Recent from talks
Nothing was collected or created yet.
Total Information Awareness
View on Wikipedia

 National Security Agency surveillance |
|---|
 |
Total Information Awareness (TIA) was a mass detection program[clarification needed] by the United States Information Awareness Office. It operated under this title from February to May 2003 before being renamed Terrorism Information Awareness.[1][2]
Based on the concept of predictive policing, TIA was meant to correlate detailed information about people in order to anticipate and prevent terrorist incidents before execution.[3] The program modeled specific information sets in the hunt for terrorists around the globe.[4] Admiral John Poindexter called it a "Manhattan Project for counter-terrorism".[5] According to Senator Ron Wyden, TIA was the "biggest surveillance program in the history of the United States".[6]
Congress defunded the Information Awareness Office in late 2003 after media reports criticized the government for attempting to establish "Total Information Awareness" over all citizens.[7][8][9]
Although the program was formally suspended, other government agencies later adopted some of its software with only superficial changes. TIA's core architecture continued development under the code name "Basketball". According to a 2012 New York Times article, TIA's legacy was "quietly thriving" at the National Security Agency (NSA).[10]
Program synopsis
[edit]TIA was intended to be a five-year research project by the Defense Advanced Research Projects Agency (DARPA). The goal was to integrate components from previous and new government intelligence and surveillance programs, including Genoa, Genoa II, Genisys, SSNA, EELD, WAE, TIDES, Communicator, HumanID and Bio-Surveillance, with data mining knowledge gleaned from the private sector to create a resource for the intelligence, counterintelligence, and law enforcement communities.[11][12] These components consisted of information analysis, collaboration, decision-support tools, language translation, data-searching, pattern recognition, and privacy-protection technologies.[13]
TIA research included or planned to include the participation of nine government entities: INSCOM, NSA, DIA, CIA, CIFA, STRATCOM, SOCOM, JFCOM, and JWAC.[13] They were to be able to access TIA's programs through a series of dedicated nodes.[14] INSCOM was to house TIA's hardware in Fort Belvoir, Virginia.[15]
Companies contracted to work on TIA included the Science Applications International Corporation,[16] Booz Allen Hamilton, Lockheed Martin Corporation, Schafer Corporation, SRS Technologies, Adroit Systems, CACI Dynamic Systems, ASI Systems International, and Syntek Technologies.[17]
Universities enlisted to assist with research and development included Berkeley, Colorado State, Carnegie Mellon, Columbia, Cornell, Dallas, Georgia Tech, Maryland, MIT, and Southampton.[17][18]
Mission
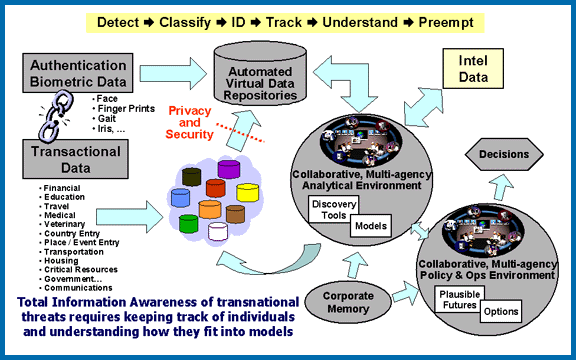
[edit]TIA's goal was to revolutionize the United States' ability to detect, classify and identify foreign terrorists and decipher their plans, thereby enabling the U.S. to take timely action to preempt and disrupt terrorist activity.
To that end, TIA was to create a counter-terrorism information system that:[19]
- Increased information coverage by an order of magnitude and afforded easy scaling
- Provided focused warnings within an hour after a triggering event occurred or an evidence threshold was passed
- Automatically queued analysts based on partial pattern matches and had patterns that covered 90% of all previously known foreign terrorist attacks
- Supported collaboration, analytical reasoning and information sharing so that analysts could hypothesize, test and propose theories and mitigating strategies, so decision-makers could effectively evaluate the impact of policies and courses of action.
Components
[edit]Genoa
[edit]Unlike the other program components, Genoa predated TIA and provided a basis for it.[20] Genoa's primary function was intelligence analysis to assist human analysts.[21] It was designed to support both top-down and bottom-up approaches; a policymaker could hypothesize an attack and use Genoa to look for supporting evidence of it or compile pieces of intelligence into a diagram and suggest possible outcomes. Human analysts could then modify the diagram to test various cases.[22]
Genoa was independently commissioned in 1996 and completed in 2002 as scheduled.
Genoa II
[edit]While Genoa primarily focused on intelligence analysis, Genoa II aimed to provide means by which computers, software agents, policymakers, and field operatives could collaborate.[21]
Genisys
[edit]
Genisys aimed to develop technologies that would enable "ultra-large, all-source information repositories".[23] Vast amounts of information were to be collected and analyzed, and the available database technology at the time was insufficient for storing and organizing such enormous quantities of data. So they developed techniques for virtual data aggregation to support effective analysis across heterogeneous databases, as well as unstructured public data sources, such as the World Wide Web. "Effective analysis across heterogenous databases" means the ability to take things from databases which are designed to store different types of data—such as a database containing criminal records, a phone call database and a foreign intelligence database. The Web is considered an "unstructured public data source" because it is publicly accessible and contains many different types of data—blogs, emails, records of visits to websites, etc.—all of which need to be analyzed and stored efficiently.[23]
Another goal was to develop "a large, distributed system architecture for managing the huge volume of raw data input, analysis results, and feedback, that will result in a simpler, more flexible data store that performs well and allows us to retain important data indefinitely".[23]
Scalable social network analysis
[edit]Scalable social network analysis (SSNA) aimed to develop techniques based on social network analysis to model the key characteristics of terrorist groups and discriminate them from other societal groups.[24]
Evidence extraction and link discovery
[edit]
Evidence extraction and link discovery (EELD) developed technologies and tools for automated discovery, extraction and linking of sparse evidence contained in large amounts of classified and unclassified data sources (such as phone call records from the NSA call database, internet histories, or bank records).[25]
EELD was designed to design systems with the ability to extract data from multiple sources (e.g., text messages, social networking sites, financial records, and web pages). It was to develop the ability to detect patterns comprising multiple types of links between data items or communications (e.g., financial transactions, communications, travel, etc.).[25] It is designed to link items relating potential "terrorist" groups and scenarios, and to learn patterns of different groups or scenarios to identify new organizations and emerging threats.[25]
Wargaming the asymmetric environment
[edit]Wargaming the asymmetric environment (WAE) focused on developing automated technology that could identify predictive indicators of terrorist activity or impending attacks by examining individual and group behavior in broad environmental context and the motivation of specific terrorists.[26]
Translingual information detection, extraction and summarization
[edit]Translingual information detection, extraction and summarization (TIDES) developed advanced language processing technology to enable English speakers to find and interpret critical information in multiple languages without requiring knowledge of those languages.[27]
Outside groups (such as universities, corporations, etc.) were invited to participate in the annual information retrieval, topic detection and tracking, automatic content extraction, and machine translation evaluations run by NIST.[27] Cornell University, Columbia University, and the University of California, Berkeley were given grants to work on TIDES.[17]
Communicator
[edit]
Communicator was to develop "dialogue interaction" technology to enable warfighters to talk to computers, such that information would be accessible on the battlefield or in command centers without a keyboard-based interface. Communicator was to be wireless, mobile, and to function in a networked environment.[28]
The dialogue interaction software was to interpret dialogue's context to improve performance, and to automatically adapt to new topics so conversation could be natural and efficient. Communicator emphasized task knowledge to compensate for natural language effects and noisy environments. Unlike automated translation of natural language speech, which is much more complex due to an essentially unlimited vocabulary and grammar, Communicator takes on task-specific issues so that there are constrained vocabularies (the system only needs to be able to understand language related to war). Research was also started on foreign-language computer interaction for use in coalition operations.[28]
Live exercises were conducted involving small unit logistics operations with the United States Marines to test the technology in extreme environments.[28]
Human identification at a distance
[edit]
The human identification at a distance (HumanID) project developed automated biometric identification technologies to detect, recognize and identify humans at great distances for "force protection", crime prevention, and "homeland security/defense" purposes.[29]
The goals of HumanID were to:[29]
- Develop algorithms to find and acquire subjects out to 150 meters (500 ft) in range.
- Fuse face and gait recognition into a 24/7 human identification system.
- Develop and demonstrate a human identification system that operates out to 150 meters (500 ft) using visible imagery.
- Develop a low-power millimeter wave radar system for wide field of view detection and narrow field of view gait classification.
- Characterize gait performance from video for human identification at a distance.
- Develop a multi-spectral infrared and visible face recognition system.
A number of universities assisted in designing HumanID. The Georgia Institute of Technology's College of Computing focused on gait recognition. Gait recognition was a key component of HumanID, because it could be employed on low-resolution video feeds and therefore help identify subjects at a distance.[30] They planned to develop a system that recovered static body and stride parameters of subjects as they walked, while also looking into the ability of time-normalized joint angle trajectories in the walking plane as a way of recognizing gait. The university also worked on finding and tracking faces by expressions and speech.[18]
Carnegie Mellon University's Robotics Institute (part of the School of Computer Science) worked on dynamic face recognition. The research focused primarily on the extraction of body biometric features from video and identifying subjects from those features. To conduct its studies, the university created databases of synchronized multi-camera video sequences of body motion, human faces under a wide range of imaging conditions, AU coded expression videos, and hyperspectal and polarimetric images of faces.[31] The video sequences of body motion data consisted of six separate viewpoints of 25 subjects walking on a treadmill. Four separate 11-second gaits were tested for each: slow walk, fast walk, inclined, and carrying a ball.[30]
The University of Maryland's Institute for Advanced Computer Studies' research focused on recognizing people at a distance by gait and face. Also to be used were infrared and five-degree-of-freedom cameras.[32] Tests included filming 38 male and 6 female subjects of different ethnicities and physical features walking along a T-shaped path from various angles.[33]
The University of Southampton's Department of Electronics and Computer Science was developing an "automatic gait recognition" system and was in charge of compiling a database to test it.[34] The University of Texas at Dallas was compiling a database to test facial systems. The data included a set of nine static pictures taken from different viewpoints, a video of each subject looking around a room, a video of the subject speaking, and one or more videos of the subject showing facial expressions.[35] Colorado State University developed multiple systems for identification via facial recognition.[36] Columbia University participated in implementing HumanID in poor weather.[31]
Bio-surveillance
[edit]
The bio-surveillance project was designed to predict and respond to bioterrorism by monitoring non-traditional data sources such as animal sentinels, behavioral indicators, and pre-diagnostic medical data. It would leverage existing disease models, identify abnormal health early indicators, and mine existing databases to determine the most valuable early indicators for abnormal health conditions.[37]
Scope of surveillance
[edit]As a "virtual, centralized, grand database",[38] the scope of surveillance included credit card purchases, magazine subscriptions, web browsing histories, phone records, academic grades, bank deposits, gambling histories, passport applications, airline and railway tickets, driver's licenses, gun licenses, toll records, judicial records, and divorce records.[8][12]
Health and biological information TIA collected included drug prescriptions,[8] medical records,[39] fingerprints, gait, face and iris data,[12] and DNA.[40]
Privacy
[edit]TIA's Genisys component, in addition to integrating and organizing separate databases, was to run an internal "privacy protection program". This was intended to restrict analysts' access to irrelevant information on private U.S. citizens, enforce privacy laws and policies, and report misuses of data.[41] There were also plans for TIA to have an application that could "anonymize" data, so that information could be linked to an individual only by court order (especially for medical records gathered by the bio-surveillance project).[37] A set of audit logs were to be kept, which would track whether innocent Americans' communications were getting caught up in relevant data.[10]
History
[edit]
The term total information awareness was first coined at the 1999 annual DARPAtech conference in a presentation by the deputy director of the Office of Information Systems Management, Brian Sharkey. Sharkey applied the phrase to a conceptual method by which the government could sift through massive amounts of data becoming available via digitization and draw important conclusions.[22]
Early developments
[edit]TIA was proposed as a program shortly after the September 11 attacks in 2001, by Rear Admiral John Poindexter.[42] A former national security adviser to President Ronald Reagan and a key player in the Iran–Contra affair, he was working with Syntek Technologies, a company often contracted out by the government for work on defense projects. TIA was officially commissioned during the 2002 fiscal year.[17] In January 2002 Poindexter was appointed Director of the newly created Information Awareness Office division of DARPA, which managed TIA's development.[43] The office temporarily operated out of the fourth floor of DARPA's headquarters, while Poindexter looked for a place to permanently house TIA's researchers.[15] Soon Project Genoa was completed and its research moved on to Genoa II.[44][45]
Late that year, the Information Awareness Office awarded the Science Applications International Corporation (SAIC) a $19 million contract to develop the "Information Awareness Prototype System", the core architecture to integrate all of TIA's information extraction, analysis, and dissemination tools. This was done through its consulting arm, Hicks & Associates, which employed many former Defense Department and military officials.[16]
TIA's earliest version employed software called "Groove", which had been developed in 2000 by Ray Ozzie. Groove made it possible for analysts from many different agencies to share intelligence data instantly, and linked specialized programs that were designed to look for patterns of suspicious behavior.[46]
Congressional restrictions and termination
[edit]On 24 January 2003, the United States Senate voted to limit TIA by restricting its ability to gather information from emails and the commercial databases of health, financial and travel companies.[47] According to the Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, § 111(b) passed in February, the Defense Department was given 90 days to compile a report laying out a schedule of TIA's development and the intended use of allotted funds or face a cutoff of support.[48]
The report arrived on May 20. It disclosed that the program's computer tools were still in their preliminary testing phase. Concerning the pattern recognition of transaction information, only synthetic data created by researchers was being processed. The report also conceded that a full prototype of TIA would not be ready until the 2007 fiscal year.[13] Also in May, Total Information Awareness was renamed Terrorism Information Awareness in an attempt to stem the flow of criticism on its information-gathering practices on average citizens.[49]
At some point in early 2003, the National Security Agency began installing access nodes on TIA's classified network.[5] The NSA then started running stacks of emails and intercepted communications through TIA's various programs.[14]
Following a scandal in the Department of Defense involving a proposal to reward investors who predicted terrorist attacks, Poindexter resigned from office on 29 August.[14]
On September 30, 2003, Congress officially cut off TIA's funding and the Information Awareness Office (with the Senate voting unanimously against it)[50] because of its unpopular perception by the general public and the media.[9][51] Senators Ron Wyden and Byron Dorgan led the effort.[52]
After 2003
[edit]Reports began to emerge in February 2006 that TIA's components had been transferred to the authority of the NSA. In the Department of Defense appropriations bill for the 2004 fiscal year, a classified annex provided the funding. It was stipulated that the technologies were limited for military or foreign intelligence purposes against non-U.S. citizens.[53] Most of the original project goals and research findings were preserved, but the privacy protection mechanics were abandoned.[5][10]
Topsail
[edit]Genoa II, which focused on collaboration between machines and humans, was renamed "Topsail" and handed over to the NSA's Advanced Research and Development Activity, or ARDA (ARDA was later moved to the Director of National Intelligence's control as the Disruptive Technologies Office). Tools from the program were used in the war in Afghanistan and other parts of the War on Terror.[16] In October 2005, the SAIC signed a $3.7 million contract for work on Topsail.[22] In early 2006 a spokesman for the Air Force Research Laboratory said that Topsail was "in the process of being canceled due to lack of funds". When asked about Topsail in a Senate Intelligence Committee hearing that February, both National Intelligence Director John Negroponte and FBI Director Robert Mueller said they did not know the program's status. Negroponte's deputy, former NSA director, Michael V. Hayden, said, "I'd like to answer in closed session."[16]
Basketball
[edit]The Information Awareness Prototype System was reclassified as "Basketball" and work on it continued by SAIC, supervised by ARDA. As late as September 2004, Basketball was fully funded by the government and being tested in a research center jointly run by ARDA and SAIC.[16]
Criticism
[edit]Critics allege that the program could be abused by government authorities as part of their practice of mass surveillance in the United States. In an op-ed for The New York Times, William Safire called it "the supersnoop's dream: a Total Information Awareness about every U.S. citizen".[8]
Hans Mark, a former director of defense research and engineering at the University of Texas, called it a "dishonest misuse of DARPA".[1]
The American Civil Liberties Union launched a campaign to terminate TIA's implementation, claiming that it would "kill privacy in America" because "every aspect of our lives would be catalogued".[54] The San Francisco Chronicle criticized the program for "Fighting terror by terrifying U.S. citizens".[55]
Still, in 2013 former Director of National Intelligence James Clapper lied about a massive data collection on US citizens and others.[56] Edward Snowden said that because of Clapper's lie he lost hope to change things formally.[56]
In popular culture
[edit]In the 2008 British television series The Last Enemy, TIA is portrayed as a UK-based surveillance database that can be used to track and monitor anybody by putting all available government information in one place.
See also
[edit]References
[edit]- ^ a b Weinberger, Sharon (24 January 2008). "Defence research: Still in the lead?". Nature. 451 (7177). Nature Publishing Group: 390–393. Bibcode:2008Natur.451..390W. doi:10.1038/451390a. PMID 18216826.
Poindexter and his office proved to be more polarizing than expected; its Total Information Awareness programme (later changed to Terrorism Information Awareness), which aimed to sift through huge amounts of data to track terrorists, was attacked on privacy grounds, and Congress eventually cancelled it. "That was a dishonest misuse of DARPA," says Hans Mark, a former director of defense research and engineering now at the University of Texas at Austin.
- ^ Ryan Singel (14 June 2003). "Funding for TIA All But Dead". Wired. Retrieved 7 December 2013.
- ^ Murray, N. (4 October 2010). "Profiling in the age of total information awareness". Race & Class. 52 (2): 3–24. doi:10.1177/0306396810377002. S2CID 144001217.
- ^ MARKOFF, JOHN (November 9, 2002). "Pentagon Plans a Computer System That Would Peek at Personal Data of Americans". The New York Times. Retrieved 19 December 2013.
- ^ a b c Shorrock, Tim (2008). Spies for Hire: The Secret World of Intelligence Outsourcing. Simon and Schuster. pp. 221. ISBN 9780743282246.
- ^ "Pentagon's 'Terror Information Awareness' program will end". USA Today. AP. 2003-09-25. Retrieved 19 December 2013.
- ^ Jonathan Turley (November 17, 2002). "George Bush's Big Brother". The Los Angeles Times. Retrieved 19 December 2013.
- ^ a b c d WILLIAM SAFIRE (November 14, 2002). "You Are a Suspect". The New York Times. Retrieved September 20, 2013.
- ^ a b "U.S. agencies collect, examine personal data on Americans". The Washington Times. May 28, 2004. Retrieved 19 December 2013.
The most widely reported data-mining project—the Pentagon's Total Information Awareness (TIA) program—was shut down by Congress because of widespread privacy fears. The project sought to use credit-card, medical and travel records to search for terrorists and was dubbed by privacy advocates as a "supersnoop" system to spy on Americans.
- ^ a b c SHANE HARRIS (August 22, 2012). "Giving In to the Surveillance State". The New York Times. Retrieved 19 December 2013.
- ^ Poindexter, John (2 August 2002). "OVERVIEW OF THE INFORMATION AWARENESS OFFICE". fas.org. Federation of American Scientists. Retrieved 3 June 2016.
- ^ a b c Stevens, Gina Marie (2003). Privacy: Total Information Awareness Programs and Latest Developments (illustrated ed.). Nova Publishers. ISBN 9781590338698.
- ^ a b c "Report to Congress Regarding the Terrorism Information Awareness Program: In response to Consolidated Appropriations Resolution, 2003, Pub. L. No. 108-7, Division M, § 111(b)" (PDF). www.epic.org. DARPA. 20 May 2003. Retrieved 7 June 2016.
- ^ a b c Bamford, James (14 October 2008). The Shadow Factory: The Ultra-Secret NSA from 9/11 to the Eavesdropping on America. Knopf Doubleday Publishing Group. ISBN 9780385528399.
- ^ a b Jacobsen, Annie (2015). The Pentagon's Brain: An Uncensored History of DARPA, America's Top-Secret Military Research Agency (illustrated ed.). Little, Brown. ISBN 9780316371650.
- ^ a b c d e TIA Lives On, National Journal, 23 February 2006, retrieved 14 June 2016
- ^ a b c d Mayle, Adam; Knott, Alex (17 December 2002). "Outsourcing Big Brother: Office of Total Information Awareness relies on private sector to track Americans". www.publicintegrity.org. Center for Public Integrity. Retrieved 6 June 2016.
- ^ a b "Human Identification at a Distance". www.cc.gatech.edu. Georgia Institute of Technology College of Computing. 2003. Retrieved 16 June 2016.
- ^ "Total Information Awareness (TIA) System". DARPA. October 3, 2002. Archived from the original on October 3, 2002.
- ^ Balancing Privacy & Security: The Privacy Implications of Government Data Mining Programs: Congressional Hearing. DIANE Publishing. p. 126. ISBN 9781422320259.
- ^ a b Dan Verton (1 September 2003). "Genoa II: Man and Machine Thinking as One". Computerworld. IDG Enterprise. Retrieved 3 June 2016.
- ^ a b c Harris, Shane (18 February 2010). The Watchers: The Rise of America's Surveillance State (reprint ed.). Penguin. ISBN 9781101195741.
- ^ a b c "Genisys". Information Awareness Office (official website). Archived from the original on 2009-02-16. Retrieved 2009-03-15.
- ^ Ethier, Jason. "Current Research in Social Network Theory". Northeastern University College of Computer and Information Science. Archived from the original on February 26, 2015. Retrieved 2009-03-15.
- ^ a b c "Evidence Extraction and Link Discovery". Information Awareness Office (official website -- mirror). Archived from the original on 2009-02-15. Retrieved 2009-03-15.
- ^ "Wargaming the Asymmetric Environment (WAE)". www.darpa.mil/iao. Information Awareness Office. Archived from the original on 28 May 2012. Retrieved 16 June 2016.
- ^ a b "TIDES". Information Awareness Office (official website -- mirror). Archived from the original on 2009-02-15. Retrieved 2009-03-15.
- ^ a b c "Communicator". Information Awareness Office (official website). Archived from the original on 2009-02-15. Retrieved 2009-03-15.
- ^ a b c "Human Identification at a distance". Information Awareness Office (official website -- mirror). Archived from the original on February 15, 2009. Retrieved 2009-03-15.
- ^ a b Bolle, Ruud M.; Connell, Jonathan; Pankanti, Sharath; Ratha, Nalini K.; Senior, Andrew W. (29 June 2013). Guide to Biometrics (illustrated ed.). Springer Science & Business Media. p. 239. ISBN 9781475740363.
- ^ a b "Human Identification at a Distance (HumanID)". Carnegie Mellon University: The Robotics Institute. Carnegie Mellon University. Archived from the original on 9 August 2016. Retrieved 16 June 2016.
- ^ "Human Identification at a Distance: Overview". University of Maryland Institute for Advanced Computer Studies. University of Maryland. 17 April 2001. Retrieved 16 June 2016.
- ^ Bahram Javidi, ed. (28 June 2005). Optical and Digital Techniques for Information Security. Advanced Sciences and Technologies for Security Applications. Vol. 1 (illustrated ed.). Springer Science & Business Media. p. 283. ISBN 9780387206165.
- ^ Nixon, M.S. (7 August 2003). "Automatic Gait Recognition for Human ID at a Distance". www.ecs.soton.ac.uk. University of Southampton. Archived from the original on 2016-08-05. Retrieved 16 June 2016.
- ^ O'Toole, Alice. "Human Identification Project". www.utdallas.edu. University of Texas at Dallas. Retrieved 16 June 2016.
- ^ "Evaluation of Face Recognition Algorithms". www.cs.colostate.edu. Colorado State University. Retrieved 16 June 2016.
- ^ a b "Bio- Surveillance". www.darpa.mil/iao. Information Awareness Office. Archived from the original on 2006-09-19.
- ^ Anthony M. Townsend. "Your city is spying on you: From iPhones to cameras, you are being watched right now". Salon. Retrieved 19 December 2013.
- ^ Ron Wyden (January 15, 2003). "Wyden Calls For Congressional Oversight, Accountability of Total Information Awareness Office". United States Senate. Retrieved 19 December 2013.
On the Web site of this particular program, the Total Information Awareness Program, they cite a Latin slogan—"Knowledge is power"—something we would all agree with, and state: The total information awareness of transnational threats requires keeping track of individuals and understanding how they fit into models. To this end, this office would seek to develop a way to integrate databases into a "virtual centralized grand database". They would be in a position to look at education, travel, and medical records, and develop risk profiles for millions of Americans
- ^ Pat M. Holt (October 2, 2003). "Driving dangerously with the Patriot Act". Christian Science Monitor. Retrieved 19 December 2013.
The Defense Department is leading the charge for what it calls Total Information Awareness, a massive database including DNA.
- ^ Lee, Newton (7 April 2015). Counterterrorism and Cybersecurity: Total Information Awareness (2, illustrated, revised ed.). Springer. p. 141. ISBN 9783319172446.
- ^ Rosen, Jeffrey (2002-12-15). "The Year in Ideas; Total Information Awareness". The New York Times. ISSN 0362-4331. Retrieved 2021-04-03.
- ^ Belasco, Amy (21 March 2003). "Total Information Awareness Programs: Funding, Composition, and Oversight Issues" (PDF). www.au.af.mil/au. Congressional Research Service. Archived from the original (PDF) on June 27, 2004. Retrieved 7 June 2016.
- ^ Armour, Tom (2002). "Genoa II DARPAtech 2002 Presentation Script" (PDF). w2.eff.org. Electronic Frontier Foundation. Archived from the original (PDF) on 2016-10-08. Retrieved 20 June 2016.
- ^ "Genoa". www.darpa.mil/iao. Information Awareness Office. Archived from the original on 2009-02-16.
- ^ "TECHNOLOGY; Many Tools Of Big Brother Are Now Up And Running". The New York Times. December 23, 2002. Retrieved 7 December 2013.
- ^ ADAM CLYMER (January 24, 2003). "Senate Rejects Privacy Project". The New York Times. Retrieved 7 December 2013.
- ^ "Joint Resolution". www.gpo.gov. United States Government Publishing Office. February 2003. Retrieved 7 June 2016.
- ^ Richelson, Jeffrey T. (4 September 2013). "The Snowden Affair". nsarchive.gwu.edu. National Security Archive. Retrieved 9 June 2016.
- ^ Solove, Daniel J. (2011). Nothing to Hide: The False Tradeoff Between Privacy and Security. Yale University Press. ISBN 9780300177251.
- ^ Donohue, Laura K. (14 April 2008). The Cost of Counterterrorism: Power, Politics, and Liberty. Cambridge University Press. p. 258. ISBN 9781139469579.
- ^ Eric, Schmitt (1 August 2003). "Poindexter Will Be Quitting Over Terrorism Betting Plan". New York Times. Washington D.C. Retrieved 10 June 2016.
- ^ Mark Williams Pontin. The Total Information Awareness Project Lives On, MIT Technology Review, 26 April 2006, retrieved 16 June 2016
- ^ "Q&A on the Pentagon's "Total Information Awareness" Program". American Civil Liberties Union. April 20, 2003. Retrieved 19 December 2013.
- ^ ROB MORSE (November 20, 2002). "Fighting terror by terrifying U.S. citizens". San Francisco Chronicle . Retrieved 21 December 2013.
- ^ a b Clapper, James R,. (2018). Facts and Fears: Hard Truths From A Life In Intelligence (ebook ed.). New York: Viking. p. 226. ISBN 9780525558651.
{{cite book}}: CS1 maint: multiple names: authors list (link)
External links
[edit]Total Information Awareness
View on GrokipediaTotal Information Awareness (TIA) was a research and development program established by the United States Defense Advanced Research Projects Agency (DARPA) in the aftermath of the September 11, 2001 terrorist attacks, intended to integrate advanced information technologies for detecting, classifying, and preempting foreign terrorist threats through comprehensive data analysis.[1][2]
Directed by Rear Admiral John Poindexter as part of the DARPA Information Awareness Office, TIA aimed to overcome inter-agency information silos by developing tools for pattern recognition in transactional data—such as financial records, travel patterns, and communications—alongside biometric identification, natural language processing, and collaborative reasoning systems like Genisys, EELD, and Genoa II.[3][1]
Proponents highlighted embedded privacy protections, including anonymization methods, audit trails, and synthetic datasets for testing, to counterbalance security gains against civil liberties risks; however, the program's scale and potential for behavioral surveillance provoked substantial opposition, prompting Congress to enact funding restrictions in the Fiscal Year 2003 appropriations via Public Law 108-7, which barred deployment without certified safeguards and congressional oversight.[4][1][3]
These measures effectively dismantled TIA's overt structure, marking a pivotal case in the tension between national security imperatives and individual privacy rights, though core concepts influenced subsequent data analytics advancements in intelligence operations.[4]