Recent from talks
Nothing was collected or created yet.
CAST-128
View on Wikipedia| General | |
|---|---|
| Designers | Carlisle Adams and Stafford Tavares |
| First published | 1996 |
| Successors | CAST-256 |
| Cipher detail | |
| Key sizes | 40 to 128 bits |
| Block sizes | 64 bits |
| Structure | Feistel network |
| Rounds | 12 or 16 |

In cryptography, CAST-128 (alternatively CAST5) is a symmetric-key block cipher used in a number of products, notably as the default cipher in some versions of GPG and PGP. It has also been approved for Government of Canada use by the Communications Security Establishment. The algorithm was created in 1996 by Carlisle Adams and Stafford Tavares using the CAST design procedure.[1]
Another member of the CAST family of ciphers, CAST-256 (a former AES candidate) was derived from CAST-128. According to some sources, the CAST name is based on the initials of its inventors, though Bruce Schneier reports the authors' claim that "the name should conjure up images of randomness".[2]
CAST-128 is a 12- or 16-round Feistel network with a 64-bit block size and a key size of between 40 and 128 bits (but only in 8-bit increments). The full 16 rounds are used when the key size is longer than 80 bits.[3]
Components include large 8×32-bit S-boxes based on bent functions, key-dependent rotations, modular addition and subtraction, and XOR operations. There are three alternating types of round function, but they are similar in structure and differ only in the choice of the exact operation (addition, subtraction or XOR) at various points.
Although Entrust holds a patent on the CAST design procedure, CAST-128 is available worldwide on a royalty-free basis for commercial and non-commercial uses.
See also
[edit]References
[edit]- ^ Carlisle M. Adams (1997). "Constructing Symmetric Ciphers Using the CAST Design Procedure" (PDF). Designs, Codes, and Cryptography (12): 283–316.
- ^ Bruce Schneier (1996). Applied Cryptography (2nd ed.). John Wiley & Sons. pp. 334–335. ISBN 0-471-11709-9.
- ^ Carlisle M. Adams (1997-05-12). "CAST Design Procedure Addendum" (PDF). Entrust. Archived from the original (PDF) on 2012-07-14. Retrieved 2013-01-15.
External links
[edit]- RFC 2144 The CAST-128 Encryption Algorithm
- "CAST Encryption Algorithm Related Publications". Archived from the original on 2007-12-17. Retrieved 2013-01-15.
- "Standard Cryptographic Algorithm Naming: Symmetric Ciphers - CAST-128". Retrieved 2013-01-14.
- "CSEC Approved Cryptographic Algorithms for the Protection of Sensitive Information and for Electronic Authentication and Authorization Applications within GC". Communications Security Establishment Canada. 2011-03-01. Archived from the original on 2014-08-07. Retrieved 2014-12-04.
CAST-128
View on GrokipediaOverview
Description
CAST-128 is a symmetric-key block cipher designed for confidentiality in data encryption.[4] It operates as a Feistel network, processing plaintext in 64-bit blocks to produce ciphertext of equal length.[4] The algorithm supports variable key lengths ranging from 40 to 128 bits, in 8-bit increments, to provide flexibility for export restrictions on cryptographic implementations.[4] It employs 12 rounds for key sizes of 80 bits or less and 16 rounds for longer keys, enhancing security based on key strength.[4] CAST-128 was developed in the early 1990s by Carlisle Adams and Stafford Tavares at Entrust Technologies.[5] Intended as an alternative to the Data Encryption Standard (DES), it offers improved security margins through its substitution-permutation structure.[4]Specifications
CAST-128 is a symmetric-key block cipher with a fixed block size of 64 bits.[1] It supports variable key sizes ranging from 40 to 128 bits in 8-bit increments: specifically, 40, 48, 56, 64, 72, 80, 88, 96, 104, 112, 120, or 128 bits.[1] The number of rounds depends on the key size, using 12 rounds for keys of 80 bits or fewer and 16 rounds for longer keys.[1] The cipher employs a Feistel structure, incorporating substitution via S-boxes, arithmetic operations (modular addition and subtraction), exclusive-or (XOR), and circular left shifts within each round function.[1] CAST-128 provides implicit support for standard block cipher modes including ECB and CBC, with explicit details and test vectors for ECB in the specification; it can also be adapted for CFB and OFB modes as typical for such ciphers, though no proprietary modes are defined.[1] Keys and data are processed in big-endian byte order, with the most significant byte first.[1] The following table summarizes the key sizes, corresponding number of rounds, and effective security level (equivalent to the key size in bits):| Key Size (bits) | Rounds | Effective Security (bits) |
|---|---|---|
| 40 | 12 | 40 |
| 48 | 12 | 48 |
| 56 | 12 | 56 |
| 64 | 12 | 64 |
| 72 | 12 | 72 |
| 80 | 12 | 80 |
| 88 | 16 | 88 |
| 96 | 16 | 96 |
| 104 | 16 | 104 |
| 112 | 16 | 112 |
| 120 | 16 | 120 |
| 128 | 16 | 128 |
History
Development
CAST-128 was designed between 1993 and 1995 by Carlisle Adams and Stafford Tavares while working at Northern Telecom (later rebranded as Entrust Technologies) in Ottawa, Canada.[6][7] The cipher's development was driven by growing concerns over the Data Encryption Standard (DES), whose 56-bit key length was increasingly vulnerable following the introduction of differential cryptanalysis in 1990, as well as stringent U.S. export controls that restricted strong cryptography to 40-bit keys for non-U.S. markets.[4] Adams and Tavares sought to create a versatile symmetric block cipher offering stronger security while accommodating variable key sizes from 40 to 128 bits in 8-bit increments to comply with export regulations and provide scalability.[4] Central to the design principles was building resistance against both differential and linear cryptanalysis, achieved through the use of irregularly structured substitution boxes (S-boxes) and heterogeneous round functions that varied in operations across rounds to avoid predictable patterns.[8] These elements drew from the broader CAST design procedure, initially outlined in earlier work on S-box construction resistant to differential attacks.[9] The algorithm was first publicly described by Adams in 1996 at the Selected Areas in Cryptography (SAC) workshop in Kingston, Ontario. Although not initially released as open-source due to patent protection on the underlying CAST procedure, its full specification was later published in 1997 as Internet Engineering Task Force (IETF) Request for Comments (RFC) 2144, making it freely available on a royalty-free basis.[4][6] As the inaugural member of the CAST family of ciphers, CAST-128 laid the groundwork for subsequent variants, including CAST-256, by demonstrating the efficacy of the CAST procedure in producing secure, efficient encryption algorithms.Standardization and Adoption
CAST-128 achieved formal standardization through RFC 2144, published by the Internet Engineering Task Force (IETF) in May 1997 and authored by Carlisle Adams. This informational RFC details the complete algorithm specification, including its variable key sizes from 40 to 128 bits in 8-bit increments, and provides a reference implementation in the C programming language to facilitate adoption and verification.[10] The algorithm was further recognized in international standards, notably ISO/IEC 18033-3:2005, which includes CAST-128 among approved 64-bit block ciphers for encryption alongside algorithms like TDEA and MISTY1. It received approval for use in Canadian government systems by the Communications Security Establishment, permitting its application for protecting Protected A and Protected B information with 128-bit keys, until its deprecation at the end of 2023.[11][12][13] However, in 2023, the Communications Security Establishment deprecated CAST-128, recommending migration to stronger algorithms like AES for ongoing use.[13] Early adoption occurred rapidly following standardization, with integration into Pretty Good Privacy (PGP) software starting in version 5 released in 1997, where it served as a symmetric cipher option for email encryption under the OpenPGP framework. Similarly, CAST-128 was incorporated into Secure Shell (SSH) protocols for secure remote access, as specified in RFC 4253 for the SSH transport layer. During the 1990s, a 40-bit key variant was commonly employed to comply with U.S. export restrictions on strong cryptography, though full 128-bit implementations became unrestricted thereafter.[14][15][4] By the 2010s, CAST-128's usage declined as it was overshadowed by the Advanced Encryption Standard (AES), largely due to its 64-bit block size vulnerability to birthday attacks in high-volume data scenarios; nonetheless, it persists in legacy systems and certain protocol implementations for backward compatibility.[16]Design
Overall Structure
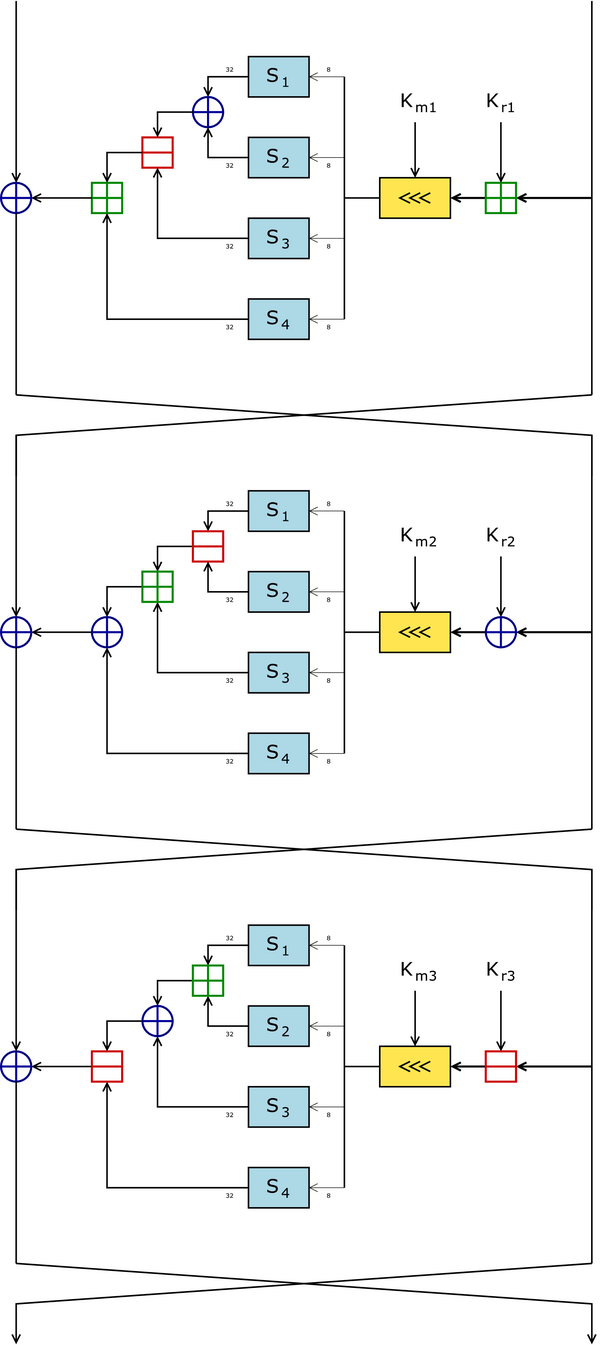
CAST-128 operates as a Feistel network cipher, processing fixed 64-bit blocks of data by splitting each block into two 32-bit halves, L and R. In the encryption process, the initial plaintext block is divided such that L_0 comprises the first 32 bits and R_0 the remaining 32 bits. Each round updates the halves by setting the new left half to the previous right half (L_i = R_{i-1}) and computing the new right half as the previous left half XORed with the output of the round function applied to the previous right half (R_i = L_{i-1} \oplus f(R_{i-1}, K_{m,i}, K_{r,i})). This structure ensures that decryption can use the same round function with subkeys in reverse order.[17] The round function f processes a 32-bit input using a masking subkey K_{m,i} (32 bits) and a rotation subkey K_{r,i} (5 bits), incorporating arithmetic operations, bitwise XOR, modular addition and subtraction (all modulo 2^{32}), and lookups in four 8 \times 32-bit substitution boxes (S1 to S4). The function begins by applying a masking operation to the input D (the right half): for Type 1 rounds, I = (K_{m,i} + D) rotated left by K_{r,i} bits; for Type 2, I = (K_{m,i} \oplus D) rotated left by K_{r,i} bits; for Type 3, I = (K_{m,i} - D) rotated left by K_{r,i} bits. The resulting 32-bit I is divided into four 8-bit parts (I_a, I_b, I_c, I_d), each looked up in one S-box to yield four 32-bit outputs, which are then combined differently per type: Type 1 uses ((S1[I_a] \oplus S2[I_b]) - S3[I_c]) + S4[I_d]; Type 2 uses ((S1[I_a] - S2[I_b]) + S3[I_c]) \oplus S4[I_d]; Type 3 uses ((S1[I_a] + S2[I_b]) \oplus S3[I_c]) - S4[I_d]. These masking types cycle through the rounds to enhance diffusion.[18] The cipher performs either 12 rounds (for key sizes up to 80 bits) or 16 rounds (for longer keys), with the types assigned as follows: rounds 1, 4, 7, 10, 13, and 16 use Type 1; rounds 2, 5, 8, 11, and 14 use Type 2; rounds 3, 6, 9, 12, and 15 use Type 3. After all rounds, the halves are swapped to form the 64-bit ciphertext C = R_n || L_n, where n is the number of rounds.[17] Decryption mirrors encryption exactly, applying the same round functions but processing the subkeys in reverse sequence from the last round to the first, leveraging the self-inverse property of the Feistel construction.[17] A high-level pseudocode outline of the encryption is:Split plaintext P into L_0 (bits 1-32), R_0 (bits 33-64)
n = 12 if key length ≤ 80 bits else 16
for i = 1 to n:
L_i = R_{i-1}
I = masking_operation(R_{i-1}, K_{m,i}) rotated left by K_{r,i} bits // type-dependent
f_output = combine_Sboxes(I_a, I_b, I_c, I_d) // type-dependent operations
R_i = L_{i-1} \oplus f_output
Swap: ciphertext C = R_n || L_n
Split plaintext P into L_0 (bits 1-32), R_0 (bits 33-64)
n = 12 if key length ≤ 80 bits else 16
for i = 1 to n:
L_i = R_{i-1}
I = masking_operation(R_{i-1}, K_{m,i}) rotated left by K_{r,i} bits // type-dependent
f_output = combine_Sboxes(I_a, I_b, I_c, I_d) // type-dependent operations
R_i = L_{i-1} \oplus f_output
Swap: ciphertext C = R_n || L_n