Recent from talks
Contribute something
Nothing was collected or created yet.
OpenID
View on Wikipedia

OpenID is an open standard and decentralized authentication protocol promoted by the non-profit OpenID Foundation. It allows users to be authenticated by co-operating sites (known as relying parties, or RP) using a third-party identity provider (IDP) service, eliminating the need for webmasters to provide their own ad hoc login systems, and allowing users to log in to multiple unrelated websites without having to have a separate identity and password for each.[1] Users create accounts by selecting an OpenID identity provider,[1] and then use those accounts to sign on to any website that accepts OpenID authentication. Several large organizations either issue or accept OpenIDs on their websites.[2]
The OpenID standard provides a framework for the communication that must take place between the identity provider and the OpenID acceptor (the "relying party").[3] An extension to the standard (the OpenID Attribute Exchange) facilitates the transfer of user attributes, such as name and gender, from the OpenID identity provider to the relying party (each relying party may request a different set of attributes, depending on its requirements).[4] The OpenID protocol does not rely on a central authority to authenticate a user's identity. Moreover, neither services nor the OpenID standard may mandate a specific means by which to authenticate users, allowing for approaches ranging from the common (such as passwords) to the novel (such as smart cards or biometrics).
The final version of OpenID is OpenID 2.0, finalized and published in December 2007.[5] The term OpenID may also refer to an identifier as specified in the OpenID standard; these identifiers take the form of a unique Uniform Resource Identifier (URI), and are managed by some "OpenID provider" that handles authentication.[1]
Adoption
[edit]As of March 2016[update], there are over 1 billion OpenID-enabled accounts on the Internet (see below) and approximately 1,100,934 sites have integrated OpenID consumer support:[6] AOL, Flickr, Google, Amazon.com, Canonical (provider name Ubuntu One), LiveJournal, Microsoft (provider name Microsoft account), Mixi, Myspace, Novell, OpenStreetMap, Orange, Sears, Sun, Telecom Italia, Universal Music Group, VeriSign, WordPress, Yahoo!, the BBC,[7] IBM,[8] PayPal,[9] and Steam,[10] although some of those organizations also have their own authentication management.
Many if not all of the larger organizations require users to provide authentication in the form of an existing email account or mobile phone number in order to sign up for an account (which then can be used as an OpenID identity). There are several smaller entities that accept sign-ups with no extra identity details required.
Facebook did use OpenID in the past, but moved to Facebook Connect.[11] Blogger also used OpenID, but since May 2018 no longer supports it.[12]
Technical overview
[edit]OpenID is a decentralized authentication protocol that allows users to authenticate with multiple websites using a single set of credentials, eliminating the need for separate usernames and passwords for each website. OpenID authenticates a user with an identity provider (IDP), who then provides the user with a unique identifier (called an OpenID). This identifier can then be used to authenticate the user with any website that supports OpenID.
When a user visits a website that supports OpenID authentication, the website will redirect the user to their chosen IDP. The IDP will then prompt the user to authenticate themselves (e.g., by entering a username and password). Once the user is authenticated, the IDP will generate an OpenID and send it back to the website. The website can then use this OpenID to authenticate the user without needing to know their actual credentials.
OpenID is built on top of several existing standards, including HTTP, HTML, and XML. OpenID relies on a number of technologies, including a discovery mechanism that allows websites to find the IDP associated with a particular OpenID, as well as security mechanisms to protect against phishing and other attacks.[13]
One of the key benefits of OpenID is that it allows users to control their own identity information, rather than relying on individual websites to store and manage their login credentials. This can be particularly important in cases where websites are vulnerable to security breaches or where users are concerned about the privacy of their personal information.
OpenID has been widely adopted by a number of large websites and service providers, including Google, Yahoo!, and PayPal. The protocol is also used by a number of open source projects and frameworks, including Ruby on Rails and Django.
Logging in
[edit]The end user interacts with a relying party (such as a website) that provides an option to specify an OpenID for the purposes of authentication; an end user typically has previously registered an OpenID (e.g. alice.openid.example.org) with an OpenID provider (e.g. openid.example.org).[1]
The relying party typically transforms the OpenID into a canonical URL form (e.g. http://alice.openid.example.org/).
- With OpenID 1.0, the relying party then requests the HTML resource identified by the URL and reads an HTML link tag to discover the OpenID provider's URL (e.g.
http://openid.example.org/openid-auth.php). The relying party also discovers whether to use a delegated identity (see below). - With OpenID 2.0, the relying party discovers the OpenID provider URL by requesting the XRDS document (also called the Yadis document) with the content type
application/xrds+xml; this document may be available at the target URL and is always available for a target XRI.
There are two modes in which the relying party may communicate with the OpenID provider:
checkid_immediate, in which the relying party requests that the OpenID provider not interact with the end user. All communication is relayed through the end user's user-agent without explicitly notifying the end user.checkid_setup, in which the end user communicates with the OpenID provider via the same user-agent used to access the relying party.
The checkid_immediate mode can fall back to the checkid_setup mode if the operation cannot be automated.
First, the relying party and the OpenID provider (optionally) establish a shared secret, referenced by an associate handle, which the relying party then stores. If using the checkid_setup mode, the relying party redirects the end user's user-agent to the OpenID provider so the end user can authenticate directly with the OpenID provider.
The method of authentication may vary, but typically, an OpenID provider prompts the end user for a password or some cryptographic token, and then asks whether the end user trusts the relying party to receive the necessary identity details.
If the end user declines the OpenID provider's request to trust the relying party, then the user-agent is redirected back to the relying party with a message indicating that authentication was rejected; the relying party in turn refuses to authenticate the end user.
If the end user accepts the OpenID provider's request to trust the relying party, then the user-agent is redirected back to the relying party along with the end user's credentials. That relying party must then confirm that the credentials really came from the OpenID provider. If the relying party and OpenID provider had previously established a shared secret, then the relying party can validate the identity of the OpenID provider by comparing its copy of the shared secret against the one received along with the end user's credentials; such a relying party is called stateful because it stores the shared secret between sessions. In contrast, a stateless or dumb relying party must make one more background request (check_authentication) to ensure that the data indeed came from the OpenID provider.
After the OpenID has been verified, authentication is considered successful and the end user is considered logged into the relying party under the identity specified by the given OpenID (e.g. alice.openid.example.org). The relying party typically then stores the end user's OpenID along with the end user's other session information.
Identifiers
[edit]To obtain an OpenID-enabled URL that can be used to log into OpenID-enabled websites, a user registers an OpenID identifier with an identity provider. Identity providers offer the ability to register a URL (typically a third-level domain, e.g. username.example.com) that will automatically be configured with OpenID authentication service.
Once they have registered an OpenID, a user can also use an existing URL under their own control (such as a blog or home page) as an alias or "delegated identity". They simply insert the appropriate OpenID tags in the HTML[14] or serve a Yadis document.[15]
Starting with OpenID Authentication 2.0 (and some 1.1 implementations), there are two types of identifiers that can be used with OpenID: URLs and XRIs.
XRIs are a new form of Internet identifier designed specifically for cross-domain digital identity. For example, XRIs come in two forms—i-names and i-numbers—that are usually registered simultaneously as synonyms. I-names are reassignable (like domain names), while i-numbers are never reassigned. When an XRI i-name is used as an OpenID identifier, it is immediately resolved to the synonymous i-number (the CanonicalID element of the XRDS document). This i-number is the OpenID identifier stored by the relying party. In this way, both the user and the relying party are protected from the end user's OpenID identity ever being taken over by another party as can happen with a URL based on a reassignable DNS name.
OpenID Foundation
[edit]The OpenID Foundation (OIDF) promotes and enhances the OpenID community and technologies. The OIDF is a non-profit international standards development organization of individual developers, government agencies and companies who wish to promote and protect OpenID. The OpenID Foundation was formed in June 2007 and serves as a public trust organization representing an open community of developers, vendors and users. OIDF assists the community by providing needed infrastructure and help in promoting and supporting adoption of OpenID. This includes managing intellectual property and trade marks as well a fostering viral growth and global participation in OpenID.
People
[edit]The OpenID Foundation's board of directors has six community board members and eight corporate board members:[16]
|
Community board members
|
Corporate board members
|
Chapters
[edit]OIDF is a global organization to promote digital identity and to encourage the further adoption of OpenID, the OIDF has encouraged the creation of member chapters. Member chapters are officially part of the Foundation and work within their own constituency to support the development and adoption of OpenID as a framework for user-centric identity on the internet.
Intellectual property and contribution agreements
[edit]The OIDF ensures that OpenID specifications are freely implementable therefore the OIDF requires all contributors to sign a contribution agreement. This agreement both grants a copyright license to the Foundation to publish the collective specifications and includes a patent non-assertion agreement. The non-assertion agreement states that the contributor will not sue someone for implementing OpenID specifications.
Legal issues
[edit]The OpenID trademark in the United States was assigned to the OpenID Foundation in March 2008.[17] It had been registered by NetMesh Inc. before the OpenID Foundation was operational.[18][19] In Europe, as of August 31, 2007, the OpenID trademark is registered to the OpenID Europe Foundation.[20]
The OpenID logo was designed by Randy "ydnar" Reddig, who in 2005 had expressed plans to transfer the rights to an OpenID organization.[21]
Since the original announcement of OpenID, the official site has stated:[22]
Nobody should own this. Nobody's planning on making any money from this. The goal is to release every part of this under the most liberal licenses possible, so there's no money or licensing or registering required to play. It benefits the community as a whole if something like this exists, and we're all a part of the community.
Sun Microsystems, VeriSign and a number of smaller companies involved in OpenID have issued patent non-assertion covenants covering OpenID 1.1 specifications. The covenants state that the companies will not assert any of their patents against OpenID implementations and will revoke their promises from anyone who threatens, or asserts, patents against OpenID implementors.[23][24]
Security
[edit]Authentication bugs
[edit]In March, 2012, a research paper[25] reported two generic security issues in OpenID. Both issues allow an attacker to sign in to a victim's relying party accounts. For the first issue, OpenID and Google (an Identity Provider of OpenID) both published security advisories to address it.[26][27] Google's advisory says "An attacker could forge an OpenID request that doesn't ask for the user's email address, and then insert an unsigned email address into the IDPs response. If the attacker relays this response to a website that doesn't notice that this attribute is unsigned, the website may be tricked into logging the attacker in to any local account." The research paper claims that many popular websites have been confirmed vulnerable, including Yahoo! Mail, smartsheet.com, Zoho, manymoon.com, diigo.com. The researchers have notified the affected parties, who have then fixed their vulnerable code.
For the second issue, the paper called it "Data Type Confusion Logic Flaw", which also allows attackers to sign in to victims' RP accounts. Google and PayPal were initially confirmed vulnerable. OpenID published a vulnerability report[28] on the flaw. The report says Google and PayPal have applied fixes, and suggest other OpenID vendors to check their implementations.
Phishing
[edit]Some observers have suggested that OpenID has security weaknesses and may prove vulnerable to phishing attacks.[29][30][31] For example, a malicious relaying party may forward the end user to a bogus identity provider authentication page asking that end user to input their credentials. On completion of this, the malicious party (who in this case also controls the bogus authentication page) could then have access to the end user's account with the identity provider, and then use that end user's OpenID to log into other services.
In an attempt to combat possible phishing attacks, some OpenID providers mandate that the end user needs to be authenticated with them prior to an attempt to authenticate with the relying party.[32] This relies on the end user knowing the policy of the identity provider. In December 2008, the OpenID Foundation approved version 1.0 of the Provider Authentication Policy Extension (PAPE), which "enables Relying Parties to request that OpenID Providers employ specified authentication policies when authenticating users and for OpenID Providers to inform the Relying Parties which policies were actually used."[33]
Privacy and trust issues
[edit]Other security issues identified with OpenID involve lack of privacy and failure to address the trust problem.[34] However, this problem is not unique to OpenID and is simply the state of the Internet as commonly used.[citation needed]
The Identity Provider does, however, get a log of your OpenID logins; they know when you logged into what website, making cross-site tracking much easier. A compromised OpenID account is also likely to be a more serious breach of privacy than a compromised account on a single site.
Authentication hijacking in unsecured connection
[edit]Another important vulnerability is present in the last step in the authentication scheme when TLS/SSL are not used: the redirect-URL from the identity provider to the relying party. The problem with this redirect is the fact that anyone who can obtain this URL (e.g. by sniffing the wire) can replay it and get logged into the site as the victim user. Some of the identity providers use nonces (a number used just once) to allow a user to log into the site once and fail all the consecutive attempts. The nonce solution works if the user is the first one to use the URL. However, a fast attacker who is sniffing the wire can obtain the URL and immediately reset a user's TCP connection (as an attacker is sniffing the wire and knows the required TCP sequence numbers) and then execute the replay attack as described above. Thus nonces only protect against passive attackers, but cannot prevent active attackers from executing the replay attack.[35] Use of TLS/SSL in the authentication process can significantly reduce this risk.
This can be restated as:
IF (Both RP1 and RP2 have Bob as a client) AND // a common case
(Bob uses the same IDP with both RP1 and RP2) AND // a common case
(RP1 does not use VPN/SSL/TLS to secure their connection with the client) // preventable!
THEN
RP2 could obtain credentials sufficient to impersonate Bob with RP1
END-IF
Covert Redirect
[edit]On May 1, 2014, a bug dubbed "Covert Redirect related to OAuth 2.0 and OpenID" was disclosed.[36][37] It was discovered by mathematics doctoral student Wang Jing at the School of Physical and Mathematical Sciences, Nanyang Technological University, Singapore.[38][39][40]
The announcement of OpenID is: "'Covert Redirect', publicized in May 2014, is an instance of attackers using open redirectors – a well-known threat, with well-known means of prevention. The OpenID Connect protocol mandates strict measures that preclude open redirectors to prevent this vulnerability."[41]
"The general consensus, so far, is that Covert Redirect is not as bad, but still a threat. Understanding what makes it dangerous requires a basic understanding of Open Redirect, and how it can be exploited."[42]
A patch was not immediately made available. Ori Eisen, founder, chairman and chief innovation officer at 41st Parameter told Sue Marquette Poremba, "In any distributed system, we are counting of the good nature of the participants to do the right thing. In cases like OAuth and OpenID, the distribution is so vast that it is unreasonable to expect each and every website to patch up in the near future".[43]
History
[edit]The original OpenID authentication protocol was developed in May 2005[44] by Brad Fitzpatrick, creator of popular community website LiveJournal, while working at Six Apart.[45] Initially referred to as Yadis (an acronym for "Yet another distributed identity system"),[46] it was named OpenID after the openid.net domain name was given to Six Apart to use for the project.[47] OpenID support was soon implemented on LiveJournal and fellow LiveJournal engine community DeadJournal for blog post comments and quickly gained attention in the digital identity community.[48][49] Web developer JanRain was an early supporter of OpenID, providing OpenID software libraries and expanding its business around OpenID-based services.
In late June, discussions started between OpenID users and developers from enterprise software company NetMesh, leading to collaboration on interoperability between OpenID and NetMesh's similar Light-weight Identity (LID) protocol. The direct result of the collaboration was the Yadis discovery protocol, adopting the name originally used for OpenID. The new Yadis was announced on October 24, 2005.[50] After a discussion at the 2005 Internet Identity Workshop a few days later, XRI/i-names developers joined the Yadis project,[51] contributing their Extensible Resource Descriptor Sequence (XRDS) format for utilization in the protocol.[52]
In December, developers at Sxip Identity began discussions with the OpenID/Yadis community[53] after announcing a shift in the development of version 2.0 of its Simple Extensible Identity Protocol (SXIP) to URL-based identities like LID and OpenID.[54] In March 2006, JanRain developed a Simple Registration (SREG) extension for OpenID enabling primitive profile-exchange[55] and in April submitted a proposal to formalize extensions to OpenID. The same month, work had also begun on incorporating full XRI support into OpenID.[56] Around early May, key OpenID developer David Recordon left Six Apart, joining VeriSign to focus more on digital identity and guidance for the OpenID spec.[49][57] By early June, the major differences between the SXIP 2.0 and OpenID projects were resolved with the agreement to support multiple personas in OpenID by submission of an identity provider URL rather than a full identity URL. With this, as well as the addition of extensions and XRI support underway, OpenID was evolving into a full-fledged digital identity framework, with Recordon proclaiming "We see OpenID as being an umbrella for the framework that encompasses the layers for identifiers, discovery, authentication and a messaging services layer that sits atop and this entire thing has sort of been dubbed 'OpenID 2.0'.[58] " In late July, Sxip began to merge its Digital Identity Exchange (DIX) protocol into OpenID, submitting initial drafts of the OpenID Attribute Exchange (AX) extension in August. Late in 2006, a ZDNet opinion piece made the case for OpenID to users, web site operators and entrepreneurs.[59]
On January 31, 2007, Symantec announced support for OpenID in its Identity Initiative products and services.[60] A week later, on February 6 Microsoft made a joint announcement with JanRain, Sxip, and VeriSign to collaborate on interoperability between OpenID and Microsoft's Windows CardSpace digital identity platform, with particular focus on developing a phishing-resistant authentication solution for OpenID. As part of the collaboration, Microsoft pledged to support OpenID in its future identity server products and JanRain, Sxip, and VeriSign pledged to add support for Microsoft's Information Card profile to their future identity solutions.[61] In mid-February, AOL announced that an experimental OpenID provider service was functional for all AOL and AOL Instant Messenger (AIM) accounts.[62]
In May, Sun Microsystems began working with the OpenID community, announcing an OpenID program,[63] as well as entering a non-assertion covenant with the OpenID community, pledging not to assert any of its patents against implementations of OpenID.[23] In June, OpenID leadership formed the OpenID Foundation, an Oregon-based public benefit corporation for managing the OpenID brand and property.[64] The same month, an independent OpenID Europe Foundation was formed in Belgium[65] by Snorri Giorgetti. By early December, non-assertion agreements were collected by the major contributors to the protocol and the final OpenID Authentication 2.0 and OpenID Attribute Exchange 1.0 specifications were ratified on December 5.[66]
In mid-January 2008, Yahoo! announced initial OpenID 2.0 support, both as a provider and as a relying party, releasing the provider service by the end of the month.[67] In early February, Google, IBM, Microsoft, VeriSign and Yahoo! joined the OpenID Foundation as corporate board members.[68] Around early May, SourceForge, Inc. introduced OpenID provider and relying party support to leading open source software development website SourceForge.net.[69] In late July, popular social network service MySpace announced support for OpenID as a provider.[70] In late October, Google launched support as an OpenID provider and Microsoft announced that Windows Live ID would support OpenID.[71] In November, JanRain announced a free hosted service, RPX Basic, that allows websites to begin accepting OpenIDs for registration and login without having to install, integrate and configure the OpenID open source libraries.[72]
In January 2009, PayPal joined the OpenID Foundation as a corporate member, followed shortly by Facebook in February. The OpenID Foundation formed an executive committee and appointed Don Thibeau as executive director. In March, MySpace launched their previously announced OpenID provider service, enabling all MySpace users to use their MySpace URL as an OpenID. In May, Facebook launched their relying party functionality,[73][74] letting users use an automatic login-enabled OpenID account (e.g. Google) to log into Facebook.[75]
In September 2013, Janrain announced that MyOpenID.com would be shut down on February 1, 2014; a pie chart showed Facebook and Google dominate the social login space as of Q2 2013.[76] Facebook has since left OpenID; it is no longer a sponsor, represented on the board, or permitting OpenID logins.[16][77]
In May 2016, Symantec announced that they would be discontinuing their pip.verisignlabs.com OpenID personal identity portal service.[78][79]
In March 2018, Stack Overflow announced an end to OpenID support, citing insufficient usage to justify the cost. In the announcement, it was stated that based on activity, users strongly preferred Facebook, Google, and e-mail/password based account authentication.[80]
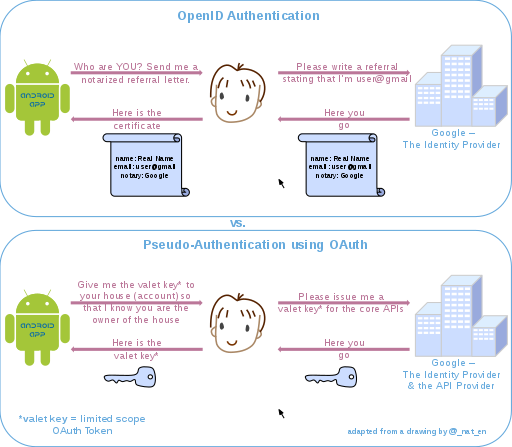
OpenID versus pseudo-authentication using OAuth
[edit]OpenID is a way to use a single set of user credentials to access multiple sites, while OAuth facilitates the authorization of one site to access and use information related to the user's account on another site. Although OAuth is not an authentication protocol, it can be used as part of one.
Authentication in the context of a user accessing an application tells an application who the current user is and whether or not they're present. [...] Authentication is all about the user and their presence with the application, and an internet-scale authentication protocol needs to be able to do this across network and security boundaries.
However, OAuth tells the application none of that. OAuth says absolutely nothing about the user, nor does it say how the user proved their presence or even if they're still there. As far as an OAuth client is concerned, it asked for a token, got a token, and eventually used that token to access some API. It doesn't know anything about who authorized the application or if there was even a user there at all. In fact, much of the point of OAuth is about giving this delegated access for use in situations where the user is not present on the connection between the client and the resource being accessed. This is great for client authorization, but it's really bad for authentication where the whole point is figuring out if the user is there or not (and who they are).[81]
The following drawing highlights the differences between using OpenID versus OAuth for authentication. Note that with OpenID, the process starts with the application asking the user for their identity (typically an OpenID URI), whereas in the case of OAuth, the application directly requests a limited access OAuth Token (valet key) to access the APIs (enter the house) on user's behalf. If the user can grant that access, the application can retrieve the unique identifier for establishing the profile (identity) using the APIs.
Attack against pseudo-authentication
[edit]OpenID provides a cryptographic verification mechanism that prevents the attack below against users who misuse OAuth for authentication.
Note that the valet key does not describe the user in any way, it only provides limited access rights, to some house (which is not even necessarily the user's, they just had a key). Therefore if the key becomes compromised (the user is malicious and managed to steal the key to someone else's house), then the user can impersonate the house owner to the application who requested their authenticity. If the key is compromised by any point in the chain of trust, a malicious user may intercept it and use it to impersonate user X for any application relying on OAuth2 for pseudo authentication against the same OAuth authorization server. Conversely, the notarized letter contains the user's signature, which can be checked by the requesting application against the user, so this attack is not viable. [82]
Verifying the letter
[edit]The letter can use public-key cryptography to be authenticated.
- The requesting application provides its encryption public key to the user, which provides it to the authentication server.
- The authentication server encrypts a document containing an encryption key which corresponds to a one-way hash of a secret the user knows (e.g. passphrase) for challenge–response using the application's public key.
- The user passes the encrypted document back to the application, which decrypts it.
- The application encrypts a random phrase using the received encryption key, and asks that the user do the same, then compares the results, if they match, the user is authentic.
OpenID Connect (OIDC)
[edit]Published in February 2014[83] by the OpenID Foundation, OpenID Connect (OIDC) is the third generation of OpenID technology. It is an authentication layer on top of the OAuth 2.0 authorization framework.[84] It allows computing clients to verify the identity of an end user based on the authentication performed by an authorization server, as well as to obtain the basic profile information about the end user in an interoperable and REST-like manner. In technical terms, OpenID Connect specifies a RESTful HTTP API, using JSON as a data format.
OpenID Connect allows a range of parties, including web-based, mobile and JavaScript clients, to request and receive information about authenticated sessions and end users. The OpenID Connect specification is extensible, supporting optional features such as encryption of identity data, discovery of OpenID providers, and session management.
See also
[edit]References
[edit]- ^ a b c d Eldon, Eric (14 April 2009). "Single sign-on service OpenID getting more usage". venturebeat.com. Archived from the original on 2 April 2018. Retrieved 25 April 2009.
- ^ "What is an OpenID?". 8 October 2007. Archived from the original on 14 June 2014. Retrieved 19 June 2014.
- ^ "OpenID Authentication 2.0 specification – Final". Archived from the original on 22 October 2011. Retrieved 24 October 2011.
- ^ "OpenID Attribute Exchange 1.0 – Final". Archived from the original on 20 November 2017. Retrieved 24 October 2011.
- ^ "OpenID Authentication 2.0 - Final". 5 December 2007. Archived from the original on 22 October 2011. Retrieved 18 May 2014.
- ^ "OpenID Usage Statistics". Archived from the original on 4 April 2016. Retrieved 1 April 2016.
- ^ bashburn, bill (22 April 2008). "BBC Joins OpenID Foundation". OpenID - The Internet Identity Layer. Archived from the original on 16 October 2008. Retrieved 29 October 2008.
- ^ "Technology Leaders Join OpenID Foundation to Promote Open Identity Management on the Web". 7 February 2008. Archived from the original on 10 February 2008.
- ^ "PayPal Access Uses OpenID 2.0". OpenID - The Internet Identity Layer. OpenID ·. 19 October 2011. Archived from the original on 22 June 2014. Retrieved 19 June 2014.
- ^ "Steam Community :: Steam Web API Documentation". Archived from the original on 10 February 2012. Retrieved 10 February 2012.
- ^ Perez, Juan Carlos (4 December 2008). "Facebook, Google launch data portability programs to all". Network World, Inc. Archived from the original on 22 June 2014. Retrieved 19 June 2014.
- ^ "It's spring cleaning time for Blogger". Blogger team. Archived from the original on 2 August 2018. Retrieved 10 September 2019.
- ^ Deeptha, R.; Mukesh, Rajeswari (1 September 2018). "Extending OpenID Connect Towards Mission Critical Applications". Cybernetics and Information Technologies. 18 (3): 93–110. doi:10.2478/cait-2018-0041.
- ^ "OpenID Authentication 1.1#Delegation". Archived from the original on 18 November 2017. Retrieved 30 June 2009.
- ^ Paul Tarjan. "Easy OpenID Delegation with Yadis". Archived from the original on 4 July 2009. Retrieved 30 June 2009.
- ^ a b "Leadership". openID Foundation. Archived from the original on 24 June 2014. Retrieved 19 June 2014.
- ^ "Trademark Assignment, Serial #: 78899244". United States Patent and Trademark Office. 6 May 2008. Archived from the original on 10 October 2013. Retrieved 19 May 2008.
Exec Dt: 03/27/2008
- ^ "Latest Status Info". United States Patent and Trademark Office. 27 March 2006. Archived from the original on 14 May 2011. Retrieved 20 March 2008.
- ^ "NetMesh: Company / Management". NetMesh. Archived from the original on 30 August 2007. Retrieved 20 March 2008.
- ^ "OpenID Europe Trademark & Logo Policy". OpenID Europe Foundation. Archived from the original on 9 March 2008. Retrieved 20 March 2008.
- ^ Reddig, Randy (29 June 2005). "OpenID Logo". Danga Interactive. Archived from the original on 14 February 2008. Retrieved 20 March 2008.
- ^ Fitzpatrick, Brad (10 August 2009). "Intellectual Property". Archived from the original on 11 October 2009. Retrieved 13 October 2009.
- ^ a b "Sun OpenID: Non-Assertion Covenant". Sun Microsystems. Retrieved 20 March 2008.
- ^ "VeriSign's OpenID Non-Assertion Patent Covenant". VeriSign. Archived from the original on 15 April 2008. Retrieved 20 March 2008.
- ^ Rui Wang; Shuo Chen; XiaoFeng Wang (May 2012). "Signing Me onto Your Accounts through Facebook and Google: a Traffic-Guided Security Study of Commercially Deployed Single-Sign-On Web Services". Archived from the original on 13 April 2016. Retrieved 9 March 2012.
- ^ "Attribute Exchange Security Alert". 5 May 2011. Archived from the original on 31 July 2017. Retrieved 9 March 2012.
- ^ "Security advisory to websites using OpenID Attribute Exchange". 5 May 2011. Archived from the original on 24 December 2011. Retrieved 9 March 2012.
- ^ "Vulnerability report: Data confusion". OpenID - The Internet Identity Layer. 15 March 2012. Archived from the original on 5 September 2019. Retrieved 15 March 2012.
- ^ Crowley, Paul (1 June 2005). "Phishing attacks on OpenID". Danga Interactive. Archived from the original on 10 October 2008. Retrieved 20 March 2008.
- ^ Anderson, Tim (5 March 2007). "OpenID still open to abuse". IT Week. Archived from the original on 4 July 2008. Retrieved 13 March 2007.
- ^ Slot, Marco. "Beginner's guide to OpenID phishing". Archived from the original on 4 August 2007. Retrieved 31 July 2007.
- ^ "Verisign PIP FAQ". Archived from the original on 13 November 2008. Retrieved 13 November 2008.
- ^ Jones, Mike (31 December 2008). "PAPE Approved as an OpenID Specification". OpenID Foundation. Archived from the original on 1 January 2009. Retrieved 2 January 2009.
- ^ Stefan Brands (22 August 2007). "The problem(s) with OpenID". Archived from the original on 16 May 2011. Retrieved 12 December 2010. (originally published on The Identity Corner at www.idcorner.org/?p=161)
- ^ Tsyrklevich, Eugene. "Single Sign-On for the Internet: A Security Story" (PDF). Blackhat USA. Archived (PDF) from the original on 12 January 2012. Retrieved 19 April 2012.
- ^ "Serious security flaw in OAuth, OpenID discovered". CNET. 2 May 2014. Archived from the original on 2 November 2015. Retrieved 10 November 2014.
- ^ "Covert Redirect". Tetraph. 1 May 2014. Archived from the original on 10 March 2016. Retrieved 10 November 2014.
- ^ "Facebook, Google Users Threatened by New Security Flaw". Yahoo. 2 May 2014. Archived from the original on 25 July 2019. Retrieved 10 November 2014.
- ^ "Nasty Covert Redirect Vulnerability found in OAuth and OpenID". The Hacker News. 3 May 2014. Archived from the original on 8 November 2014. Retrieved 10 November 2014.
- ^ "Math student detects OAuth, OpenID security vulnerability". Tech Xplore. 3 May 2014. Archived from the original on 4 December 2014. Retrieved 10 November 2014.
- ^ "Covert Redirect". OpenID - The Internet Identity Layer. OpenID. 15 May 2014. Archived from the original on 20 October 2014. Retrieved 10 November 2014.
- ^ "'Covert Redirect' vulnerability impacts OAuth 2.0, OpenID". SC Magazine. 2 May 2014. Retrieved 10 November 2014.
- ^ "Lessons to be Learned from Covert Redirect". 41st Parameter. 5 May 2014. Retrieved 10 November 2014.
- ^ Fitzpatrick, Brad (16 May 2005). "Distributed Identity: Yadis". LiveJournal. Archived from the original on 4 May 2006. Retrieved 20 March 2008.
- ^ Waters, John K (1 December 2007). "OpenID Updates Identity Spec". Redmond Developer News. Archived from the original on 8 February 2008. Retrieved 20 March 2008.
- ^ "Glossary". LiveJournal Server: Technical Info. Archived from the original on 30 September 2009. Retrieved 13 October 2009.
- ^ Lehn, David I. (18 May 2005). "18 May 2005". Advogato blog for dlehn. Advogato. Archived from the original on 21 December 2010. Retrieved 13 October 2009.
They were looking for a name and managed to email me about openid.net right before I was going to offer it to them. So I gave it to them for the new and improved OpenID project.
- ^ "OpenID: an actually distributed identity system". 24 September 2005. Archived from the original on 24 September 2005. Retrieved 20 March 2008.
- ^ a b Fitzpatrick, Brad (30 May 2006). "brad's life – OpenID and SixApart". LiveJournal. Archived from the original on 25 April 2007. Retrieved 20 March 2008.
- ^ Recordon, David (24 December 2005). "Announcing YADIS...again". Danga Interactive. Archived from the original on 5 September 2008. Retrieved 20 March 2008.
- ^ Reed, Dummond (31 December 2005). "Implementing YADIS with no new software". Danga Interactive. Archived from the original on 5 September 2008. Retrieved 20 March 2008.
- ^ Reed, Drummond (30 November 2008). "XRD Begins". Equals Drummond. Archived from the original on 20 December 2008. Retrieved 5 January 2009.
- ^ Hardt, Dick (18 December 2005). "Sxip concerns with YADIS". Danga Interactive. Archived from the original on 15 October 2008. Retrieved 20 March 2008.
- ^ Hardt, Dick (10 December 2005). "SXIP 2.0 Teaser". Identity 2.0. Archived from the original on 14 August 2007. Retrieved 20 March 2008.
- ^ Hoyt, Josh (15 March 2006). "OpenID + Simple Registration Information Exchange". Danga Interactive. Archived from the original on 11 October 2008. Retrieved 20 March 2008.
- ^ Grey, Victor (2 April 2006). "Proposal for an XRI (i-name) profile for OpenID". Danga Interactive. Archived from the original on 19 March 2008. Retrieved 20 March 2008.
- ^ Recordon, David (29 April 2006). "Movin' On..." LiveJournal. Archived from the original on 20 October 2006. Retrieved 20 March 2008.
- ^ Recordon, David (16 June 2006). "Moving OpenID Forward". Danga Interactive. Archived from the original on 22 May 2008. Retrieved 19 May 2008.
- ^ Becker, Phil (4 December 2006). "The case for OpenID". ZDNet. Archived from the original on 4 May 2025. Retrieved 12 December 2010.
- ^ "Symantec Unveils Security 2.0 Identity Initiative at DEMO 07 Conference". Symantec. 31 January 2007. Archived from the original on 9 February 2007. Retrieved 20 March 2008.
- ^ Graves, Michael (6 February 2007). "VeriSign, Microsoft & Partners to Work together on OpenID + Cardspace". VeriSign. Archived from the original on 3 May 2008. Retrieved 20 March 2008.
- ^ Panzer, John (16 February 2007). "AOL and 63 Million OpenIDs". AOL Developer Network. Archived from the original on 11 May 2008. Retrieved 20 March 2008.
- ^ "Sun Microsystems Announces OpenID Program". PR Newswire. 7 May 2007. Archived from the original on 9 May 2008. Retrieved 20 March 2008.
- ^ OpenID Board of Directors (1 June 2007). "OpenID Foundation". Archived from the original on 23 November 2017. Retrieved 20 March 2008.
- ^ "OpenID Europe Foundation". Archived from the original on 15 April 2008. Retrieved 4 April 2008.
- ^ "OpenID 2.0...Final(ly)!". OpenID Foundation. 5 December 2007. Archived from the original on 30 April 2008. Retrieved 20 March 2008.
- ^ "Yahoo! Announces Support for OpenID; Users Able to Access Multiple Internet Sites with Their Yahoo! ID". Yahoo!. 17 January 2008. Archived from the original on 4 March 2008. Retrieved 20 March 2008.
- ^ "Technology Leaders Join OpenID Foundation to Promote Open Identity Management on the Web". OpenID Foundation. Marketwire. 7 February 2008. Archived from the original on 15 February 2008. Retrieved 20 March 2008.
- ^ "SourceForge Implements OpenID Technology" (Press release). SourceForge, Inc. 7 May 2008. Archived from the original on 13 May 2008. Retrieved 21 May 2008.
- ^ "MySpace Announces Support for "OpenID" and Introduces New Data Availability Implementations". Business Wire. MySpace. 22 July 2008. p. 2. Archived from the original on 14 May 2011. Retrieved 23 July 2008.
- ^ "Microsoft and Google announce OpenID support". OpenID - The Internet Identity Layer. OpenID Foundation. 30 October 2008. Archived from the original on 18 December 2008. Retrieved 2 January 2009.
- ^ "JanRain Releases Free Version of Industry Leading OpenID Solution" (Press release). JanRain, Inc. 14 November 2008. Archived from the original on 18 December 2008. Retrieved 14 November 2008.
- ^ "Facebook Developers | Facebook Developers News". Developers.facebook.com. 18 May 2009. Archived from the original on 23 December 2009. Retrieved 28 July 2009.
- ^ "Facebook now accepts Google account logins". Pocket-lint.com. 19 May 2009. Archived from the original on 22 May 2009. Retrieved 28 July 2009.
- ^ "OpenID Requirements – Facebook Developer Wiki". Wiki.developers.facebook.com. 26 June 2009. Archived from the original on 23 December 2009. Retrieved 28 July 2009.
- ^ Kane, Zee M (4 September 2013). "MyOpenID to shut down. Will be turned off on February 1, 2014". The Next Web. Archived from the original on 7 September 2013. Retrieved 5 September 2013.
- ^ "OpenID Sponsoring Members". 7 October 2009. Retrieved 17 April 2014.
- ^ "Symantec Personal Identification Portal banner indicates service will be discontinued on 12 September 2016". Archived from the original on 11 June 2016. Retrieved 17 May 2016.
- ^ "Is Symantec failing hard at being Google?". 7 May 2016. Archived from the original on 2 June 2016. Retrieved 17 May 2016.
- ^ "Support for OpenID ended on July 25, 2018". Archived from the original on 7 March 2018. Retrieved 6 March 2018.
- ^ "User Authentication with OAuth 2.0". OAuth.net. Archived from the original on 19 November 2015. Retrieved 19 March 2015.
- ^ "Why is it a bad idea to use plain oauth2 for authentication?". Information Security Stack Exchange. Archived from the original on 7 July 2018. Retrieved 7 July 2018.
- ^ "Final OpenID Connect Core 1.0 - Appendix C. Notices". 2014. Archived from the original on 14 March 2024. Retrieved 14 March 2024.
- ^ "OpenID Connect FAQ and Q&As". 20 February 2014. Archived from the original on 23 August 2014. Retrieved 25 August 2014.
External links
[edit]OpenID
View on GrokipediaOverview
Definition and Purpose
OpenID is an open standard for decentralized digital identity authentication that enables users to sign in to multiple independent websites using a single, user-controlled identifier, without the need to share passwords or other credentials with relying parties.[2] This protocol allows end users to prove ownership or control of a unique identifier, such as a URL—through interactions with an OpenID provider, fostering a user-centric approach to identity management across the web.[2] The primary purpose of OpenID is to facilitate decentralized single sign-on (SSO), permitting users to authenticate once with their chosen identity provider and then access various services without repeated logins, thereby reducing password fatigue and streamlining the overall user experience.[8] Key benefits include enhanced user control over personal identity data, the absence of a mandatory central authority to manage identities, and broad interoperability between diverse online services and providers, which promotes portability and flexibility in digital interactions.[2][8] OpenID was developed in the early 2000s, with its initial release in 2005, to address the escalating challenge of users managing an ever-increasing number of distinct usernames and passwords for different websites amid the rapid growth of the internet and web-based applications.[9] This motivation stemmed from the recognition that traditional site-specific authentication created significant usability barriers and security risks due to credential reuse and weak password practices.[10] Over time, OpenID has evolved, with OpenID Connect emerging as its successor and current standard to incorporate modern enhancements like integration with OAuth 2.0 for broader applicability in web, mobile, and API contexts; the original OpenID Authentication 2.0 is now considered legacy.[4]Core Components
OpenID's architecture revolves around three primary roles that facilitate decentralized authentication. The OpenID Provider (OP) serves as the identity issuer, operating as a server that authenticates users and issues assertions about their identity, typically accessible via an OP Endpoint URL using HTTP or HTTPS protocols.[2] The Relying Party (RP) functions as the service or web application that relies on the OP for authentication, seeking verifiable proof that the end user controls a specific identifier without managing identities itself.[2] At the center is the End User, the individual who owns and controls the identifier, choosing their preferred OP to manage their digital identity across services.[2] Supporting these roles are key elements that enable interaction in a web-based environment. The User-Agent, commonly the end user's web browser, acts as the intermediary, facilitating communication between the RP, OP, and end user through standard HTTP/1.1-compliant requests and responses.[2] Discovery mechanisms provide a high-level means for RPs to locate an end user's OP without prior configuration.[2] The protocol is layered on established web standards to ensure interoperability and extensibility. It builds upon HTTP and URI conventions for all communications, using standardized formats for requests and responses, with support for extensions.[2] Unlike centralized identity systems, OpenID adopts a decentralized model that empowers end users to select any compatible OP, eliminating the need for a single authority and allowing identifiers to remain portable across providers.[2] This user-centric approach originated from early specifications aimed at enabling portable digital identity without vendor lock-in.[2] For details on modern implementations, see the OpenID Connect section.Technical Specifications
Discovery and Identifiers
In OpenID Authentication 2.0, identifiers serve as the starting point for the authentication process, allowing end users to claim control over a unique resource without sharing credentials directly. These identifiers primarily consist of HTTP or HTTPS URLs, such ashttp://example.com/, which represent user-controlled web resources, or XRIs (Extensible Resource Identifiers), which provide a structured syntax for persistent global identifiers like i-names or i-numbers. XRIs, defined by the XRI Technical Committee at OASIS, enable abstraction over various identity schemes but require resolution to a canonical form for use in OpenID. Additionally, identifiers are categorized as claimed identifiers, which are user-owned and verified through the protocol (e.g., a personal URL like http://myblog.com/), or OP-local identifiers, which are specific to an OpenID Provider (OP) and may not be directly controlled by the user (e.g., https://user123.op.example.com/).[2]
The discovery process in OpenID 2.0 enables a relying party (RP) to locate the OP endpoint and related services associated with a provided identifier, using a series of HTTP fetches and document parsing. For URL identifiers, the process begins with normalization: the input is stripped of fragments (e.g., #section is removed), prefixed with http:// if no scheme is present, and treated as an absolute URI per RFC 3986 rules; relative references or those starting with www. are resolved accordingly to avoid duplicates. The RP then performs HTML-based discovery by fetching the normalized URL and scanning the HTML <head> for <link> elements, such as <link rel="openid2.provider" href="https://op.example.com/openid" rel="nofollow"> to identify the OP endpoint or <link rel="openid2.local_id" href="https://user.op.example.com" rel="nofollow"> for an OP-local alias. If Yadis discovery (via HTTP headers like X-Yadis-Location) succeeds, an XRDS document is retrieved, containing <XRD> elements with <Service> tags that specify types like http://specs.openid.net/auth/2.0/server for the OP endpoint URI. For XRI identifiers, discovery routes through XRI resolution services to obtain an XRDS document, including a <CanonicalID> element for persistence. This entire process relies on HTTP redirection (e.g., 302 or 303 status codes) to follow chains and resolve the final endpoint, ensuring the RP obtains verifiable service details without prior knowledge of the OP.[2]
Claimed identifiers differ from delegated setups in that the former directly assert user ownership, with the RP verifying control by completing the full authentication flow against the claimed URL's discovered OP. In delegation, users maintain a personal claimed identifier (e.g., their website URL) while offloading authentication to a trusted OP via an OP-local identifier, configured during discovery through XRDS <LocalID> elements or HTML <link rel="openid2.local_id"> tags; this allows portability without altering the user's primary identity. For instance, a user might delegate http://[example.com](/page/Example.com)/ to an OP at https://myop.com/, where the RP treats the claimed URL as authoritative but authenticates via the delegated endpoint. XRI support in OpenID 2.0 facilitated such delegations with persistent canonical forms, though it was not incorporated into later standards like OpenID Connect 1.0, effectively deprecating its use in modern implementations.[2][4]
Authentication Flow
The OpenID authentication flow enables a relying party (RP) to verify that an end user controls a specific identifier without requiring the RP to store credentials or access the user's authentication details directly. This process relies on a series of HTTP redirects and signed messages exchanged between the user's browser (user agent), the RP, and the OpenID provider (OP). The flow begins when the user supplies an identifier—such as a URL or XRI—to the RP, typically through a login form.[2] In the basic authentication flow, the RP first normalizes the user-supplied identifier (for example, by prepending "http://" if absent) and performs discovery to locate the OP's endpoint URL and the claimed identifier. The RP then optionally establishes an association with the OP using Diffie-Hellman key exchange over a direct HTTPS connection to create a shared secret for message signing, enhancing security without relying on long-term keys. Next, the RP redirects the user's browser to the OP's authentication endpoint with an indirect request message containing parameters like the mode ("checkid_setup" or "checkid_immediate"), the claimed identifier, a return-to URL for the RP, and a nonce to prevent replay attacks. At the OP, the user authenticates—using methods like passwords or biometrics, though the specifics are implementation-dependent—and grants permission for the RP to receive the identity assertion. The OP then redirects the browser back to the RP's return-to URL with a response message.[2] The response includes either a positive assertion, confirming the user's control of the claimed identifier, or a negative assertion indicating failure (e.g., due to cancellation). Positive assertions are digitally signed using HMAC-SHA1 or HMAC-SHA256 with the shared secret from the association, containing fields such as the signed parameters, the claimed identifier, the OP endpoint, and a timestamp. The RP verifies the assertion by checking the return-to URL matches the request, validating the signature against the association (or by directly querying the OP if no association exists), ensuring the nonce is unique, and confirming the discovered endpoint details. This verification completes the flow, allowing the RP to establish a session with the user. OpenID 2.0 does not mandate message encryption beyond HTTPS transport, though Diffie-Hellman secures the association secret exchange.[2] OpenID supports different modes to accommodate various use cases. In "check_id_immediate" mode, the OP attempts to respond without user interaction, returning a positive assertion if prior consent exists or a negative one otherwise; this is useful for seamless check-ins. The "check_id_setup" mode requires full user interaction at the OP for authentication and approval, making it the standard for initial logins. A direct mode allows RPs and OPs to communicate without user-agent involvement, primarily for establishing associations or verifying assertions post-redirect.[2] The introduction of indirect identifiers in OpenID 1.1 allowed users to select their OP dynamically during the flow, using special values like "http://specs.openid.net/auth/2.0/identifier_select" in requests, which streamlined discovery for delegated identities. Assertions in OpenID 2.0 consist of these signed, tamper-evident messages that convey minimal identity claims, focusing on proof of control rather than rich attributes.[2]Providers and Relying Parties
In OpenID Authentication 2.0, the OpenID Provider (OP) serves as the entity responsible for managing user identities and handling authentication requests from relying parties. The OP facilitates user registration, though the specific methods for identifying authorized users fall outside the protocol's scope, allowing providers to implement their own mechanisms for account creation and management.[2] Upon receiving an authentication request, the OP authenticates the end-user's identity and obtains their approval for sharing identity information, subsequently redirecting the user's web browser with either a positive or negative assertion to confirm the outcome.[2] To ensure the integrity of these assertions, the OP signs them using established associations, such as those based on HMAC-SHA1 or HMAC-SHA256 algorithms, or through private associations in stateless modes.[2] Additionally, the OP hosts an endpoint URL—typically over HTTP or HTTPS—for processing protocol messages, which is discovered by relying parties through mechanisms like XRDS documents or HTML rel tags.[2] The Relying Party (RP), in contrast, acts as the service or application seeking to authenticate users via OpenID, initiating the process by normalizing the user-supplied identifier, such as a URL or XRI.[2] The RP then performs discovery on this identifier using Yadis protocols or HTML-based methods to locate the appropriate OP endpoint URL.[2] To secure the exchange, the RP may establish shared associations with the OP, often using Diffie-Hellman key exchange, and sends signed authentication requests to the OP.[2] Upon receiving the OP's response, the RP verifies critical elements including the return URL, previously discovered information, nonces to prevent replay attacks, and the signatures on assertions, either directly with the OP or via pre-established associations.[2] This verification enables seamless integration of OpenID into web applications, allowing RPs to delegate authentication without storing user credentials.[2] Interoperability between OPs and RPs is facilitated by standardized protocol endpoints and open-source libraries that simplify implementation. For instance, OP endpoints commonly use paths like "/openid/server" to handle authentication requests, as outlined in the specification.[2] Libraries such as JanRain's PHP-based toolkit and DotNetOpenAuth for .NET provide comprehensive support for both OP and RP roles, enabling developers to build compatible systems with features like association management and extension handling.[11] These tools ensure adherence to OpenID 2.0 while supporting backward compatibility with earlier versions like 1.1.[11] An early example of an OP was MyOpenID, a free service launched by JanRain that allowed users to create OpenID identities but ceased operations in 2014.[12] Modern implementations continue to rely on such libraries for OpenID 2.0 support, though the protocol has largely been superseded by OpenID Connect.[11]History and Evolution
Early Development
OpenID originated in 2005 when Brad Fitzpatrick, founder of the LiveJournal blogging platform and an employee of Six Apart, developed it as a solution to the challenges of distributed authentication across websites. At the time, LiveJournal faced issues with comment spam and the need for users to maintain multiple logins for different services, prompting Fitzpatrick to create a lightweight, decentralized system where users could authenticate using a single URL-based identity without sharing passwords or requiring central coordination. This approach aimed to enable interoperability among blogging platforms like LiveJournal, TypePad, and Movable Type, leveraging simple HTML discovery mechanisms to verify identity ownership.[13][14] The first specification, OpenID 1.0, was published in May 2005 and emphasized basic URL-based authentication through one-time signed assertions, eliminating the need for SSL, public keys, or browser plugins. It allowed static HTML sites to act as identity providers with minimal infrastructure, using TypeKey—Six Apart's authentication service—as the inaugural OpenID provider to demonstrate practical implementation. Development was community-driven via a wiki on openid.net, fostering contributions from developers interested in open identity standards, while Six Apart provided core support through its platforms.[13][15] In December 2006, OpenID 1.1 was released, building on the initial version by introducing extensions for delegation (allowing users to point to third-party providers via HTML links) and improving compatibility with AJAX-based interfaces for smoother user experiences. This update addressed early limitations in stateless operation and caching, enabling broader adoption among early relying parties. Microsoft offered partial support during this phase, signaling growing industry interest, though full integration came later; meanwhile, integrations with platforms like Blogger and Flickr began emerging, showcasing OpenID's potential for comment authentication and user verification on photo-sharing and blogging sites.[16][17]Specification Milestones
The OpenID specifications evolved through a series of formal releases under the OpenID Foundation, which was established in June 2007 to oversee standardization and intellectual property policies for the protocol. The foundational milestone came with OpenID Authentication 2.0, finalized on December 5, 2007, which built upon earlier informal developments like the Yadis project for service discovery and introduced enhancements such as support for Extensible Resource Identifiers (XRIs) alongside URLs as user identifiers. This version emphasized decentralized authentication without requiring relying parties to store user credentials, while incorporating mechanisms for improved security and interoperability.[2][18] Accompanying the core authentication spec, the OpenID Attribute Exchange (AX) 1.0 extension was also released on December 5, 2007, enabling the secure exchange of user attributes—such as names or email addresses—between OpenID providers and relying parties during authentication. To address phishing risks, the Provider Authentication Policy Extension (PAPE) 1.0 was finalized on December 30, 2008, allowing relying parties to request specific authentication policies, like multi-factor methods, from providers and receive confirmation of their application. The User Interface (UI) Extension 1.0, released in 2008, further refined user experience by specifying modes for authentication interfaces, such as popup windows or embedded iframes, to streamline interactions across devices.[19][20] As OpenID matured, certain elements faced deprecation to align with evolving web standards and security practices. XRIs, initially integrated in OpenID 2.0 for abstract identifiers, were phased out in the 2010s following the disbandment of the OASIS XRI Technical Committee in 2015, due to limited adoption and maintenance challenges. This shift culminated in the transition toward OpenID Connect, an identity layer built on OAuth 2.0, with its core specification finalized on February 26, 2014, effectively superseding OpenID 2.0 for modern implementations while providing backward migration paths.[21][22]OpenID Foundation
Organizational Structure
The OpenID Foundation was established in 2007 as a non-profit organization dedicated to stewarding the development and maintenance of OpenID specifications, ensuring their open availability to promote interoperable digital identity solutions.[3][23] The Foundation's governance is led by a Board of Directors, comprising up to 38 members categorized into sustaining directors appointed by sustaining members, community directors elected for two-year staggered terms, and corporate directors elected annually based on membership size.[24][23] Operational activities are conducted through specialized working groups, such as the AB/Connect Working Group for OpenID Connect specifications, the FAPI Working Group for financial-grade API profiles, and the Shared Signals Working Group for security event sharing, all operating on a consensus-driven model open to contributors via a standard contribution agreement.[25][26][27] Membership is structured into three primary classes—sustaining, individual, and corporate—with the Board able to define additional tiers; participation is accessible to private entities, governments, non-profits, and individuals, though not required for contributing to working groups.[28][23] Key operations include a specification development process managed by working groups in three phases: drafts for initial proposals, implementer's drafts for testing and refinement, and final specifications upon consensus approval, with all outputs freely available under an open copyright license.[29][30] The Foundation administers certification programs featuring self-certification and conformance test suites for standards like OpenID Connect and Financial-grade API, adopted by entities including the UK and Brazilian governments to verify ecosystem compliance.[7][31] International chapters, governed by a national chapters policy, support localized adoption and profiling, with examples including the OpenID Foundation Japan. As of 2025, the active international chapter is OpenID Foundation Japan (OIDF-J).[32][33] Headquartered in San Ramon, California, United States, the Foundation tracks specification progress through periodic updates, board elections, and public announcements.[1][34]Key Contributors and Chapters
Brad Fitzpatrick is recognized as the founder of OpenID, having developed the initial authentication protocol in May 2005 while working as the creator of the LiveJournal community website.[35] His contributions extended to evangelism efforts, including a prominent presentation on OpenID at the Internet Identity Workshop (IIW) in October 2005, which helped build early community momentum.[36] David Recordon served as an early advocate and key collaborator in OpenID's development, co-authoring the OpenID Authentication 1.1 specification in 2006 alongside Fitzpatrick. As a founding board member of the OpenID Foundation established in 2007, Recordon played a pivotal role in promoting the protocol through global outreach and specification finalization, including announcing the completion of OpenID 2.0 in 2007.[37] His work also bridged OpenID with related standards like OAuth. Mike Jones has been a longstanding technical leader in the OpenID ecosystem, serving on the OpenID Foundation's Board of Directors since 2008 and architecting the globally adopted OpenID certification program.[38] As a principal contributor to the OpenID Connect working group, Jones co-authored core specifications and continues to drive updates, including federation enhancements, through his role as board secretary and active participation in foundation workshops.[39] The OpenID Foundation supports international chapters to localize efforts, host events, and adapt specifications for regional needs. The Japan chapter, known as OpenID Foundation Japan (OIDF-J), was announced in February 2008 in collaboration with eleven technology companies and formally established in April 2008, focusing on education, interoperability testing, and events like the recurring OpenID Summit Tokyo, which celebrated OpenID Connect's tenth anniversary in 2024. As of 2025, OIDF-J remains the active international chapter, contributing to the Connect working group by providing localized feedback and hosting interops that influenced profiles for mobile and verifiable credentials.[33][32] An earlier European effort, the independent OpenID Europe Foundation formed in 2007 in Belgium, handled initial trademark registrations but is no longer active as a chapter.Policies and Legal Framework
The OpenID Foundation's intellectual property policies govern the development and use of its specifications, ensuring open access while protecting contributors and implementers. Specifications, including Work Group Drafts, Implementers' Drafts, and Final Specifications, are licensed under the OpenID Copyright License, which provides a perpetual, irrevocable, non-exclusive, royalty-free, worldwide copyright license to reproduce, distribute, publicly display, publicly perform, and create derivative works for the purpose of developing and implementing compliant products.[40] This license requires attribution to the OpenID Foundation and applies to all OIDF-approved specifications, promoting widespread adoption without restrictive terms. For patents, the Intellectual Property Rights (IPR) Policy mandates that contributors grant a royalty-free, worldwide, non-exclusive patent license covering Necessary Claims—defined as claims essential to implementing the specifications—to the Foundation, other contributors, and implementers.[41] The contribution process is structured to maintain openness and mitigate legal risks through formal agreements. All individuals or entities submitting contributions must execute the OpenID Foundation's standard Contribution Agreement, which incorporates the IPR Policy and Process Document by reference, granting the Foundation necessary copyright and patent rights while affirming the contributor's ownership of their submissions.[42] This agreement ensures that contributions can be integrated into specifications without encumbrances, with contributors promising not to assert patent claims against compliant implementations, thereby facilitating collaborative development.[41] Unlike some standards bodies, the current IPR Policy does not require disclosure of potential essential patents, placing the onus on participants to act in good faith.[41] On March 1, 2012, the OpenID Foundation Board unanimously approved a patent pledge statement for inclusion in all specifications, explicitly granting implementers a royalty-free license under any Foundation-owned patents essential to compliance, further reducing barriers to adoption.[43] Regarding trademarks, the Foundation secured the OpenID trademark in the United States in March 2008, resolving early community discussions on ownership and usage, and later formalized the OpenID Trademark and Service Mark License Policy in 2013 to guide acceptable branding practices.[44] Implementations of OpenID protocols must comply with applicable privacy regulations, such as the EU's General Data Protection Regulation (GDPR), particularly for handling user consent and personal data in authentication flows, as outlined in the Foundation's Privacy Policy.[45] As of 2025, the OpenID Foundation has faced no major lawsuits related to its specifications or policies.[40]Adoption and Implementations
Major Providers and Users
OpenID's early adoption in the mid-2000s was driven by several prominent providers, including MyOpenID, which operated from 2005 until its shutdown on February 1, 2014, after being acquired by Janrain.[46][47] AOL and Yahoo also served as key OpenID 2.0 providers during this period, enabling users to authenticate across sites with their existing accounts, though both discontinued support in the 2010s.[48] Specifically, Yahoo ended OpenID 2.0 support by mid-2015 as part of a broader migration to OpenID Connect.[9] By 2025, OpenID 2.0 provider support has significantly diminished, with major players like Google terminating it on April 20, 2015, to prioritize OpenID Connect.[49] PayPal maintains legacy compatibility through OpenID Connect implementations but no longer actively supports pure OpenID 2.0.[50] Niche providers persist, such as IndieAuth.net, which offers OpenID compatibility via endpoints like openid.indieauth.com for decentralized authentication in personal websites and indie web tools.[51] OpenID 2.0 usage has continued to decline due to deprecation and the rise of more secure alternatives.[52] In contrast, OpenID Connect has seen widespread adoption by 2025, with major providers including Google, Microsoft, and Apple enabling single sign-on for billions of users across web, mobile, and applications. As of August 2025, over 82,000 verified companies utilize OpenID Connect implementations, reflecting its role in powering secure authentications globally.[53][3] Early relying parties included platforms like WordPress, which integrated OpenID 2.0 through plugins for user logins starting in the late 2000s, and Stack Overflow, a strong early advocate that launched with OpenID support in 2008 to enable federated authentication.[54] However, Stack Overflow discontinued OpenID logins on July 25, 2018, shifting to other methods like OAuth.[55] Current integrations remain in select forums and wikis, often via legacy plugins or hybrid setups, but adoption has waned as sites migrate to OpenID Connect for enhanced security and interoperability.[56]Use Cases and Integration Examples
OpenID facilitates single sign-on (SSO) scenarios where users can authenticate to blogs, forums, and e-commerce platforms using a single set of credentials from an OpenID provider, eliminating the need for site-specific accounts.[57] This approach reduces password fatigue and enhances user convenience across decentralized web services. For instance, users could log into multiple websites by providing their OpenID identifier, such as a URL from a trusted provider, allowing seamless access without repeated registrations.[58] A notable early example occurred in 2008 when Google enabled OpenID for commenting on Blogger posts, permitting users to sign in with their existing OpenID credentials to participate in discussions.[59] Similarly, the BBC trialed an OpenID system that integrated Yahoo logins for comment authentication on its platforms, demonstrating practical application in media forums to simplify user interactions.[59] In e-commerce contexts, OpenID supported SSO integrations that allowed customers to access shopping carts and accounts across affiliated sites using one identity, streamlining transactions while maintaining decentralized control.[58] In enterprise environments prior to the widespread adoption of OpenID Connect around 2014, OpenID 2.0 enabled internal identity federation by allowing organizations to link authentication across internal applications and services without centralized credential storage.[58] Large enterprises like Microsoft and Novell utilized OpenID for federated SSO, where employees could access intranets, collaboration tools, and legacy systems via a unified identity provider, improving efficiency in pre-cloud infrastructures.[58] Integration examples include content management systems configured as relying parties. The Drupal OpenID SSO Relying Party module, released in 2011, enables Drupal sites to authenticate users against a central OpenID provider, redirecting login requests for SSO across networked installations.[60] For WordPress, early plugins such as the OpenID plugin (version 2.1.3 and prior) allowed site administrators to set up relying party functionality by incorporating OpenID URL fields in user profiles, facilitating authentication via external providers.[61] Hybrid setups with social logins were common, as providers like Google and Yahoo offered OpenID services, enabling users to leverage social accounts as OpenID identifiers for broader SSO compatibility.[58] In modern applications as of 2025, OpenID Connect supports diverse use cases, including "Sign in with Google" or "Sign in with Apple" for consumer apps, enabling secure profile data access and SSO across platforms. Enterprise integrations, such as those using certified OpenID Connect providers like Microsoft Azure AD, facilitate federated access to cloud services and APIs for millions of organizations. Niche open-source projects continue to support legacy OpenID 2.0 compatibility; for example, the Gluu Server incorporates OpenID support for SSO in community-driven deployments, allowing developers to federate access in custom forums and tools while maintaining interoperability with older specifications.[31][62]Security and Privacy
Common Vulnerabilities
One notable authentication vulnerability in early OpenID implementations involved manipulation of authentication requests due to the lack of authenticity and integrity guarantees, leading to relying party (RP) confusion about the identity provider (IdP) involved in the flow.[63] This issue, identified around 2008 in OpenID 2.0 evaluations, allowed adversaries to forge or alter requests, potentially enabling unauthorized access by tricking the RP into accepting invalid authentication responses.[63] In OpenID 1.0, nonce reuse flaws permitted replay attacks, as many RPs failed to properly validate nonce values in authentication responses, allowing intercepted messages to be reused against the same or other sites.[63] Empirical analysis of implementations revealed that inadequate nonce checking exposed users to repeated exploitation of captured authentication data, undermining the protocol's resistance to passive eavesdropping.[63] Phishing attacks targeting OpenID often exploited OP impersonation through similar domains, where attackers registered lookalike URLs (e.g., using homograph attacks or slight variations) to mimic legitimate IdPs and capture user credentials during login redirects.[64] In 2007, IdP selection attacks further compounded this risk, as demonstrated by CVE-2007-1652, where remote attackers could forcibly log users into OpenID-enabled sites via crafted web pages that exploited cached tokens, disclosing personal information and adding unauthorized sites to trusted lists without user consent.[65] Privacy concerns in OpenID arose from unintended attribute disclosure via the Attribute Exchange (AX) extension, where some implementations did not verify signed AX data, allowing attackers to modify or inject attributes during authentication and expose sensitive user information to malicious RPs without detection.[66] This flaw, highlighted in a 2011 security advisory, enabled low-effort impersonation or data leakage, particularly when high-trust attributes from IdPs were not properly authenticated.[66] The protocol's trust model assumptions introduced additional vulnerabilities, relying on RPs to inherently trust OPs for authentication without robust verification of OP integrity or user-selected IdPs, which could lead to exploitation if a malicious OP was chosen or compromised.[67] This decentralized trust structure assumed low assurance levels suitable only for non-critical applications, leaving higher-stakes scenarios exposed to issues like association poisoning or identity recycling when assumptions about secure OP-RP communication failed.[67] A prominent specific event was the 2014 Covert Redirect vulnerability, an open redirector attack affecting OpenID's redirect-based flows, where attackers altered the redirect_uri parameter to bypass validation and redirect users to malicious sites, potentially exposing authorization codes or tokens during authentication.[68] This issue, analogous to phishing but embedded in the protocol's URI handling, impacted OpenID-enabled sites by allowing covert exfiltration of user sessions without altering core credentials.[68] Authentication hijacking over HTTP represented another critical exposure, as OpenID's redirect mechanisms in unsecured connections enabled man-in-the-middle attacks, where adversaries intercepted and replayed authentication responses to hijack sessions or add malicious identities to user accounts.[61] Early implementations, such as certain WordPress OpenID plugins, lacked protections like CSRF tokens, facilitating such hijacks by exploiting HTTP's lack of encryption to manipulate OpenID URLs and force unauthorized logins.[61] In February 2025, the OpenID Foundation disclosed a vulnerability (CVE-2025-27370) due to ambiguities in JWT audience values in OpenID Connect's private_key_jwt client authentication, potentially allowing malicious authorization servers to inject attacker-controlled audiences into tokens, compromising security objectives like token integrity. No known exploits occurred, but it prompted spec updates.[69][70] Additional 2025 vulnerabilities include CVE-2025-59363 in OneLogin, where API keys could access OIDC client secrets, risking exposure in shared credential environments (patched in version 2025.3.0), and CVE-2025-12466 in Drupal's Simple OAuth module, enabling authentication bypass via alternate paths in OpenID Connect flows.[71][72] Persistent misconfigurations like nOAuth in Microsoft Entra ID continue to affect ~9% of SaaS apps integrating OpenID flows, enabling account takeovers as of June 2025.[73]Mitigation Strategies and Best Practices
To secure OpenID implementations, relying parties (RPs) and openID providers (OPs) must prioritize the use of HTTPS for all endpoints, including discovery, authentication requests, and responses, to prevent eavesdropping and man-in-the-middle attacks; this involves employing SSL/TLS with certificates from trusted authorities and ensuring HTTP URLs redirect to HTTPS equivalents.[2] Strict validation of message signatures is essential, utilizing HMAC-SHA256 (preferred over HMAC-SHA1) and associations established via Diffie-Hellman key exchange to verify the authenticity of responses, with RPs either storing associations or performing direct verification against the OP.[2] For enhanced authentication assurance, implement the Provider Authentication Policy Extension (PAPE) to request and enforce multi-factor authentication (MFA), where RPs specify policies such as "Multi-Factor" (e.g., knowledge factor like a PIN combined with possession factor like a soft token) or "Multi-Factor Physical" (e.g., hardware token) in requests, and OPs respond with details of the applied method to confirm compliance.[20] RPs should verify OP endpoints by discovering them through XRDS documents (ensuring digital signatures per XMLDSIG to detect tampering) and validating that response origins match the discovered URLs, thereby mitigating risks from rogue providers.[2] User education plays a critical role, with OPs and RPs advising end-users to access sites only via top-level browser windows and recognize phishing attempts by verifying domain authenticity before entering credentials.[2] Attribute filtering is a key privacy strategy, where RPs request only necessary attributes via extensions like Attribute Exchange (AX) and OPs limit disclosure to the minimum required, reducing exposure of sensitive data such as email or full names unless explicitly consented. Following OpenID Foundation (OIDF) guidelines established post-2014, RPs must rigorously validate redirect URIs (openID.return_to) by ensuring exact matches against pre-registered values, rejecting any deviations to counter open redirector risks in authentication flows.[74] Useful tools include the OIDF's conformance testing suites and certification checklists, which guide implementers through security validation for interoperability, covering aspects like endpoint protection and policy enforcement; certified implementations demonstrate adherence to these standards.[7] To monitor for replay attacks, RPs should track nonces in positive assertions and timestamps in responses, rejecting duplicates or those outside a defined validity window (e.g., via session storage), while OPs apply rate limiting to curb denial-of-service attempts.[2] In 2025, OIDF profiles emphasize mandatory adoption of TLS 1.3 for all connections to leverage its improved security against downgrade and protocol attacks, superseding older TLS versions in OpenID deployments.[75]OpenID Connect
Relation to OpenID 2.0
OpenID Connect (OIDC) serves as an identity layer on top of the OAuth 2.0 authorization framework, enabling clients to verify the identity of end-users and obtain basic profile information through standardized authentication mechanisms. Finalized by the OpenID Foundation (OIDF) in February 2014 with the release of the OIDC Core 1.0 specification, it represents a modern evolution in decentralized identity protocols designed for enhanced interoperability and security in web and mobile applications.[21][4] In contrast to OpenID 2.0, the preceding iteration of the OpenID protocol finalized in December 2007, OIDC introduces significant architectural shifts to address limitations in scalability, security, and ease of implementation. OpenID 2.0 relied on signed messages formatted in a key-value encoding scheme, where responses were authenticated using mechanisms like HMAC-SHA1 signatures over associations between relying parties and providers. OIDC, however, employs JSON-based structures throughout, with identity assertions delivered via JSON Web Tokens (JWTs) as ID tokens that compactly encode claims such as the issuer, subject, and authentication timestamp in a self-contained, verifiable format. This JWT approach facilitates stateless verification and reduces reliance on shared secrets, marking a departure from OpenID 2.0's more cumbersome direct communication and verification flows.[11][2][6] OIDC does not provide direct backward compatibility with OpenID 2.0, as it operates on a fundamentally different protocol stack built atop OAuth 2.0 rather than extending the older specification's direct authentication model. Instead, OIDC supersedes OpenID 2.0 for new deployments, encouraging migration to leverage its improved privacy features, such as selective disclosure of claims, and broader ecosystem support. The OIDF has designated OpenID 2.0 as obsolete, with libraries and implementations for the legacy protocol maintained separately from active OIDC development.[11][2] The OIDC Core 1.0 specification has undergone maintenance updates to incorporate errata and clarifications, including errata set 2 released in December 2023, ensuring ongoing robustness without altering core semantics. By 2025, OIDC Core 1.0 achieved further international standardization as ITU-T Recommendation X.1285 in May 2025, underscoring its global adoption and stability as the preferred successor to OpenID 2.0.[4][76][77]Key Features and Flows
OpenID Connect (OIDC) introduces several core features that build upon OAuth 2.0 to provide robust identity layer functionality. The ID Token is a JSON Web Token (JWT) that conveys claims about the authentication of an End-User by the OpenID Provider (OP), including standard claims such as issuer (iss), subject (sub), audience (aud), and expiration time (exp).[78] This token is digitally signed to ensure integrity and authenticity, with the recommended signing algorithm being RS256 unless otherwise specified.[79] The UserInfo Endpoint allows a Relying Party (RP) to retrieve additional claims about the authenticated End-User by presenting a valid Access Token, supporting both signed and unsigned responses for flexibility in deployment.[80] For dynamic discovery, OIDC relies on the discovery document published by the OP at the path /.well-known/openid-configuration, which provides metadata such as endpoint URIs, supported scopes, and claim types to facilitate interoperability without hardcoding configurations.[81]
OIDC defines several authentication flows tailored to different client types and security requirements, all initiated via the Authorization Endpoint. The Authorization Code Flow, the most secure and recommended for confidential clients, involves the RP redirecting the End-User to the OP for authentication, after which the OP issues an authorization code that the RP exchanges at the Token Endpoint for an Access Token and ID Token; this flow is enhanced by Proof Key for Code Exchange (PKCE) to mitigate authorization code interception attacks for public clients.[82] The Implicit Flow, which directly returns the ID Token and optionally the Access Token in the redirect URI fragment, has been deprecated in favor of more secure alternatives due to vulnerabilities like token leakage in browser histories.[83] The Hybrid Flow combines elements of the previous two by returning an authorization code alongside tokens in the initial redirect, allowing immediate partial access while deferring full token issuance to the Token Endpoint for added security.[84] For machine-to-machine scenarios without user involvement, the Client Credentials Flow enables clients to obtain an Access Token directly from the Token Endpoint using client authentication, though it does not issue ID Tokens as it lacks End-User context.[85]
To ensure conformance and interoperability, OIDC 1.0 specifies mandatory profiles for OPs and RPs, including support for RS256 ID Token signing, the prompt and display parameters, and the max_age claim for authentication freshness; dynamic OPs must additionally implement discovery, dynamic client registration, and the UserInfo Endpoint.[86]
Extensions to OIDC address specialized use cases, particularly in high-security environments. The Financial-grade API (FAPI) profiles, such as FAPI 2.0, impose stringent security requirements on top of OIDC and OAuth 2.0, including mutual TLS for client authentication, sender-constrained tokens via DPoP, and precise error handling to protect financial APIs against advanced threats.[87] The Shared Signals Framework (SSF) 1.0, finalized in 2025, enables OPs and RPs to share privacy-preserving security events—such as authentication attempts or risk incidents—via secure webhooks or push notifications, using Security Event Tokens (SETs) to enhance real-time threat detection across ecosystems.[88] Furthermore, the OpenID for Verifiable Presentations 1.0 specification, approved in 2025, integrates OIDC with decentralized identifiers by allowing RPs to request and receive Verifiable Credentials as presentations through OAuth-protected endpoints, supporting selective disclosure and tamper-evident proofs for privacy-focused identity verification.[89]