIhvcNAQELBQAw
TzELMAkGA1UEBhMCVVMxKTAnBgNVBAoTIEludGVybmV0IFNlY3VyaXR5IFJlc2Vh
cmNoIEdyb3VwMRUwEwYDVQQDEwxJU1JHIFJvb3QgWDEwHhcNMTUwNjA0MTEwNDM4
WhcNMzUwNjA0MTEwNDM4WjBPMQswCQYDVQQGEwJVUzEpMCcGA1UEChMgSW50ZXJu
ZXQgU2VjdXJpdHkgUmVzZWFyY2ggR3JvdXAxFTATBgNVBAMTDElTUkcgUm9vdCBY
MTCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAK3oJHP0FDfzm54rVygc
h77ct984kIxuPOZXoHj3dcKi/vVqbvYATyjb3miGbESTtrFj/RQSa78f0uoxmyF+
0TM8ukj13Xnfs7j/EvEhmkvBioZxaUpmZmyPfjxwv60pIgbz5MDmgK7iS4+3mX6U
A5/TR5d8mUgjU+g4rk8Kb4Mu0UlXjIB0ttov0DiNewNwIRt18jA8+o+u3dpjq+sW
T8KOEUt+zwvo/7V3LvSye0rgTBIlDHCNAymg4VMk7BPZ7hm/ELNKjD+Jo2FR3qyH
B5T0Y3HsLuJvW5iB4YlcNHlsdu87kGJ55tukmi8mxdAQ4Q7e2RCOFvu396j3x+UC
B5iPNgiV5+I3lg02dZ77DnKxHZu8A/lJBdiB3QW0KtZB6awBdpUKD9jf1b0SHzUv
KBds0pjBqAlkd25HN7rOrFleaJ1/ctaJxQZBKT5ZPt0m9STJEadao0xAH0ahmbWn
OlFuhjuefXKnEgV4We0+UXgVCwOPjdAvBbI+e0ocS3MFEvzG6uBQE3xDk3SzynTn
jh8BCNAw1FtxNrQHusEwMFxIt4I7mKZ9YIqioymCzLq9gwQbooMDQaHWBfEbwrbw
qHyGO0aoSCqI3Haadr8faqU9GY/rOPNk3sgrDQoo//fb4hVC1CLQJ13hef4Y53CI
rU7m2Ys6xt0nUW7/vGT1M0NPAgMBAAGjQjBAMA4GA1UdDwEB/wQEAwIBBjAPBgNV
HRMBAf8EBTADAQH/MB0GA1UdDgQWBBR5tFnme7bl5AFzgAiIyBpY9umbbjANBgkq
hkiG9w0BAQsFAAOCAgEAVR9YqbyyqFDQDLHYGmkgJykIrGF1XIpu+ILlaS/V9lZL
ubhzEFnTIZd+50xx+7LSYK05qAvqFyFWhfFQDlnrzuBZ6brJFe+GnY+EgPbk6ZGQ
3BebYhtF8GaV0nxvwuo77x/Py9auJ/GpsMiu/X1+mvoiBOv/2X/qkSsisRcOj/KK
NFtY2PwByVS5uCbMiogziUwthDyC3+6WVwW6LLv3xLfHTjuCvjHIInNzktHCgKQ5
ORAzI4JMPJ+GslWYHb4phowim57iaztXOoJwTdwJx4nLCgdNbOhdjsnvzqvHu7Ur
TkXWStAmzOVyyghqpZXjFaH3pO3JLF+l+/+sKAIuvtd7u+Nxe5AW0wdeRlN8NwdC
jNPElpzVmbUq4JUagEiuTDkHzsxHpFKVK7q4+63SM1N95R1NbdWhscdCb+ZAJzVc
oyi3B43njTOQ5yOf+1CceWxG1bQVs5ZufpsMljq4Ui0/1lvh+wjChP4kqKOJ2qxq
4RgqsahDYVvTH9w7jXbyLeiNdd8XM2w9U/t7y0Ff/9yi0GE44Za4rF2LN9d11TPA
mRGunUHBcnWEvgJBQl9nJEiU0Zsnvgc/ubhPgXRR4Xq37Z0j4r7g1SgEEzwxA57d
emyPxgcYxn/eR44/KJ4EBs+lVDR3veyJm+kXQ99b21/+jh5Xos1AnX5iItreGCc=
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIFazCCA1OgAwIBAgIRAIIQz7DSQONZRGPgu2OCiwAwDQYJKoZIhvcNAQELBQAw
TzELMAkGA1UEBhMCVVMxKTAnBgNVBAoTIEludGVybmV0IFNlY3VyaXR5IFJlc2Vh
cmNoIEdyb3VwMRUwEwYDVQQDEwxJU1JHIFJvb3QgWDEwHhcNMTUwNjA0MTEwNDM4
WhcNMzUwNjA0MTEwNDM4WjBPMQswCQYDVQQGEwJVUzEpMCcGA1UEChMgSW50ZXJu
ZXQgU2VjdXJpdHkgUmVzZWFyY2ggR3JvdXAxFTATBgNVBAMTDElTUkcgUm9vdCBY
MTCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAK3oJHP0FDfzm54rVygc
h77ct984kIxuPOZXoHj3dcKi/vVqbvYATyjb3miGbESTtrFj/RQSa78f0uoxmyF+
0TM8ukj13Xnfs7j/EvEhmkvBioZxaUpmZmyPfjxwv60pIgbz5MDmgK7iS4+3mX6U
A5/TR5d8mUgjU+g4rk8Kb4Mu0UlXjIB0ttov0DiNewNwIRt18jA8+o+u3dpjq+sW
T8KOEUt+zwvo/7V3LvSye0rgTBIlDHCNAymg4VMk7BPZ7hm/ELNKjD+Jo2FR3qyH
B5T0Y3HsLuJvW5iB4YlcNHlsdu87kGJ55tukmi8mxdAQ4Q7e2RCOFvu396j3x+UC
B5iPNgiV5+I3lg02dZ77DnKxHZu8A/lJBdiB3QW0KtZB6awBdpUKD9jf1b0SHzUv
KBds0pjBqAlkd25HN7rOrFleaJ1/ctaJxQZBKT5ZPt0m9STJEadao0xAH0ahmbWn
OlFuhjuefXKnEgV4We0+UXgVCwOPjdAvBbI+e0ocS3MFEvzG6uBQE3xDk3SzynTn
jh8BCNAw1FtxNrQHusEwMFxIt4I7mKZ9YIqioymCzLq9gwQbooMDQaHWBfEbwrbw
qHyGO0aoSCqI3Haadr8faqU9GY/rOPNk3sgrDQoo//fb4hVC1CLQJ13hef4Y53CI
rU7m2Ys6xt0nUW7/vGT1M0NPAgMBAAGjQjBAMA4GA1UdDwEB/wQEAwIBBjAPBgNV
HRMBAf8EBTADAQH/MB0GA1UdDgQWBBR5tFnme7bl5AFzgAiIyBpY9umbbjANBgkq
hkiG9w0BAQsFAAOCAgEAVR9YqbyyqFDQDLHYGmkgJykIrGF1XIpu+ILlaS/V9lZL
ubhzEFnTIZd+50xx+7LSYK05qAvqFyFWhfFQDlnrzuBZ6brJFe+GnY+EgPbk6ZGQ
3BebYhtF8GaV0nxvwuo77x/Py9auJ/GpsMiu/X1+mvoiBOv/2X/qkSsisRcOj/KK
NFtY2PwByVS5uCbMiogziUwthDyC3+6WVwW6LLv3xLfHTjuCvjHIInNzktHCgKQ5
ORAzI4JMPJ+GslWYHb4phowim57iaztXOoJwTdwJx4nLCgdNbOhdjsnvzqvHu7Ur
TkXWStAmzOVyyghqpZXjFaH3pO3JLF+l+/+sKAIuvtd7u+Nxe5AW0wdeRlN8NwdC
jNPElpzVmbUq4JUagEiuTDkHzsxHpFKVK7q4+63SM1N95R1NbdWhscdCb+ZAJzVc
oyi3B43njTOQ5yOf+1CceWxG1bQVs5ZufpsMljq4Ui0/1lvh+wjChP4kqKOJ2qxq
4RgqsahDYVvTH9w7jXbyLeiNdd8XM2w9U/t7y0Ff/9yi0GE44Za4rF2LN9d11TPA
mRGunUHBcnWEvgJBQl9nJEiU0Zsnvgc/ubhPgXRR4Xq37Z0j4r7g1SgEEzwxA57d
emyPxgcYxn/eR44/KJ4EBs+lVDR3veyJm+kXQ99b21/+jh5Xos1AnX5iItreGCc=
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIFYDCCBEigAwIBAgISA2xUYj32x6FV ...
-----BEGIN CERTIFICATE-----
MIIFYDCCBEigAwIBAgISA2xUYj32x6FV ...
Standards Evolution
ITU-T and ISO Frameworks
The ITU-T X.509 recommendation, initially published in November 1988 as part of the X.500 series on directory services, established the foundational framework for authentication using public-key certificates within open systems interconnection (OSI) environments. This first edition (version 1) defined basic certificate structures, including a sequence of version, serial number, signature algorithm, issuer name, validity period, subject name, subject public key, and issuer signature, primarily for simple authentication in directory-based systems. The 1993 edition (version 2) introduced unique identifiers for issuers and subjects to support certificate set operations and revocation, enhancing management in distributed directory environments. By the 1997 edition (version 3), significant expansions included optional extensions for certificates and certificate revocation lists (CRLs), allowing customization for diverse applications such as key usage restrictions and policy information.[63] Subsequent updates refined these foundations: Attribute certificates were introduced in the 1997 edition, while the 2005 and 2008 editions added support for qualified certificates, time-stamping protocols, and enhanced directory access mechanisms, addressing evolving needs for non-repudiation and privilege attribution. The 2019 edition consolidated frameworks for public-key infrastructure (PKI) and privilege management infrastructure (PMI), incorporating protections against quantum computing threats and clarifying interactions with directory services, with subsequent corrigenda in 2021 and 2023, and Amendment 1 in 2024 further supporting advanced cryptographic algorithms, while maintaining backward compatibility with prior versions.[63] These evolutions reflect ITU-T Study Group 17's ongoing alignment with global security standards, ensuring X.509's role in secure information exchange across telecommunications networks. Parallel to ITU-T efforts, the International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) adopted X.509 as ISO/IEC 9594-8, synchronizing content through joint development to promote international interoperability.[63] This equivalent standard, first aligned in the early 1990s and updated through its ninth edition in 2020, mirrors ITU-T revisions, including version 3 extensions and PMI components, while integrating with the broader ISO/IEC 9594 series on directory services, and updated through corrigenda in 2021 and 2024, and Amendment 1 in 2025. The dual numbering facilitates adoption in both telecommunications and information technology sectors, with ISO/IEC 9594-8 emphasizing open systems for certificate-based authentication. X.509 is deeply integrated with the X.500 directory standards, leveraging directory services for certificate storage, retrieval, and validation via protocols like Directory Access Protocol (DAP) and Directory System Agent Protocol (DSAP). In this model, certificates are stored as directory entries, enabling users to query issuers, subjects, and revocation status through hierarchical directory information trees, which supports scalable PKI operations in enterprise and global networks.[64] This integration allows authentication services to be provided directly by the directory, reducing reliance on separate infrastructures.[65] Attribute certificates in X.509, introduced in version 3 and expanded in later editions, provide a distinct structure from public-key certificates to bind permissions and roles to an entity without altering the underlying public key. Defined as an AC SEQUENCE, an attribute certificate includes fields for holder (identifying the subject via public-key certificate reference or name), issuer (with serial number and signature algorithm), validity period, attributes (such as roles or clearances), and issuer signature, enabling flexible authorization separate from authentication. This separation allows multiple attribute certificates per public-key certificate, supporting dynamic privilege assignment in directory environments. The Privilege Management Infrastructure (PMI) extends X.509 to manage authorizations through attribute certificates, forming a hierarchy of attribute authorities analogous to certification authorities in PKI.[63] Introduced in the 2000 edition and refined through 2019, PMI uses attribute certificates for role-based access control, where privileges are encoded as attributes verifiable against policies in the directory. This framework supports delegation, revocation via attribute CRLs, and integration with X.500 for querying privilege paths, enabling scalable, interoperable permission systems in secure distributed applications.IETF PKIX Contributions
The Public-Key Infrastructure X.509 (PKIX) Working Group was chartered by the Internet Engineering Task Force (IETF) in the fall of 1995 to develop standards supporting X.509-based public key infrastructures tailored for Internet protocols over TCP/IP networks.[66] This initiative addressed the need to adapt the ITU-T X.509 framework for practical deployment in distributed, open environments like the Internet, focusing on certificate formats, management protocols, and validation procedures compatible with TCP/IP.[7] A foundational contribution was RFC 2459, published in January 1999, which provided the first comprehensive profile of X.509 version 3 certificates and version 2 certificate revocation lists (CRLs) for Internet use.[7] This profile specified mandatory and optional extensions, encoding rules, and processing algorithms to ensure interoperability among diverse implementations. Subsequent updates refined these profiles; notably, RFC 5280 from October 2008 updated the certificate and CRL profile, introducing detailed algorithms for certification path validation and support for certificate policies to enforce trust relationships across paths.[3] RFC 6818, issued in November 2012, further enhanced the profile by clarifying the application of name constraints extensions, ensuring that subordinate certificates adhere to permitted or excluded name spaces to prevent unauthorized delegation.[67] Additionally, RFC 7299 established an IANA registry for object identifiers (OIDs) under the PKIX arc (1.3.6.1.5.5.7), enabling systematic allocation and management of OIDs for extensions, algorithms, and policy identifiers to promote standardization and avoid collisions.[68] PKIX contributions also standardized mechanisms for expressing certificate policies (CPs) and certification practice statements (CPSs), which define the assurance levels and operational practices of certification authorities. RFC 2527, from March 1999, outlined a framework for authoring CPs and CPSs, including syntax for policy qualifiers and user notices to convey compliance requirements.[69] This was updated in RFC 3647 (November 2003), which refined the structure for better alignment with X.509 extensions like certificatePolicies (OID 2.5.29.32), allowing issuers to embed policy OIDs that indicate specific assurance levels, such as basic or high assurance for authentication or signing. These policies enable relying parties to assess the suitability of certificates based on verifiable claims about the issuer's processes. Recent PKIX efforts under the successor LAMPS Working Group have focused on efficiency and emerging use cases. RFC 9618, published in August 2024, updates the policy validation algorithm in RFC 5280 with a more efficient graph-based approach that reduces computational overhead while preserving equivalence in outcomes, addressing scalability issues in large certificate chains.[70] For certificate management, the update to the Certificate Management Protocol (CMP) in RFC 9810 (July 2025) modernizes RFC 4210 by incorporating post-quantum cryptography support, improved error handling, and alignments with current X.509 profiles for secure enrollment and revocation over the Internet.[71] In the realm of extended key usage (EKU) extensions, RFC 9734 (February 2025) defines a new KeyPurposeId for Instant Messaging (IM) URIs (OID 1.3.6.1.5.5.7.3.XX), enabling certificates to explicitly authorize keys for securing IM identities and communications in protocols like MLS.[72] These advancements ensure X.509 remains robust for Internet-scale applications, such as TLS integrations.Applications
Integration in Major Protocols
X.509 certificates are integral to the Transport Layer Security (TLS) protocol, where they serve as the primary mechanism for server and client authentication during the handshake process, enabling secure communication in applications such as HTTPS. In TLS versions like 1.2 and 1.3, the protocol relies on X.509 public key infrastructure (PKI) profiles to validate certificate chains, ensuring mutual authentication and key exchange.[3] In the Internet Protocol Security (IPsec) suite, particularly through the Internet Key Exchange version 2 (IKEv2) protocol, X.509 certificates provide authentication for VPN peers by verifying identities during the security association establishment. IKEv2 supports certificate-based authentication as an alternative to pre-shared keys, allowing for scalable deployment in enterprise networks.[73] Secure/Multipurpose Internet Mail Extensions (S/MIME) employs X.509 certificates for signing and encrypting email messages, associating user identities with public keys to ensure message integrity and confidentiality. The S/MIME v4.0 standard specifies conventions for certificate usage, including key management and signer identification, to facilitate secure email exchange.[74] The Secure Shell (SSH) protocol, as implemented in OpenSSH, offers optional support for X.509 certificates through public key infrastructure integration, enabling certificate-based authentication in place of traditional key pairs for remote access. This approach leverages PKI to enforce access controls without native X.509 parsing in core OpenSSH, often via external modules. In identity federation protocols like Security Assertion Markup Language (SAML) and OAuth, X.509 certificates underpin trust relationships between identity providers and service providers, as seen in implementations such as Shibboleth. These certificates sign assertions and enable secure token exchange, supporting single sign-on across domains. Microsoft's Certificate-Based Authentication (CBA) in Active Directory has undergone changes outlined in KB5014754, with full enforcement mode activated starting February 11, 2025, to strengthen mapping between X.509 certificates and user principals using enhanced security identifiers. This update mandates stricter certificate validation on domain controllers to mitigate impersonation risks.[75] Additionally, protocols such as Enrollment over Secure Transport (EST) utilize X.509 certificates for automated client enrollment in PKI systems, providing a secure HTTP-based method for certificate request and issuance. In wireless networks, Extensible Authentication Protocol-Transport Layer Security (EAP-TLS) relies on X.509 certificates for mutual authentication between devices and access points, ensuring secure Wi-Fi associations in enterprise environments.[76][77]Common Deployment Scenarios
In the Web Public Key Infrastructure (PKI), the CA/Browser Forum's Baseline Requirements define mandatory standards for issuing and managing X.509 certificates used in TLS server authentication, including validation methods, cryptographic algorithms, and validity periods to ensure interoperability and security across global certificate authorities.[78] These requirements have driven widespread adoption, with automation tools like Let's Encrypt utilizing the Automated Certificate Management Environment (ACME) protocol to enable seamless, free issuance of X.509 certificates for domain-validated TLS, supporting over 300 million active certificates and facilitating HTTPS deployment on millions of websites.[79][80] Enterprise PKI deployments commonly rely on Microsoft's Active Directory Certificate Services (AD CS), which integrates with Windows environments to issue and manage internal X.509 certificates for authentication, encryption, and access control, such as securing device enrollment in VPNs, wireless networks, and IPsec policies without requiring external public CAs.[81] For Internet of Things (IoT) and mobile ecosystems, X.509 certificates are adapted for resource-constrained devices through short-lived validity periods—often hours to days—to reduce key storage needs and mitigate compromise risks, while standards like Matter employ device attestation certificates (DACs) for secure commissioning and mutual authentication in smart home networks.[82][83] In government and federal contexts, the United States Federal PKI (FPKI) enforces X.509 policies through the Federal Bridge Certification Authority, with 2023 updates clarifying audit and archival obligations for assigning trusted roles—such as auditors and administrators—to enhance accountability and compliance in cross-agency certificate trust.[53] Recent trends in X.509 deployments include the CA/B Forum's enforcement of a maximum 398-day validity period for TLS certificates, effective September 30, 2020, aimed at limiting exposure from key compromises, alongside mandatory Certificate Transparency logging per RFC 6962 to publicly audit issuances and detect anomalies. In April 2025, the CA/B Forum approved a phased reduction of the maximum validity period to 47 days, to be fully enforced by March 15, 2029.[78][84][51] The migration away from SHA-1 signatures in TLS certificates, deprecated by major browsers since 2017, is now fully complete across public infrastructures, with all new issuances using SHA-256 or stronger hashes.[85] A key challenge in these scenarios is managing issuance at scale, as public CAs like Let's Encrypt alone produce hundreds of millions of TLS certificates annually, necessitating robust automation to handle renewals, revocations, and monitoring without disrupting services.[80]Security Considerations
Architectural and Systemic Weaknesses
The X.509 public key infrastructure (PKI) employs a centralized trust model anchored by a limited set of root Certificate Authorities (CAs) pre-installed in client trust stores, which introduces significant single points of failure. A compromise of even one root CA can undermine trust across the entire hierarchy of certificates it validates, potentially enabling man-in-the-middle attacks on a global scale, as seen in historical incidents like the DigiNotar breach. This reliance on few trusted entities heightens systemic vulnerability, since the failure or malicious action of a root CA affects all dependent end-entity certificates without isolated containment.[86][87] Transitive trust in X.509 certificate chains exacerbates risks by propagating compromises along the path from root to end-entity certificates. In this model, validation assumes unbroken trust from the root anchor through intermediate CAs; thus, a breach at any intermediate level invalidates all downstream certificates, amplifying the attack surface in long chains common to complex PKIs. Such propagation can lead to widespread unauthorized access if revocation mechanisms lag, as relying parties inherit unvetted trust relationships without direct verification of each link's integrity.[88][89] X.509 lacks native mechanisms for transparent auditing of certificate issuance, permitting CAs to issue invalid or unauthorized certificates without immediate detection by domain owners or relying parties. This opacity allows misissuances—such as those for unrelated domains—to persist undetected, facilitating attacks until external monitoring reveals them. To mitigate this, external systems like Certificate Transparency (CT) were developed, mandating public logging of issuances for verifiable audits, though integration remains optional in the core standard.[90][91] Name constraints in X.509 certificates provide a mechanism to restrict subordinate CAs to specific namespaces, such as permitted DNS names, aiming to prevent over-issuance beyond authorized domains. However, these constraints are often non-critical and inconsistently enforced across implementations, reducing their reliability in blocking unauthorized certificates for subdomains. This limitation contributes to vulnerabilities like subdomain takeovers, where attackers exploit misconfigured DNS to claim subdomains without robust CA-level prevention, as name constraints do not fully address dynamic or wildcard scenarios.[92][3] The X.509 PKI exhibits fragmentation between global and national implementations, with inconsistent policies across jurisdictions leading to interoperability challenges and varying assurance levels. While international standards like those from ITU-T and IETF provide a framework, national regulations—such as eIDAS in the EU—impose divergent requirements on CA practices, certificate validation, and liability, resulting in policy silos that complicate cross-border trust. This disjointed landscape fosters uneven security postures, where certificates valid in one region may face rejection elsewhere due to mismatched certification practices.[93][94]Certification Authority Challenges
Certification Authorities (CAs) in X.509 public key infrastructures serve as critical trust anchors, but their operational vulnerabilities have repeatedly undermined the security of certificate ecosystems. These challenges arise from the centralized role CAs play in issuing and managing digital certificates, where a single point of failure can compromise widespread trust. Historical incidents and systemic issues highlight the fragility of this model, often stemming from inadequate security practices and insufficient oversight.[95] One prominent example of CA compromise is the 2011 DigiNotar breach, where intruders exploited vulnerabilities in the company's network to access CA servers and issue 531 rogue X.509 certificates, including for high-profile domains like *.google.com. This intrusion, undetected for nearly two months, enabled man-in-the-middle attacks affecting approximately 300,000 users, primarily in Iran, and led to the revocation of all DigiNotar certificates and the removal of its root certificates from major browser trust stores by vendors such as Mozilla. The incident, detailed in the official investigation known as the Black Tulip Report, exposed severe lapses in segmentation, logging, and intrusion detection, ultimately causing DigiNotar's bankruptcy.[96][95] Vetting failures further exacerbate risks, particularly with Domain Validated (DV) certificates, which require only proof of domain control without verifying the requester's identity or intent. This minimal process has enabled fraudsters to obtain valid X.509 certificates for phishing sites mimicking legitimate entities, such as "banskfamerica.com" issued by Comodo or "paypwil.com" by GoDaddy. In one month alone in 2015, CAs issued hundreds of such deceptive certificates for phishing domains, often through automated DV issuance that bypasses scrutiny for high-risk names despite CA/B Forum guidelines. The ease of acquiring low-cost DV certificates—sometimes free via services like Let's Encrypt—has fueled a surge in HTTPS phishing, with attacks using valid DV SSL certificates rising from 450 in 2005 to 47,500 in the first quarter of 2017.[97][98] Revocation mechanisms like Certificate Revocation Lists (CRLs) and Online Certificate Status Protocol (OCSP) suffer from inherent delays that hinder timely detection of compromises. Caching in OCSP and CRL distribution can postpone awareness of revocations by hours or days, allowing compromised X.509 certificates to remain usable. In analyses of PKI revocation effectiveness, average delays from malware detection to published revocation exceeded 171 days for some certificates, with additional issues like missing OCSP endpoints or inconsistent responses affecting up to 788 cases in code-signing scenarios applicable to broader CA failures. These latencies amplify the window for abuse following a CA breach.[99][100] Market concentration among a few dominant CAs heightens systemic risks, as a compromise in one can cascade across the X.509 ecosystem. In 2023, the certificate authority market was valued at approximately USD 167-173 million, with key players like Sectigo and DigiCert holding significant shares alongside others such as GoDaddy and GlobalSign; usage trends showed Sectigo at around 6% and DigiCert at 2% of active SSL certificates, underscoring reliance on a limited set of providers. This oligopoly, where fewer than 10 CAs issue most web certificates, means that failures in vetting or security at these entities can erode trust on a global scale.[101][102][103] Policy inconsistencies across CAs, as outlined in their Certificate Policies (CPs) and Certification Practice Statements (CPSs), contribute to uneven trust assurance. Variations in implementation, such as differing approaches to risk assessment or auditing, have been noted in federal oversight; the 2023 Federal PKI (FPKI) audit identified four discrepancies in the CPS traceability to CP requirements for the FPKI Managing Authority, prompting clarifications to align practices more closely. These gaps in standardization can lead to divergent security postures among CAs, complicating reliance on X.509 certificates.[104] Finally, mitigation gaps persist due to the absence of mandatory liability for CA errors, leaving relying parties with limited recourse. While some CAs like Sectigo and Microsoft include liability limitations in their CPS—capping responsibility to insurance policy amounts or excluding certain damages—there is no universal requirement for accountability or insurance in X.509 PKI frameworks, as highlighted in surveys of PKI failures. This lack of enforceable liability discourages robust risk management and shifts the burden to end-users, perpetuating vulnerabilities in the trust model.[105][106]Implementation and Cryptographic Risks
Implementation issues in X.509 certificate handling have led to significant vulnerabilities, particularly in parsing and validation processes. A notable example is the Heartbleed bug in OpenSSL (CVE-2014-0160), discovered in 2014, which allowed attackers to read server memory, potentially exposing private keys used in TLS sessions secured by X.509 certificates.[107] More directly related to X.509, buffer overflow vulnerabilities in OpenSSL's X.509 certificate validation, such as those in versions prior to 1.1.1n, enabled denial-of-service attacks or potential code execution during certificate parsing.[108] Path validation bugs have also been prevalent; for instance, improper handling of critical extensions in certificate chains can cause verifiers to accept invalid paths, as demonstrated in symbolic execution analyses of SSL/TLS libraries where bugs allowed bypassing revocation checks or name constraints.[109] These issues often stem from complex ASN.1 decoding and extension processing, with real-world implementations showing inconsistent behavior across libraries like OpenSSL, Bouncy Castle, and NSS.[110] Cryptographic weaknesses in X.509 arise from the use of deprecated or vulnerable algorithms in signatures and keys. MD5 and SHA-1 hashing algorithms, once common in X.509 certificates, have been phased out due to collision vulnerabilities; for example, Microsoft ended SHA-1 support in root certificates by 2016, and RFC 9155 formally deprecated MD5 and SHA-1 in TLS handshakes by 2021.[111][112] RSA-1024 keys, widely used until the early 2010s, were deemed weak by NIST in 2013, with support disallowed after December 31, 2013, due to feasible factorization attacks.[113] For elliptic curve cryptography, ECDSA implementations in X.509 have faced concerns over potential biases in NIST-recommended curves like P-256, stemming from revelations of NSA influence that raised fears of embedded backdoors similar to those in Dual_EC_DRBG, a flawed random number generator standardized by NIST in 2006.[114] Although no direct backdoor has been proven in ECDSA curves, these issues have prompted recommendations to prefer verified curves like Curve25519 for new deployments.[115] Quantum computing poses existential threats to X.509's core primitives, as Shor's algorithm can efficiently factor large integers and solve discrete logarithms, breaking RSA and ECDSA signatures used in certificates.[116] A sufficiently large quantum computer could forge X.509 signatures or derive private keys from public ones in polynomial time, undermining the entire PKI ecosystem.[117] NIST's ongoing post-quantum cryptography (PQC) standardization addresses this through new object identifiers (OIDs) for quantum-resistant algorithms, enabling their integration into X.509 structures like hybrid certificates that combine classical and PQC keys.[118] Mitigations for these risks emphasize algorithm agility and upgrades within the X.509 framework. The signatureAlgorithm field in X.509 certificates, defined in RFC 3279, allows flexible specification of signature schemes, facilitating transitions to stronger algorithms without structural changes.[119] Post-quantum signatures, such as Leighton-Micali Signature (LMS) outlined in RFC 8554, are supported via dedicated OIDs for X.509, enabling stateful hash-based schemes resistant to quantum attacks.[120][121] Additionally, regular increases in key sizes—such as mandating RSA-2048 as the minimum since around 2013—provide interim protection against classical threats, with NIST recommending 2048 bits or larger for ongoing security.[122] In 2024, Microsoft updated Windows Certificate-Based Authentication (CBA) policies to enforce stronger certificate requirements, including deprecation of weak RSA keys under 2048 bits in TLS server authentication and enhanced strong mapping to prevent weak certificate acceptance in domain controllers.[123][75] These changes, effective via updates like KB5014754, aim to mitigate legacy vulnerabilities in enterprise PKI deployments.References
Summary of X.509 Standard
- The X.509 public-key certificate or the X.509 attribute certificate, as defined by the ISO/ITU-T X.509 standard.
- RFC 5280 profiles X.509 v3 certificates and X.509 v2 CRLs for the Internet, part of the Internet PKI standards, and describes certification path processing.
