Recent from talks
Contribute something
Nothing was collected or created yet.
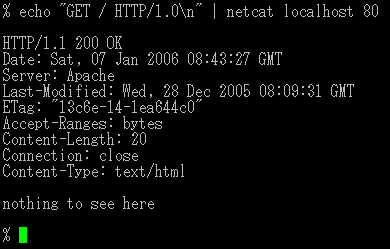
Netcat
View on Wikipedia| netcat | |
|---|---|
 The netcat command | |
| Original author | *Hobbit* |
| Developer | Avian Research |
| Initial release | October 28, 1995[1] |
| Final release | 1.10
/ March 1996 |
| Operating system | Unix and Unix-like, DOS, Microsoft Windows, Windows CE |
| Type | Network utility |
| License | Original version: custom, permissive license GNU version: GPL OpenBSD version: BSD |
| Website | nc110 |
netcat (often abbreviated to nc) is a computer networking utility for reading from and writing to network connections using TCP or UDP. The command is designed to be a dependable back-end that can be used directly or easily driven by other programs and scripts. At the same time, it is a feature-rich network debugging and investigation tool, since it can produce almost any kind of connection its user could need and has a number of built-in capabilities.
It is able to perform port scanning, file transferring and port listening.
Features
[edit]The original netcat's features include:[2]
- Outbound or inbound connections, TCP or UDP, to or from any ports
- Full DNS forward/reverse checking, with appropriate warnings
- Ability to use any local source port
- Ability to use any locally configured network source address
- Built-in port-scanning capabilities, with randomization
- Built-in loose source-routing capability
- Can read command line arguments from standard input
- Slow-send mode, one line every N seconds
- Hex dump of transmitted and received data
- Optional ability to let another program service establish connections
- Optional telnet-options responder
Rewrites like GNU's and OpenBSD's support additional features. For example, OpenBSD's nc supports TLS, and GNU netcat natively supports a tunneling mode supporting UDP and TCP (optionally allowing one to be tunneled over the other) in a single command,[3] where other versions may require piping data from one netcat instance to another.
Ports and reimplementations
[edit]The original version of netcat was a Unix program. The last version (1.10) was released in March 1996.[4]
There are several implementations on POSIX systems, including rewrites from scratch like GNU netcat[5] or OpenBSD netcat,[6] the latter of which supports IPv6 and TLS. The OpenBSD version has been ported to the FreeBSD base,[7] Windows/Cygwin,[8] and Linux.[9] Mac OS X comes with netcat installed as of OSX 10.13 or users can use MacPorts to install a variant.[10]
A DOS version of netcat called NTOOL is included in the FreeDOS Package group Networking.[11] It is based on the WatTCP stack and licensed under the European Union Public Licence Version 1.1.[12]
Known ports for embedded systems includes versions for Windows CE (named "Netcat 4 wince"[13]) or for the iPhone.[14]
BusyBox includes by default a lightweight version of netcat named mini-netcat.[15] Another version with more features, named bloaty nc, is also available.[16]
Solaris 11 includes netcat implementation based on OpenBSD netcat.[17]
Socat[18] is a more complex variant of netcat. It is larger and more flexible and has more options that must be configured for a given task. On February 1, 2016, Santiago Zanella-Beguelin and Microsoft Vulnerability Research issued a security advisory regarding a composite Diffie-Hellman parameter which had been hard-coded into the OpenSSL implementation of socat.[19] The implausibility that a composite might have been unintentionally introduced where a prime number is required has led to the suspicion of sabotage to introduce a backdoor software vulnerability.[20] This socat bug affected version 1.7.3.0 and 2.0.0-b8 it was corrected in following releases from 1.7.3.1 and 2.0.0-b9.[19]
Cryptcat[21] is a version of netcat with integrated transport encryption capabilities.
In the middle of 2005, Nmap announced another netcat incarnation called Ncat.[22] It features new possibilities such as "Connection Brokering", TCP/UDP Redirection, SOCKS4 client and server support, ability to "Chain" Ncat processes, HTTP CONNECT proxying (and proxy chaining), SSL connect/listen support and IP address/connection filtering. Like Nmap, Ncat is cross-platform.
On some systems, modified versions or similar netcat utilities go by the command name(s) nc, ncat, pnetcat, socat, sock, socket, sbd.
ncat
[edit]Ncat is a similar tool to netcat provided by Nmap suite.[22] "While Ncat isn't built on any code from the “traditional” Netcat (or any other implementation), Ncat is most definitely based on Netcat in spirit and functionality."[23]
Ncat features includes: ability to chain Ncats together, redirect both TCP and UDP ports to other sites, SSL support, and proxy connections via SOCKS4 or HTTP (CONNECT method) proxies (with optional proxy authentication as well).[24]
See also
[edit]- List of Unix commands
- cat (Unix) – Shell command for writing an input file or stream to standard output
- Nmap
- OpenSSL
- Telnet
- Plink
- Packet Sender
- Banner grabbing
References
[edit]- ^ Hobbit (1995-10-28). "New tool available: Netcat". Bugtraq mailing list. Retrieved 2019-06-05.
- ^ Vacca, John R. (2006). Guide to Wireless Network Security. Springer Publishing. p. 266. ISBN 978-0387954257.
- ^ Giovanni Giacobbi (2006-11-01). "The GNU Netcat project". Retrieved 2020-03-22.
- ^ "Netcat 1.10". nc110.sourceforge.net. 2008-02-14. Retrieved 2019-06-05.
- ^ Giovanni Giacobbi (2006-11-01). "The GNU Netcat project". Retrieved 2019-06-05.
- ^ "OpenBSD CVSWeb: /src/usr.bin/nc/". OpenBSD. Retrieved 2019-06-05.
- ^ delphij (2005-02-06). "Contents of /release/5.4.0/usr.bin/nc/Makefile". FreeBSD. Retrieved 2019-06-05.
- ^ Thomas Linden (2011-03-02). "Netcat OpenBSD Cygwin Port 1.10.2.3". Daemon.de. Retrieved 2019-06-05.
- ^ Debian netcat-openbsd
- ^ "MacPorts Portfiles: netcat". MacPorts. Retrieved 2019-06-05.
- ^ "ibiblio.org FreeDOS Group -- Networking". ibiblio. 2019-03-03. Retrieved 2019-06-05.
- ^ Jürgen Hoffmann (2018-11-03). "various tools". Retrieved 2019-06-05.
- ^ Andreas Bischoff (2010-06-07). "Netcat 4 wince". Retrieved 2019-06-05.
- ^ "Revision 835: /trunk/data/netcat". 2008-08-18. Retrieved 2019-06-05.
- ^ "nc: mini-netcat - built from the ground up for LRP". git.busybox.net.
- ^ "busybox - bloaty nc". git.busybox.net.
- ^ "Oracle Solaris 11.2 Information Library - Performing TCP and UDP Administration With the netcat Utility". docs.oracle.com.
- ^ "socat - Multipurpose relay". 2019-04-06. Retrieved 2019-06-05.
- ^ a b "Socat security advisory 7". 2016-02-01. Retrieved 2019-06-05.
- ^ Chirgwin, Richard (2016-02-03). "Socat slams backdoor, sparks thrilling whodunit". The Register. Retrieved 2019-06-05.
- ^ "CryptCat Project". 2005-10-18. Retrieved 2019-06-05.
- ^ a b "Ncat - Netcat for the 21st Century". Nmap. 2009-07-08. Retrieved 2019-06-05.
- ^ "ncat(1) - Ncat Reference Guide". manpages.debian.org. 2016-12-18. Retrieved 2019-06-05.
- ^ "Ncat - Netcat for the 21st Century".
External links
[edit]- Official website
- – Linux User Commands Manual
[[Program network station program 4.2
Netcat
View on GrokipediaHistory
Origins and Development
Netcat was invented in 1995 by Hobbit, a pseudonymous developer associated with the email address [email protected], as a straightforward Unix utility designed to read and write data across TCP and UDP network connections without imposing specific protocol assumptions.[9][1] The tool emerged from the need for a lightweight, versatile backend for network debugging, exploration, and scripting, filling a gap left by more rigid utilities like telnet, which lacked flexibility for arbitrary data stream handling.[1][10] Hobbit drew inspiration from earlier security and scanning tools such as SATAN and pscan, aiming to create a reliable program that could serve as a foundational component for other scripts while offering built-in capabilities for direct use in network tasks.[1] Developed in the C programming language specifically for Unix-like systems, netcat was crafted in an era when networking tools were proliferating within the hacker and security communities, emphasizing simplicity and portability across Unix variants.[1][10] The initial implementation focused on core functionality for establishing inbound or outbound connections, with an emphasis on minimal dependencies to ensure broad usability on contemporary Unix platforms like SunOS and BSD derivatives.[1] Early testing and refinements addressed common issues in network programming, such as handling half-closed connections and proxy behaviors, reflecting the practical challenges of 1990s Internet infrastructure.[1] Key milestones in netcat's early history include its release as version 1.00, announced on October 28, 1995, via the Bugtraq mailing list to the broader security and Unix user communities, marking its entry into public circulation.[9][1] Subsequent updates, culminating in version 1.10 by early 1996, incorporated portability enhancements and bug fixes based on user reports, solidifying its role as an essential utility in the evolving landscape of open-source networking tools.[1][10]Release and Early Adoption
Netcat's initial public release occurred on October 28, 1995, as version 1.00, authored by Hobbit under the auspices of Avian Research.[9] This version was distributed freely in full source form via the Avian Research FTP site at avian.org, with mirrors on sites such as zippy.telcom.arizona.edu and ftp.sterling.com, and no explicit restrictions beyond crediting the author.[9] The tool was positioned as a versatile utility for reading and writing data across TCP or UDP connections, suitable for network exploration and debugging.[9] A subsequent update, version 1.10, was released on March 20, 1996, incorporating bug fixes such as improved handling of stdin buffering and raw read operations to prevent data loss in piped inputs, along with minor enhancements for reliability in various network scenarios. Distribution continued through the same channels, with the source code archived and shared within Unix and early open-source communities via FTP and mailing lists like Bugtraq.[9] By the late 1990s, netcat had been integrated into several Linux distributions as a standard networking package for system administrators.[9] Early adoption centered on its utility in security auditing—such as testing firewall rules and port accessibility—network debugging for diagnosing connectivity issues, and scripting for automated data transfers in Unix environments.[9] Its popularity surged in open-source circles due to the straightforward command-line interface and broad applicability, despite the absence of a formal license initially.[10] The original implementation was released in the public domain, enabling unrestricted use and modification, which accelerated its spread but also prompted the creation of licensed forks.[9] This licensing status was later explicitly clarified as public domain by the author, yet it influenced the development of GPL- and BSD-licensed variants, such as GNU netcat, to comply with redistribution policies in corporate and distribution environments wary of unlicensed code.[11]Technical Overview
Protocol and Connection Support
Netcat primarily interacts with two core network protocols: TCP, which provides reliable, connection-oriented streams for ordered and error-checked data delivery, and UDP, which enables connectionless datagram transmission without guarantees of delivery or order.[1] These protocols allow netcat to function as a versatile backend for reading and writing data across network connections, with TCP as the default for most operations.[1] The tool operates in two main connection modes to establish network interactions. In client mode, netcat initiates outbound connections by directly specifying the remote host and port, facilitating data transfer to a listening endpoint.[1] Conversely, server mode involves binding to a local port using the-l option to listen for and accept incoming connections from remote clients.[1] Protocol selection between TCP and UDP is controlled via dedicated command-line options, such as -u for UDP mode.[1]
Regarding address families, the original netcat implementation defaults to IPv4 support, handling numeric IP addresses and hostname resolution without native IPv6 capabilities.[1] IPv6 was introduced in subsequent variants, including the OpenBSD rewrite, which explicitly added dual-stack compatibility for both address families.[12]
Netcat's data handling model treats network sockets as file-like bidirectional I/O streams, seamlessly integrating with Unix pipes and redirection. It reads input from standard input (stdin) and forwards it over the network connection, while simultaneously relaying any received network data to standard output (stdout), enabling efficient data shoveling in both directions until the connection closes.[1] This approach allows network traffic to be processed as ordinary streams, supporting tasks like echoing data or tunneling without additional protocol overhead.[1]
Command-Line Syntax and Options
The basic command-line syntax for netcat isnc [options] [host] [port], where host specifies the target hostname or IP address and port indicates the destination port number or range; omitting host and port places netcat in listening mode when combined with appropriate options.[1] This structure allows netcat to function as either a client connecting to a remote endpoint or a server awaiting inbound connections, with options preceding the host and port arguments to customize protocol, timing, and behavior.[1] For example, nc example.com 80 establishes a TCP connection to port 80 on the specified host, piping standard input to the remote side and relaying network data to standard output until the connection closes.[1]
Key options modify core operations, such as -l to enable listening mode for incoming connections (often paired with -p port to bind to a specific local port), -u to switch from the default TCP to UDP protocol, -v for verbose mode that outputs diagnostic messages about connection progress, and -p source_port to specify the local source port for outgoing connections.[1] Additional essential flags include -s source_IP to bind the connection to a particular local IP address, -w timeout_seconds to set a timeout for connection establishment or inactivity (defaulting to no timeout), -e program to execute a specified program upon successful connection (available in the original implementation when compiled with the GAPING_SECURITY_HOLE option), and -z for zero-I/O scanning mode, which probes ports without sending data to detect listening services.[1]
By default, netcat operates with bidirectional input/output, reading from standard input (up to 8 KB chunks) and writing to standard output while mirroring network traffic in the reverse direction, without performing end-of-line conversions for broad compatibility.[1] Options for controlling flow include -i interval_seconds, which introduces delays between transmitted lines to regulate data rates, and in certain implementations like OpenBSD's port, -k to keep the listener active for multiple sequential connections after the initial one closes (incompatible with single-use modes).[1][12]
Netcat handles errors by exiting with a nonzero status code for failures such as denied connections or timeouts. Refused connections are generally treated as non-fatal, except when attempting a single TCP connection to one port, in which case it exits with a nonzero status.[1] The original implementation adheres to POSIX standards through the use of raw read() and write() system calls for I/O operations, ensuring portability across Unix-like systems without relying on non-blocking modes or advanced buffering.[1]
Features and Capabilities
Core Networking Functions
Netcat's core networking functions enable straightforward data transfer and connection management over TCP and UDP, making it a fundamental tool for network communication without relying on higher-level protocols. At its essence, netcat reads from standard input and writes to standard output across network sockets, allowing bidirectional data streams between endpoints. This simplicity supports tasks like file transmission, where one host connects to another to push or pull data reliably.[1] Data transfer is achieved by directing file contents through netcat commands, with the sender piping input to a remote connection and the receiver capturing output to a file. For instance, to send a file, the commandnc host port < filename streams the file's contents to the specified host and port, while the receiving end uses nc -l -p port > filename to listen and save the incoming data. Transfers operate as raw streams, closing upon EOF, and can be resumed after interruption by combining netcat with the dd utility to skip known byte offsets on the sender (e.g., dd if=filename bs=1 skip=offset | nc host port) and append to the partial file on the receiver, requiring manual tracking of transferred bytes for alignment.[13][14]
Port listening and forwarding allow netcat to bind to local ports for incoming connections, enabling scenarios like reverse shells or basic proxies. In listening mode, nc -l -p port awaits a client connection and relays data bidirectionally; for a reverse shell, variants supporting the -e option execute a program upon connection, such as nc -l -p port -e /bin/sh, providing remote command execution over the established socket. Simple port forwarding can route traffic through proxies, as in nc -x proxyhost:proxyport host port using SOCKS or HTTP methods, though availability depends on the implementation.[13][12]
Banner grabbing involves initiating a connection to a remote service and capturing its initial response, aiding in service identification without full interaction. The command nc -v host port connects verbosely, displaying the server's greeting banner before closing, often combined with timeouts like -w 3 for efficiency across multiple ports (e.g., nc -v -w 3 host 20-30). This function leverages netcat's connection-handling to probe services minimally.[1]
Netcat integrates seamlessly with Unix pipes, enhancing its utility for composite tasks like remote archiving. For example, to perform a network backup, the sender executes tar cf - /directory | nc host 1234, streaming the tar archive over the connection, while the receiver runs nc -l -p 1234 | tar xf - to extract it directly. This piping model supports compression or other preprocessing (e.g., via gzip), treating netcat as a transport layer for arbitrary data flows.[12]
Diagnostic and Utility Extensions
Netcat provides several built-in options for network diagnostics, enabling users to perform tasks such as port scanning and traffic analysis without requiring additional software. One key feature is the zero-I/O mode, activated by the-z flag, which allows netcat to scan for open ports on a target host by attempting connections without sending any data, thereby minimizing network disturbance.[12] For instance, the command nc -z host 1-1024 probes ports 1 through 1024 on the specified host, reporting only those that are listening, and can be combined with -v for verbose output including connection timings.[13] This mode supports both TCP and UDP protocols when used with the -u option and is particularly useful for initial reconnaissance in network troubleshooting.[15]
In certain implementations, such as netcat-traditional, the -o option enables hexadecimal dumping of network traffic to a file, facilitating detailed protocol analysis by capturing raw byte-level data exchanged during sessions.[15] For example, nc -o traffic.hex [example.com](/page/Example.com) 80 would connect to port 80 and log the hex representation of all incoming and outgoing packets to traffic.hex, aiding in debugging malformed packets or custom protocol inspections.[16] This feature is absent in some streamlined versions like OpenBSD's nc, where users may need external tools for similar functionality.[12]
Netcat also handles telnet protocol negotiation through the -t option, which automatically responds to RFC 854 DO and WILL requests with DON'T and WON'T messages, allowing seamless scripting of interactive telnet sessions without manual intervention.[12] Complementing this, the -n flag suppresses DNS resolution, forcing netcat to use numeric IP addresses directly and bypassing hostname lookups to reduce overhead and potential resolution delays in diagnostic runs.[13] For example, nc -t -n 192.168.1.1 23 establishes a telnet connection to the specified IP while handling negotiation and avoiding DNS queries.[15]
For basic tunneling, netcat supports simple port forwarding by chaining instances to relay traffic between interfaces, creating lightweight proxies without dedicated software.[17] A common setup involves one netcat process listening on a local port and piping output to another connecting to the remote target, such as nc -l -p 8080 | nc remotehost 80 on the relay machine, which forwards incoming connections from port 8080 to the remote port 80.[18] This approach leverages netcat's core connection capabilities to build ad-hoc tunnels for testing or bypassing restrictions.[15]
Implementations
Original Unix Implementation
The original Unix implementation of netcat, developed by the anonymous programmer known as Hobbit of Avian Research, was written in ANSI C as a single source file namednetcat.c, comprising approximately 1,850 lines of code. This compact codebase was designed for simplicity and portability, allowing it to function as a versatile backend tool for network data transfer on Unix-like systems.[19]
Compilation requires a POSIX-compliant environment and standard Unix tools such as gcc or equivalent C compilers, with no external dependencies beyond core system libraries like <sys/socket.h>, <netinet/in.h>, and <unistd.h>. The build process typically involves a simple make command, optionally with preprocessor defines (e.g., -DGAPING_SECURITY_HOLE to enable the -e option for program execution) passed via flags, ensuring broad compatibility across Unix variants without additional configuration.[1]
Key limitations of this implementation include exclusive support for IPv4 addresses, absence of any built-in encryption mechanisms, single-threaded operation relying on blocking I/O and the select() system call for handling connections, and fixed buffer sizes of 8 KB for input/output operations to manage data streams efficiently. These constraints reflect the tool's focus on core functionality rather than advanced features, prioritizing reliability in basic TCP and UDP networking tasks.[1]
The source code for version 1.10, the final official release, remains publicly available and archived at SourceForge under the project nc110, with the last update occurring in March 1996. This preservation ensures ongoing access for study and historical reference, underscoring netcat's enduring influence as a foundational networking utility.[19]
Platform Ports and Variants
Netcat has been adapted to various non-Unix platforms through ports that leverage platform-specific APIs, such as the Winsock interface on Windows for handling TCP/IP connections. Early Windows ports emerged in the late 1990s, with Weld Pond releasing a Netcat version for Windows NT in 1998, compiled for Win32 to support networking tasks on Microsoft systems.[10] These ports translated the original Unix socket programming to Winsock, enabling similar functionality like port scanning and data transfer on Windows environments. Later adaptations, such as Nmap's ncat introduced in 2009, built upon these by incorporating IPv6 and SSL support while maintaining compatibility with the Winsock API. Ports for legacy systems like MS-DOS were developed using compilers such as Open Watcom to create minimal implementations suitable for resource-constrained environments. The mTCP suite, updated in 2010, includes a Netcat component ported to DOS with Open Watcom 1.8, allowing TCP/IP operations on real-mode systems without requiring protected mode extensions.[20] For embedded networking devices, third-party adaptations like IOScat provide Netcat-like TCP functions directly in Cisco IOS, implemented as a scriptable text file to facilitate penetration testing and data relay on routers without native support for external binaries.[21] On BSD-derived systems, Netcat is integrated into base installations, with FreeBSD including it since early versions and adding IPv6 support around 2000 as part of broader protocol enhancements in FreeBSD 4.0. The FreeBSD nc utility supports IPv6 connections natively, enabling commands likenc -6 for address family specification. Similarly, macOS includes a built-in nc from the OpenBSD codebase in its base system, while Homebrew offers an additional netcat formula for users seeking the classic version with options like -e for program execution.[22]
Minor variants extend Netcat's core with targeted modifications, such as Cryptcat, released around 2001, which adds Twofish encryption to secure data streams over TCP or UDP connections using a shared password as the key.[23] For mobile and embedded platforms, basic forks like those in Termux on Android provide OpenBSD-derived Netcat via package managers, supporting lightweight networking tasks such as port listening without root access. These adaptations preserve Netcat's simplicity while accommodating platform constraints like limited memory or non-standard APIs.
Notable Reimplementations
GNU netcat is a reimplementation of the original netcat utility developed as part of the GNU project to ensure portability and compatibility across various Unix-like systems.[11] It adds support for the -e option to execute programs upon connection, improved error handling for more robust operation, and is included by default in many Linux distributions such as Debian and Fedora.[24] The OpenBSD netcat represents a significant rewrite integrated into the OpenBSD operating system starting in 2001, with version 1.89 appearing in OpenBSD 3.5.[12] This version introduces native IPv6 support, compatibility with Unix domain sockets and proxies, and tight integration with the PF packet filter for enhanced firewall capabilities.[25] For security reasons, it deliberately omits the -e option to prevent its use in creating unauthorized backdoors.[12] Ncat, developed by the Nmap Project, was released in 2009 as a modern reimplementation of netcat, emphasizing backward compatibility with the original syntax while extending functionality for contemporary networks.[6] Key additions include built-in SSL/TLS encryption via the --ssl option, support for Lua scripting to enable custom behaviors like advanced proxying and data transformation, and full IPv6 compatibility.[6] It is distributed as part of the Nmap security scanner suite and supports cross-platform use on Linux, Windows, and macOS.[26] Socat, authored by Gerhard Rieger and first released in 2001, serves as a more versatile superset of netcat rather than a direct clone, focusing on bidirectional data relay across diverse address types.[27] It handles not only TCP and UDP but also Unix sockets, SSL, and raw IP protocols, with features like address option chaining for complex relaying scenarios that netcat cannot achieve natively.[28] Often recommended as an advanced alternative, socat is widely used in scripting and automation for its flexibility in protocol bridging and encryption support.[29]Security Considerations
Known Vulnerabilities
The-e option in traditional netcat implementations enables the execution of arbitrary commands upon establishing a connection, facilitating remote code execution if the tool is misconfigured or exposed on a network, such as in bind shell attacks where incoming connections trigger shell access. This feature has been widely recognized as a security risk, allowing attackers to create persistent backdoors with minimal effort.
Early versions of netcat, including the Windows port 1.1, contained a stack-based buffer overflow in the doexec.c function when using the -e option, enabling remote attackers to execute arbitrary code via long command-line arguments; this was documented as CVE-2004-1317.[30] Debian maintainers applied patches to address potential buffer overflows in input handling for netcat version 1.10, closing related bug reports. In variants like socat, a heap-based buffer overflow existed in the xioscan_readline function of xio-readline.c (versions 1.4.0.0 through 1.7.2.0 and 2.0.0-b1 through 2.0.0-b4), allowing local denial-of-service or potential code execution when invoked with the READLINE address without the 'prompt' option; this was assigned CVE-2012-0219 and patched in later releases.[31]
Netcat's UDP mode lacks inherent rate limiting, making it susceptible to denial-of-service attacks if used to relay or listen for traffic, as it can consume resources without bounds on incoming packets. The OpenBSD reimplementation omitted the -e option for command execution to reduce the risk of inadvertent backdoor creation, prioritizing security in its base system utility.[32]
Best Practices and Alternatives
When using netcat, it is advisable to avoid the-e option on untrusted networks, as it enables program execution upon connection, potentially allowing unauthorized access if exploited.[33] Instead, integrate netcat with firewalls such as iptables to restrict access to specific ports and IP addresses, ensuring that listening modes are only exposed to authorized sources.[34] For instance, an iptables rule can limit incoming connections to a designated subnet, mitigating risks from external probes.[35]
For protocol selection, prefer UDP with netcat for broadcast scenarios where speed is prioritized over guaranteed delivery, such as network discovery tasks, but opt for TCP when reliability is essential, as it ensures ordered and error-checked data transmission.[34] Secure configurations include combining netcat with SSH tunneling to encrypt traffic; a common setup pipes netcat output through SSH for forwarding, as seen in rsync operations where nc relays data via an SSH proxy to the target host.[36] Additionally, employ the -w timeout option to prevent indefinite hangs during stalled connections, specifying a duration in seconds to automatically close idle sessions.[37]
In modern deployments, plain netcat should be used with caution in production environments due to its lack of built-in encryption and authentication; consider isolated execution within containers or under SELinux policies for enhanced confinement. As secure alternatives, Ncat from the Nmap project extends netcat with TLS/SSL support for encrypted connections, using options like --ssl to secure data in transit without additional tools.[6] Socat provides advanced multiplexing capabilities, supporting complex stream handling and native SSL/TLS via address types like OPENSSL, making it suitable for bidirectional relays with authentication.[38] For file transfers, scp or rsync over SSH offer encrypted alternatives to netcat's unsecure piping, ensuring integrity and confidentiality through OpenSSH protocols.[36]