Recent from talks
Nothing was collected or created yet.
Phantom OS
View on Wikipedia
| Phantom OS | |
|---|---|
 OS Phantom screenshot for 17 October 2019 | |
| Developer | Digital Zone |
| Written in | C, Phantom, Java |
| OS family | RTOS |
| Working state | Active |
| Source model | FOSS |
| Latest release | latest / October 17, 2019 |
| Repository | github |
| Available in | Russian, English |
| Supported platforms | IA-32 |
| Kernel type | Microkernel |
| License | LGPL |
| Official website | phantomos |
Phantom OS is an orthogonally persistent managed code general-purpose operating system. It is based on a concept of persistent virtual memory, and executes bytecode in a virtual machine. It is one of a few OSes not based on the classic concepts of Unix-like systems. Phantom is based on the principle that "Everything is an object", in contrast to the Unix-like approach of "Everything is a file".[1]
Overview
[edit]Phantom was founded by Dmitry Zavalishin[1] and is being developed mostly by Russian programmers. It is free and open-source software (FOSS) released under a GNU Lesser General Public License (LGPL).
Basics
[edit]Managed code – Memory protection on object level, rather than process level; absence of pointer arithmetic in managed code avoids many problems that exist and occur in unmanaged code.[2]
Global address space – Inexpensive inter-process communication (IPC). Single (flat) address space allows transfer of objects from one process (application) to another by transferring links to that object. Security is achieved by the absence of pointer arithmetic and the inability of an application to get linked to an object other than by calling a public method.[2]
Persistence – Application code does not see OS restarts and can live forever—this does not use the concept of a file and any variable or data structure can be stored forever and at the same time be available directly through a pointer. Contrary to hibernation, which is done in other OSs, persistence lies in the very core principles of the Phantom OS core. The implementation creates snapshots continuously and transparently to the applications maintaining consistent internal state without pausing applications.[1]
Compatibility
[edit]Two ways to migrate code are offered:[2]
- Converter from Java virtual machine (JVM) bytecode; is supposed to permit the import of bytecode from Java and other programming languages that target the JVM.
- The Portable Operating System Interface (POSIX) subsystem allows porting application code from Unix and Linux, although important features of Phantom OS such as persistence become unavailable.
Status
[edit]As of October 2019[update], the system exists as an alpha version for x86 IA-32 processors. Porting to ARM architecture is underway (currently being tested, not yet ready for use) and porting to MIPS architecture and x86-64 (AMD64) has begun. Kernel operation has been demonstrated at the biggest Russian IT-conferences RIT 2011, ADD 2010,[3] CC 2010,[4] and 2009.
See also
[edit]References
[edit]- ^ a b c Dziuba, Ted (3 February 2009). "Russian rides Phantom to OS immortality". The Register. Retrieved 27 April 2011.
The iPhone that never dies
- ^ a b c d "Прототип отечественной ОС Phantom на базе Genode будет готов до конца года". www.opennet.ru. 24 January 2022. Retrieved 9 November 2023.
- ^ Dmitry Zavalishin reports on ADD 2010 Archived 2012-07-07 at archive.today
- ^ Dmitry Zavalishin reports on Chaos Constructions’2010 (Saint-Petersburg, Russia) Archived 2012-03-23 at the Wayback Machine
Sources
[edit]- "Source codes of Phantom OS". Digital Zone. 2009. Retrieved 27 April 2011.
- "Phantom OS Internals book". 2019.
- "Phantom OS on OpenHUB". 2019.
External links
[edit]Phantom OS
View on GrokipediaIntroduction
Definition and Core Concept
Phantom OS is a general-purpose, object-oriented operating system designed around the principles of orthogonal persistence and managed code execution. It operates as a virtual machine within a vast persistent virtual memory, where all system data, code, and resources exist as objects in a single, global address space that remains intact across reboots, power failures, or other interruptions.[1] This architecture ensures that persistence is inherent to the system, without relying on explicit serialization or checkpointing mechanisms typically found in conventional operating systems.[6] The core concept of Phantom OS revolves around treating the entire operating environment as a seamless, persistent virtual machine that eliminates traditional file systems and disk-based storage hierarchies. Instead, all resources—ranging from kernel services to user applications—are stored directly in memory as manipulable objects, enabling direct sharing and communication between applications without intermediaries like files or processes. This design allows applications to resume their state instantaneously after any system halt, as if no disruption had occurred, fostering a model of computational continuity often described as "application immortality."[7][1] A distinctive feature of Phantom OS is the absence of a persistence boundary between kernel and user space; everything within the system is uniformly treated as a persistent object, in stark contrast to traditional models like Unix, where the paradigm of "everything is a file" separates volatile runtime states from durable storage. Orthogonal persistence underpins this uniformity, making object lifetime independent of program execution cycles. Initiated as an original operating system not derived from Linux or other Unix-like systems, Phantom OS prioritizes this object-centric persistence to enable long-lived, resilient applications.[1][8]Goals and Motivations
Phantom OS aims to provide an operating environment where applications can survive system reboots without losing state or requiring explicit serialization, enabling the development of "immortal" programs that resume operation seamlessly upon restart.[1] This design eliminates the need for traditional file systems and disk I/O operations for data persistence, allowing all application data to remain in a single, persistent address space that treats the entire system memory as durable.[9] By removing these conventional persistence mechanisms, Phantom OS simplifies resource management, reducing context switches and overhead associated with data transformation in standard operating systems.[10] The motivations for Phantom OS stem from the limitations of traditional OS architectures, such as state loss during reboots, data fragmentation in file-based storage, and the inefficiencies of object serialization for complex, interconnected data structures.[10] These issues often lead to significant developer effort—up to 30-75% of code dedicated to handling saves, loads, and recovery—complicating software maintenance and increasing error risks in long-running applications.[9] Phantom OS seeks to transform the operating system into an "application server" that facilitates direct sharing of persistent objects among programs, thereby streamlining inter-process communication and fostering a more efficient programming paradigm.[1] Key benefits include reduced development complexity, as programmers no longer need to manage explicit state persistence, allowing focus on core logic and potentially cutting costs by 30% or more.[9] This approach enhances reliability for embedded and wearable devices through efficient resource use and automatic state recovery, while supporting continuous operation in critical systems like medical or banking applications by ensuring instant restoration after power failures or crashes without lengthy reboots.[2] The philosophical basis of Phantom OS reflects Dmitry Zavalishin's vision of a "never-dying" persistent system, articulated in early 2000s discussions on redefining OS resilience to prioritize uninterrupted application lifecycles over traditional shutdown procedures.[10]History and Development
Origins and Early Development
Phantom OS originated as a personal research project initiated by Dmitry Zavalishin in the early 2000s, drawing inspiration from object-oriented programming paradigms and earlier research on persistent systems from the 1990s, particularly concepts of orthogonal persistence that enable uniform treatment of data across lifetimes without explicit save operations.[11] Zavalishin, a programmer with prior experience at Yandex from 2002 to 2005, envisioned Phantom as a way to eliminate traditional state loss during system reboots, addressing limitations in conventional OS architectures for applications requiring high reliability, such as medical and military software.[10] In August 2005, Zavalishin founded the software company Digital Zone, initially focused on scalable web-based systems.[12] Early development of Phantom OS transitioned to Digital Zone around 2010, where it was pursued as a foundational research effort. Initial implementations targeted the x86 (IA-32) architecture, with core components written in C to build a basic virtual machine capable of maintaining object states across power cycles.[3] These prototypes emphasized seamless persistence mechanisms, allowing programs to resume execution without data loss, in contrast to file-based storage in existing systems. The work was primarily conducted by a small team of Russian programmers at Digital Zone, operating initially as a proprietary research endeavor without external funding details publicly disclosed. By 2009, Phantom OS gained public attention through articles highlighting its "immortality" feature, where powering off the system preserves program states for immediate resumption upon restart.[10] This announcement marked the project's transition toward broader visibility, though core development remained internal to Digital Zone. Open-source elements were introduced later under the GNU Lesser General Public License (LGPL) version 3.0, facilitating community contributions while retaining the company's control over key components.[2]Key Milestones and Releases
Phantom OS saw its first public demonstrations in the late 2000s and early 2010s at major Russian IT conferences, showcasing the kernel's orthogonal persistence capabilities. A notable presentation occurred at the Application Developer Days (ADD) conference in 2010, where lead developer Dmitry Zavalishin discussed the system's design and demonstrated basic functionality, emphasizing how applications could survive reboots without explicit state management.[13] Similar demos were presented at Chaos Constructions events in 2009 and 2010, highlighting early prototypes focused on persistent virtual memory to illustrate the OS's core innovation of seamless state retention across power cycles.[1] During the 2010s, development progressed through internal betas centered on persistence demonstrations, with incremental improvements to the kernel and userland components available via the project's source repositories. These betas prioritized proving the viability of orthogonal persistence, allowing objects in memory to remain accessible post-reboot as if the system had never shut down. Contributions from collaborators, including Innopolis University, supported these efforts following the open-sourcing.[5] By late 2019, the project reached an alpha stage, providing a bootable system with a basic kernel implementing essential VM classes for low-level operations and initial userland support, including a bytecode execution environment compatible with Java virtual machine bytecode for importing applications from JVM-targeted languages.[7][6] This alpha also incorporated a simple POSIX compatibility subsystem to run legacy Unix-like applications, such as a Quake port, alongside native persistent components.[1] Post-alpha development has been sustained through the official GitHub repository, phantomuserland, where ongoing commits address stability, driver enhancements (e.g., SVGA support for VMWare and Parallels), and UI elements like TrueType fonts and controls with alpha blending.[3] In 2020, a fork integrating Phantom OS with the Genode framework was initiated to leverage Genode's modularity for improved component isolation and hardware support, using Genode's build system to embed Phantom's persistent kernel.[14] As of November 2025, activity persists with experiments in hardware portability, notably an active but unstable ARM port that compiles and boots minimally, alongside nascent MIPS support, reflecting efforts to expand beyond the primary IA-32 architecture.[3] These updates address persistence challenges, such as snapshot reliability tested over hundreds of cycles, while the project's documentation and source remain the primary avenues for community contributions.[15]Design Principles
Orthogonal Persistence
Orthogonal persistence in Phantom OS ensures that the entire virtual memory, including code, data, and execution state, remains automatically durable across system reboots or failures, independent of any program lifecycle events such as termination or restarts. This eliminates the need for explicit save or load operations, allowing applications to resume exactly where they left off without perceiving the interruption.[6] The core mechanism relies on a persistent virtual memory subsystem that captures continuous snapshots of the object graph, paging all memory contents to disk in a manner that preserves their in-memory form for full restoration on subsequent boots. Pointers to objects are maintained intact through a unified global address space, enabling direct referencing without serialization or remapping after recovery. This paging engine operates orthogonally to the virtual machine's bytecode execution, ensuring coherence even during abrupt power loss or crashes.[6][1] In Phantom OS, persistence is uniquely orthogonal to object types, applying equally to kernel-implemented internal objects and user-defined entities, in contrast to selective persistence models in databases that target only designated data structures. This uniform treatment integrates seamlessly with the system's object model, where all entities share the same addressable space.[6][1] Key advantages include simplified development, as programmers avoid managing files or explicit durability, and reboot-transparent operation that reduces setup overhead for user interfaces and data states. However, maintaining snapshot consistency requires locking the persistent memory during writes—via functions likevm_lock_persistent_memory() and vm_unlock_persistent_memory()—which can introduce thread delays and performance overhead if access patterns are not optimized. Uncontrolled paging may also lead to efficiency issues, necessitating disciplined memory design to prevent degradation.[6]
Object Model
Phantom OS employs a unified object-oriented paradigm where everything is an object, encompassing files, devices, processes, and kernel services, each equipped with methods and properties for interaction. This model eliminates distinctions between traditional system components, treating them uniformly as instances of classes within the operating system. Notably, there are no primitive types outside of objects; all data is encapsulated within this object structure, ensuring a consistent and type-safe environment.[16] The system utilizes a single global namespace for addressing, where objects are referenced directly via pointers in a global address space rather than conventional identifiers like file paths or process IDs (PIDs). This approach facilitates direct object sharing for inter-process communication (IPC), allowing applications to interact by passing references to mutable objects without the overhead of data copying, thereby enhancing efficiency and reducing latency. In contrast to microkernel designs such as seL4, which rely on message-passing for isolation, Phantom OS embraces shared mutable objects to promote seamless collaboration, while the managed environment prevents unauthorized access.[16][3] This object model has significant implications for development and system management. By unifying all resources under objects, it simplifies programming by abstracting away low-level details, enabling developers to focus on object interactions rather than managing disparate system elements. However, it necessitates automated memory management through garbage collection mechanisms, including fast reference counting for immediate deallocation and periodic mark-and-sweep cycles for comprehensive cleanup; note that the GC implementation is incomplete for large-scale 64-bit scenarios, such as 20 TB memory.[16][17][3] Additionally, objects support versioning, where multiple class versions coexist; newly created objects adopt the latest version, while existing ones retain their original implementation, allowing for evolutionary system updates without breaking compatibility. Orthogonal persistence is applied to these objects, ensuring their state survives reboots by storing them in a persistent virtual memory space.[16]System Architecture
Kernel Design
Phantom OS features a microkernel architecture that minimizes the core kernel's footprint while implementing essential low-level services through internal classes, enabling direct access to hardware and system resources without extensive abstraction layers. These internal classes, written in C, form the kernel's object-oriented foundation, handling critical operations such as thread management and interrupt processing. The design emphasizes modularity, with the kernel providing a small trusted computing base that supports preemptive multitasking, including priority-based scheduling and synchronization primitives like mutexes and semaphores.[6] A key aspect of the kernel is its hybrid integration with a bytecode virtual machine (PVM), which blurs traditional boundaries between kernel and user space by executing managed code directly in persistent memory. The kernel manages object creation using memory pools with reference counting, while the PVM oversees higher-level persistent objects, allowing applications to run as seamless extensions of the system without explicit serialization. Hardware abstraction is achieved through a driver subsystem that includes support for PCI enumeration, block devices, network interfaces, and graphics, all operating within the persistent environment. This hybrid approach eliminates conventional syscalls, replacing them with object invocations that maintain system coherence across operations.[6][3] Persistence is guaranteed at the kernel level via a paging engine that creates periodic snapshots of the entire virtual memory state, ensuring at least two copies are maintained on disk for fault tolerance. Upon reboot, the kernel restores the most recent valid snapshot, restarting non-persistent kernel components from scratch while reviving userland objects in their prior state, thus avoiding data loss from power failures or crashes. The architecture supports a global address space for inter-process communication via direct pointer access in managed code, enhancing efficiency over message-passing models.[6][18] The kernel's evolution began with a C-based implementation focused on x86 stability, later incorporating Java-like bytecode execution through the PVM for higher-level services and language support, including experimental ports to ARM, MIPS, and AMD64. A notable development is the Genode fork, which integrates Phantom's persistent model into the Genode framework to incorporate capability-based security mechanisms, enhancing isolation while preserving the core persistence features.[3][14]Memory and Persistence Mechanism
Phantom OS employs a virtual memory model centered on a huge, single address space that extends directly into persistent storage, such as SSD or NVMe drives, treating the entire system as a unified persistent RAM environment. This model leverages orthogonal persistence through transparent swapping, where all memory pages are paged to disk via a persistent paging engine, ensuring that the address space remains consistent and accessible across system restarts without traditional file system abstractions. The absence of a separate file system layer allows storage to function as a direct extension of memory, eliminating serialization overhead for data persistence.[1][6] The implementation relies on continuous checkpointing through asynchronous snapshots of the entire virtual memory, performed regularly without halting system operations or "stopping the world." These snapshots capture the state of object graphs in the persistent memory allocator, which manages allocation using dedicated arenas for object types, such as integers, to optimize storage. On boot or recovery, the system restores the last consistent snapshot, enabling applications to resume execution seamlessly as if no interruption occurred, with a syscall restart engine re-executing any pending system calls. Multiple snapshots (typically two or more) are maintained incrementally to support efficient backups and state preservation.[1][6][3] Coherence is maintained through a combination of object-level garbage collection and memory access controls during snapshotting. The system features two garbage collectors: a fast reference-counting mechanism for immediate cleanup and a slower mark-and-sweep collector for comprehensive traversal, both operating on persistent objects to prevent dangling pointers and ensure memory integrity. During snapshots, functions likevm_lock_persistent_memory() and vm_unlock_persistent_memory() restrict thread access to the persistent memory, guaranteeing a consistent state without concurrent modifications. This approach supports non-volatile memory (NVM) integration for accelerated persistence where available, enhancing overall reliability.[6][19]
To address challenges like power failures, Phantom OS uses atomic updates within the snapshot process and maintains redundant snapshots for recovery, allowing the system to revert to the most recent viable state upon abrupt shutdowns. This mechanism ensures data integrity and application continuity, with the kernel's persistent pager handling paging operations to mitigate risks from incomplete writes. No additional recovery protocols are needed beyond snapshot restoration, as the virtual memory model inherently avoids transient states vulnerable to crashes.[1][6]
Programming and Development
Supported Languages
Phantom OS primarily supports its native programming language, known as the Phantom language, which is an object-oriented language designed specifically for persistent programming environments. This language is compiled using the Phantom Language Compiler (PLC), producing bytecode that executes on the Phantom Virtual Machine (PVM). The Phantom language incorporates features for orthogonal persistence, allowing objects to remain active across system reboots without explicit serialization, and its syntax and structure draw parallels to managed languages like C# while extending them for seamless integration with the OS's persistent memory model.[6] In addition to the native Phantom language, the OS provides experimental support for other languages to broaden its development ecosystem. Java programs can be executed through an experimental bytecode translator that converts JVM class files to Phantom bytecode, though this implementation remains basic and incomplete. Python support is in preliminary stages, utilizing an AST connector to translate Python code into Phantom bytecode, enabling limited scripting capabilities within the persistent runtime. For low-level system components, such as kernel internals and drivers, C is used, with code compiled directly into the kernel space to interface with hardware and core services.[6][1][3] Programs in supported languages are compiled to either Phantom bytecode for managed execution or native objects for kernel-level code, eliminating traditional linking steps as objects are dynamically loaded directly into the OS's persistent virtual memory space. This process leverages the global address space, where applications share objects without file I/O for state management, ensuring data persistence across sessions. A key constraint is the prohibition on pointer arithmetic in userland languages to maintain memory safety and persistence integrity, enforced by the PVM. Furthermore, garbage collection is tightly integrated with the persistence mechanism, allowing automatic memory management while preserving object lifetimes indefinitely unless explicitly terminated. As of the latest available documentation and repository activity in 2023, these features remain experimental.[6][1]Development Tools and APIs
Phantom OS provides a specialized development environment tailored for persistence-aware programming, where applications operate within a persistent virtual memory space, eliminating the need for explicit state serialization or deserialization. Developers can write code that assumes data structures remain intact across system reboots, leveraging the operating system's orthogonal persistence model to focus on business logic rather than I/O management. This approach is facilitated by a toolchain that integrates compilation, building, and runtime execution directly with the persistent object store.[6] The primary compiler in the Phantom OS ecosystem is the Phantom Language Compiler (PLC), which handles native code generation for the system's proprietary Phantom programming language. PLC parses Phantom source code and produces bytecode executable by the kernel's virtual machine, enabling seamless integration with persistent objects. For broader language support, PLC includes translators for Java and Python, though these remain works in progress; Java code is adapted via a JVM class file loader that converts to Phantom-compatible bytecode, while Python uses preliminary AST processing for similar translation. These tools ensure that developers can port or write applications in familiar languages while benefiting from persistence. As of the latest available documentation and repository activity in 2023, these features remain experimental.[6][3] The build system uses Make, with the PHANTOM_HOME environment variable, for automated compilation and building of both kernel components and userland applications. This setup supports incremental builds that preserve object states across iterations, reducing development overhead in long-running projects.[6] At the core of application development are object-oriented APIs provided through the.internal and .phantom packages, which expose system services without relying on traditional system calls. Instead, developers invoke methods directly on kernel objects, such as creating persistent instances via Object.create() or handling events through EventQueue.process(). Examples include .internal.[window](/page/Window) for graphical interface management and .internal.tcp for network operations, all designed to operate transparently on persistent data. This method-based interface promotes a uniform programming model across user and kernel spaces, where persistence is inherent to object lifecycles.[6][19]
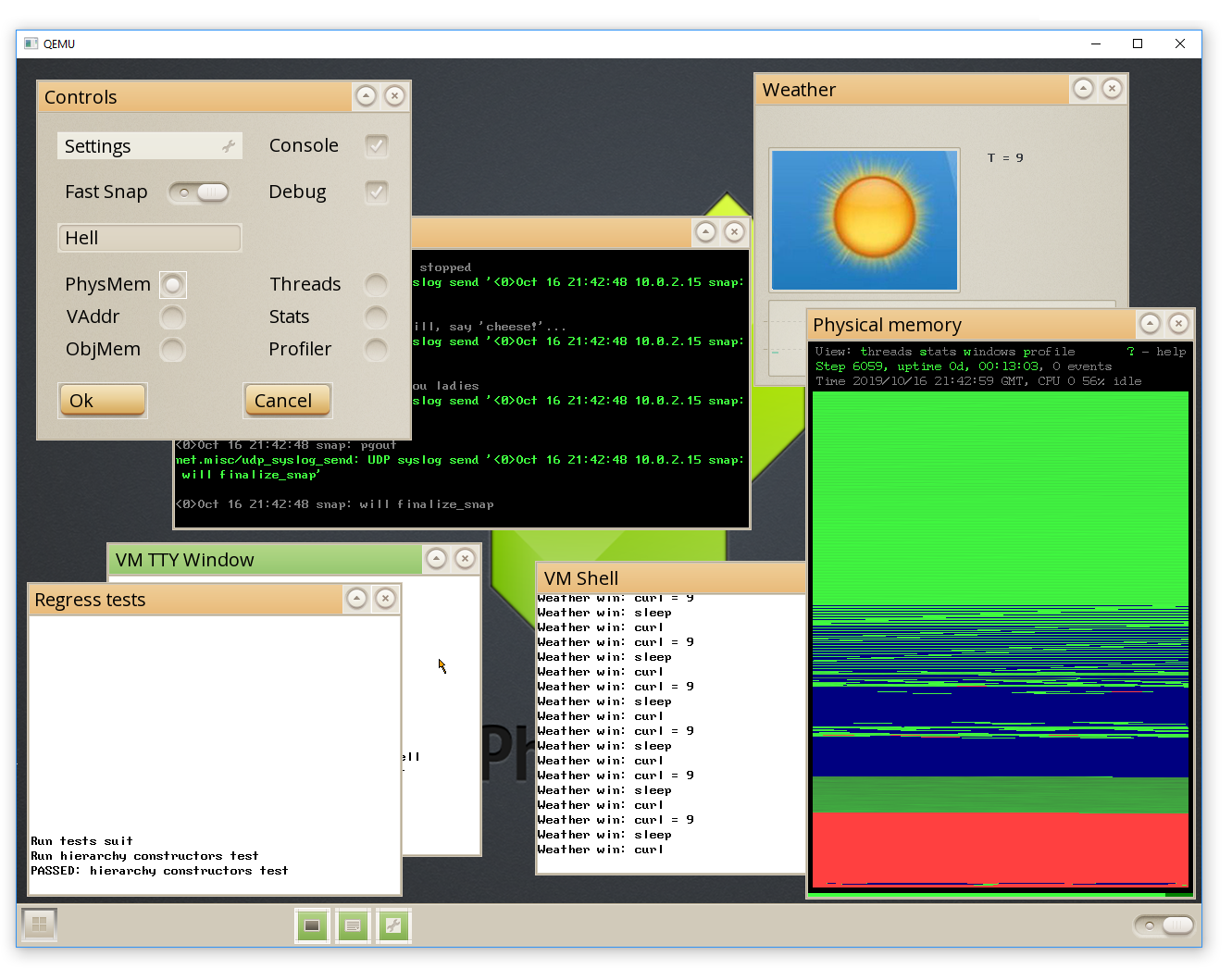
Debugging tools emphasize live inspection of persistent objects, with facilities like pvm_object_print and pvm_object_dump for runtime examination of memory states, complemented by logging macros such as LOG_FLOW for tracing execution flow and SHOW_ERROR for error reporting. There is no full-fledged integrated debugger akin to GDB, but these utilities allow developers to probe object graphs non-destructively, even across simulated reboots. For testing persistence behaviors, QEMU serves as the primary emulator, enabling isolated execution of Phantom OS images to verify state retention without hardware dependencies. Documentation is hosted on ReadTheDocs, offering comprehensive guides with code examples for both kernel modules and user applications, including persistence-specific patterns like snapshot-aware threading.[6][3]
Despite these capabilities, the ecosystem has notable gaps, including limited support for modern integrated development environments (IDEs), with most development occurring via command-line tools or basic editors. Community-driven extensions on GitHub address porting challenges, such as adapters for cross-compiling from standard toolchains, but official IDE integration remains underdeveloped. This reliance on lightweight, specialized tools aligns with Phantom OS's focus on simplicity and persistence but may pose a learning curve for developers accustomed to feature-rich environments. As of the latest available documentation and repository activity in 2023, these features remain experimental.[3][1]