Recent from talks
Nothing was collected or created yet.
Contact list
View on WikipediaThis article needs additional citations for verification. (October 2024) |
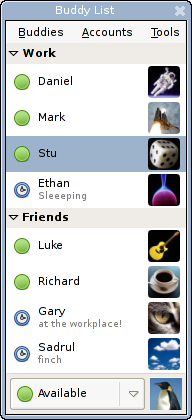
A contact list is a collection of screen names.[1] It is a commonplace feature of instant messaging, Email clients, online games and mobile phones.[1] It has various trademarked and proprietary names in different contexts.[1]
Contacts lists' windows show screen names that represent actual other people.[2] To communicate with someone on the list, the user can select a name and act upon it, for example open a new E-mail editing session, instant message, or telephone call. In some programs, if your contact list shows someone, their list will show yours. Contact lists for mobile operating systems are often shared among several mobile apps.[citation needed]
Some text message clients allow users to change their display name at will, while others only allow them to reformat their screen name (add/remove spaces and capitalize letters). Generally, it makes no difference other than how it is displayed.[citation needed]
With most programs, the contact list can be minimized to keep it from getting in the way, and is accessed again by selecting its icon.[citation needed]
The style of the contact list is different with the different programs, but all contact lists have similar capabilities.[citation needed]
Such lists may be used to form social networks with more specific purposes. The list is not the network: to become a network, a list requires some additional information such as the status or category of the contact.[citation needed] Given this, contact networks for various purposes can be generated from the list. Salespeople have long maintained contact networks using a variety of means of contact including phone logs and notebooks.[citation needed] They do not confuse their list with their network, nor would they confuse a "sales contact" with a "friend" or person they had already worked with.[citation needed]
See also
[edit]References
[edit]- ^ a b c Margaret, Rouse (8 December 2016). "What is a Contact List? - Definition from Techopedia". Techopedia. Retrieved 8 December 2023.
- ^ "contact list - English definition, grammar, pronunciation, synonyms and examples | Glosbe". glosbe.com. Retrieved 2023-12-08.
