Recent from talks
Nothing was collected or created yet.
Call stack
View on WikipediaThis article needs additional citations for verification. (September 2012) |
In computer science, a call stack is a stack data structure that stores information about the active subroutines and inline blocks of a computer program. This type of stack is also known as an execution stack, program stack, control stack, run-time stack, or machine stack, and is often shortened to simply the "stack". Although maintenance of the call stack is important for the proper functioning of most software, the details are normally hidden and automatic in high-level programming languages. Many computer instruction sets provide special instructions for manipulating stacks.
A call stack is used for several related purposes, but the main reason for having one is to keep track of the point to which each active subroutine should return control when it finishes executing. An active subroutine is one that has been called, but is yet to complete execution, after which control should be handed back to the point of call. Such activations of subroutines may be nested to any level (recursive as a special case), hence the stack structure. For example, if a subroutine DrawSquare calls a subroutine DrawLine from four different places, DrawLine must know where to return when its execution completes. To accomplish this, the address following the instruction that jumps to DrawLine, the return address, is pushed onto the top of the call stack as part of each call.
Description
[edit]Since the call stack is organized as a stack, the caller of a procedure pushes the return address onto the stack, and the called subroutine, when it finishes, pulls or pops the return address off the call stack and transfers control to that address; similarly, the prolog of an inline block pushes a stack frame and the epilog pops it. If a called subroutine calls on yet another subroutine, it will push another return address onto the call stack, and so on, with the information stacking up and unstacking as the program dictates. If the pushing consumes all of the space allocated for the call stack, an error called a stack overflow occurs, generally causing the program to crash. Adding a block's or subroutine's entry to the call stack is sometimes called "winding", and removing entries "unwinding".
There is usually exactly one call stack associated with a running program (or more accurately, with each task or thread of a process), although additional stacks may be created for signal handling or cooperative multitasking (as with setcontext). Since there is only one in this important context, it can be referred to as the stack (implicitly "of the task"); however, in the Forth programming language the data stack or parameter stack is accessed more explicitly than the call stack and is commonly referred to as the stack (see below).
In high-level programming languages, the specifics of the call stack are usually hidden from the programmer. They are given access only to a set of functions, and not the memory on the stack itself. This is an example of abstraction. Most assembly languages, on the other hand, require programmers to be involved in manipulating the stack. The actual details of the stack in a programming language depend upon the compiler, operating system, and the available instruction set.
Functions of the call stack
[edit]As noted above, the primary purpose of a call stack is to store the return addresses. When a subroutine is called, the location (address) of the instruction at which the calling routine can later resume must be saved somewhere. Using a stack to save the return address has important advantages over some alternative calling conventions, such as saving the return address before the beginning of the called subroutine or in some other fixed location. One is that each task can have its own stack, and thus the subroutine can be thread-safe, that is, able to be active simultaneously for different tasks doing different things. Another benefit is that by providing reentrancy, recursion is automatically supported. When a function calls itself recursively, a return address needs to be stored for each activation of the function so that it can later be used to return from the function activation. Stack structures provide this capability automatically.
Depending on the language, operating system, and machine environment, a call stack may serve additional purposes, including, for example:
- Local data storage
- A subroutine frequently needs memory space for storing the values of local variables, the variables that are known only within the active subroutine and do not retain values after it returns. It is often convenient to allocate space for this use by simply moving the top of the stack by enough to provide the space. This is very fast when compared to dynamic memory allocation, which uses the heap space. Note that each separate activation of a subroutine gets its own separate space in the stack for locals.
- Similarly, an inline block may allocate a stack frame for local variables. As with a call frame, the values are lost when the block exits.
- Parameter passing
- Subroutines often require that values for parameters be supplied to them by the code which calls them, and it is not uncommon that space for these parameters may be laid out in the call stack. Generally if there are only a few small parameters, processor registers will be used to pass the values, but if there are more parameters than can be handled this way, memory space will be needed. The call stack works well as a place for these parameters, especially since each call to a subroutine, which will have differing values for parameters, will be given separate space on the call stack for those values. In object-oriented languages such as C++, the list of parameters may also include the
thispointer. - Evaluation stack
- Operands for arithmetic or logical operations are most often placed into registers and operated on there. However, in some situations the operands may be stacked up to an arbitrary depth, which means something more than registers must be used (this is the case of register spilling). The stack of such operands, rather like that in an RPN calculator, is called an evaluation stack, and may occupy space in the call stack.
- Enclosing subroutine context
- Some programming languages (e.g., Pascal and Ada) support declaration of nested subroutines, which are allowed to access the context of their enclosing routines, i.e., the parameters and local variables within the scope of the outer routines. Such static nesting can repeat (a function declared within a function declared within a function…). The implementation must provide a means by which a called function at any given static nesting level can reference the enclosing frame at each enclosing nesting level. This reference is commonly implemented by a pointer to the frame of the most recently activated instance of the enclosing function, called a "downstack link" or "static link", to distinguish it from the "dynamic link" that refers to the immediate caller (which need not be the static parent function).
- Instead of a static link, the references to the enclosing static frames may be collected into an array of pointers known as a display which is indexed to locate a desired frame. The depth of a routine's lexical nesting is a known constant, so the size of a routine's display is fixed. Also, the number of containing scopes to traverse is known, the index into the display is also fixed. Usually, a routine's display is located in its own stack frame, but the Burroughs B6500 implemented such a display in hardware which supported up to 32 levels of static nesting.
- The display entries denoting containing scopes are obtained from the appropriate prefix of the caller's display. An inner routine which recurses creates separate call frames for each invocation. In this case, all of the inner routine's static links point to the same outer routine context.
- Enclosed block context
- In some languages, e.g., ALGOL 60, PL/I, a block within a procedure may have its own local variables, allocated on block entry and freed on block exit. Similarly, the block may have its own exception handlers, deactivated at block exit.
- Other return state
- Beside the return address, in some environments there may be other machine or software states that need to be restored when a subroutine returns. This might include things like privilege level, exception-handling information, arithmetic modes, and so on. If needed, this may be stored in the call stack just as the return address is.
The typical call stack is used for the return address, locals, and parameters (known as a call frame). In some environments there may be more or fewer functions assigned to the call stack. In the Forth programming language, for example, ordinarily only the return address, counted loop parameters and indexes, and possibly local variables are stored on the call stack (which in that environment is named the return stack), although any data can be temporarily placed there using special return-stack handling code so long as the needs of calls and returns are respected; parameters are ordinarily stored on a separate data stack or parameter stack, typically called the stack in Forth terminology even though there is a call stack since it is usually accessed more explicitly. Some Forths also have a third stack for floating-point parameters.
Structure
[edit]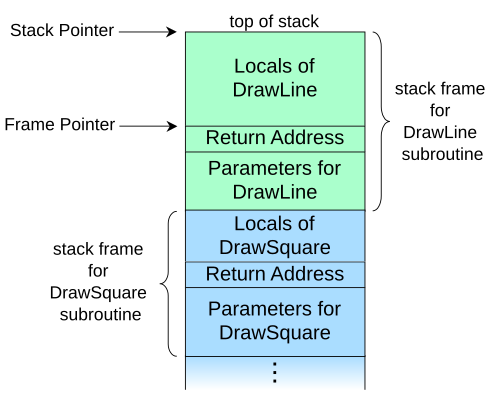
DrawSquare subroutine (shown in blue) called DrawLine (shown in green), which is the currently executing routineA call stack is composed of stack frames (also called activation records or activation frames). These are machine dependent and ABI-dependent data structures containing subroutine state information. Each stack frame corresponds to an invocation of a subroutine that has not yet completed with a return.[1] The stack frame at the top of the stack is for the currently executing routine. For example, if a subroutine named DrawLine is currently running, having been called by a subroutine DrawSquare, the top part of the call stack might be laid out like in the adjacent picture.
A diagram like this can be drawn in either direction as long as the placement of the top, and so direction of stack growth, is understood. Architectures differ as to whether call stacks grow towards higher addresses or towards lower addresses, so the logic of any diagram is not dependent on this addressing choice by convention.
While it is actively executing, with its frame at the stack top, a routine can access the information within its frame as needed.[2] The stack frame typically includes at least the following items (in the order pushed):
- the arguments (parameter values) passed to the routine on the call stack (if any);
- the return address back to the routine's caller (e.g. in the
DrawLinestack frame, an address intoDrawSquare's code), if that is saved on the call stack rather than a register; and - space for the local variables of the routine (if any).
Stack and frame pointers
[edit]When stack frame sizes can differ, such as between different functions or between invocations of a particular function, popping a frame off the stack does not constitute a fixed decrement of the stack pointer. At function return, the stack pointer is instead restored to the frame pointer, the value of the stack pointer just before the function was called. Each stack frame contains a frame pointer to the top of the frame immediately below. The stack pointer is a mutable register shared between all invocations. A frame pointer of a given invocation of a function is a copy of the stack pointer as it was before the function was invoked.[3]
The locations of all other fields in the frame can be defined relative either to the top of the frame, as negative offsets of the stack pointer, or relative to the top of the frame below, as positive offsets of the frame pointer. The location of the frame pointer itself must inherently be defined as a negative offset of the stack pointer.
Storing the address to the caller's frame
[edit]In most systems a stack frame has a field to contain the previous value of the frame pointer register, the value it had while the caller was executing. For example, the stack frame of DrawLine would have a memory location holding the frame pointer value that DrawSquare uses (not shown in the diagram above). The value is saved upon entry to the subroutine. Having such a field in a known location in the stack frame enables code to access each frame successively underneath the currently executing routine's frame, and also allows the routine to easily restore the frame pointer to the caller's frame, just before it returns.
Lexically nested routines
[edit]Programming languages that support nested subroutines also have a field in the call frame that points to the stack frame of the latest activation of the procedure that most closely encapsulates the callee, i.e. the immediate scope of the callee. This is called an access link or static link (as it keeps track of static nesting during dynamic and recursive calls) and provides the routine (as well as any other routines it may invoke) access to the local data of its encapsulating routines at every nesting level. Some architectures, compilers, or optimization cases store one link for each enclosing level (not just the immediately enclosing), so that deeply nested routines that access shallow data do not have to traverse several links; this strategy is often called a "display".[4]
Access links can be optimized away when an inner function does not access any (non-constant) local data in the encapsulation, as is the case with pure functions communicating only via arguments and return values, for example. Some historical computers, such as the Electrologica X8 and somewhat later the Burroughs large systems, had special "display registers" to support nested functions, while compilers for most modern machines (such as the ubiquitous x86) simply reserve a few words on the stack for the pointers, as needed.
Overlap
[edit]For some purposes, the stack frame of a subroutine and that of its caller can be considered to overlap, the overlap consisting of the area where the parameters are passed from the caller to the callee. In some environments, the caller pushes each argument onto the stack, thus extending its stack frame, then invokes the callee. In other environments, the caller has a preallocated area at the top of its stack frame to hold the arguments it supplies to other subroutines it calls. This area is sometimes termed the outgoing arguments area or callout area. Under this approach, the size of the area is calculated by the compiler to be the largest needed by any called subroutine.
Use
[edit]Call site processing
[edit]Usually the call stack manipulation needed at the site of a call to a subroutine is minimal (which is good since there can be many call sites for each subroutine to be called). The values for the actual arguments are evaluated at the call site, since they are specific to the particular call, and either pushed onto the stack or placed into registers, as determined by the used calling convention. The actual call instruction, such as "branch and link", is then typically executed to transfer control to the code of the target subroutine.
Subroutine entry processing
[edit]In the called subroutine, the first code executed is usually termed the subroutine prologue, since it does the necessary housekeeping before the code for the statements of the routine is begun.
For instruction set architectures in which the instruction used to call a subroutine puts the return address into a register, rather than pushing it onto the stack, the prologue will commonly save the return address by pushing the value onto the call stack, although if the called subroutine does not call any other routines it may leave the value in the register. Similarly, the current stack pointer and/or frame pointer values may be pushed.
If frame pointers are being used, the prologue will typically set the new value of the frame pointer register from the stack pointer. Space on the stack for local variables can then be allocated by incrementally changing the stack pointer.
The Forth programming language allows explicit winding of the call stack (called there the "return stack").
Return processing
[edit]When a subroutine is ready to return, it executes an epilogue that undoes the steps of the prologue. This will typically restore saved register values (such as the frame pointer value) from the stack frame, pop the entire stack frame off the stack by changing the stack pointer value, and finally branch to the instruction at the return address. Under many calling conventions, the items popped off the stack by the epilogue include the original argument values, in which case there usually are no further stack manipulations that need to be done by the caller. With some calling conventions, however, it is the caller's responsibility to remove the arguments from the stack after the return.
Unwinding
[edit]Returning from the called function will pop the top frame off the stack, perhaps leaving a return value. The more general act of popping one or more frames off the stack to resume execution elsewhere in the program is called stack unwinding and must be performed when non-local control structures are used, such as those used for exception handling. In this case, the stack frame of a function contains one or more entries specifying exception handlers. When an exception is thrown, the stack is unwound until a handler is found that is prepared to handle (catch) the type of the thrown exception.
Some languages have other control structures that require general unwinding. Pascal allows a global goto statement to transfer control out of a nested function and into a previously invoked outer function. This operation requires the stack to be unwound, removing as many stack frames as necessary to restore the proper context to transfer control to the target statement within the enclosing outer function. Similarly, C has the setjmp and longjmp functions that act as non-local gotos. Common Lisp allows control of what happens when the stack is unwound by using the unwind-protect special operator.
When applying a continuation, the stack is (logically) unwound and then rewound with the stack of the continuation. This is not the only way to implement continuations; for example, using multiple, explicit stacks, application of a continuation can simply activate its stack and wind a value to be passed. The Scheme programming language allows arbitrary thunks to be executed in specified points on "unwinding" or "rewinding" of the control stack when a continuation is invoked.
Inspection
[edit]The call stack can sometimes be inspected as the program is running. Depending on how the program is written and compiled, the information on the stack can be used to determine intermediate values and function call traces. This has been used to generate fine-grained automated tests,[5] and in cases like Ruby and Smalltalk, to implement first-class continuations. As an example, the GNU Debugger (GDB) implements interactive inspection of the call stack of a running, but paused, C program.[6]
Taking regular-time samples of the call stack can be useful in profiling the performance of programs as, if a subroutine's address appears in the call stack sampling data many times, it is likely to act as a code bottleneck and should be inspected for performance problems.
Security
[edit]In a language with free pointers or non-checked array writes (such as in C), the mixing of control flow data which affects the execution of code (the return addresses or the saved frame pointers) and simple program data (parameters or return values) in a call stack is a security risk, and is possibly exploitable through stack buffer overflows, which are the most common type of buffer overflow.
One such attack involves filling one buffer with arbitrary executable code, and then overflowing this or some other buffer to overwrite some return address with a value that points directly to the executable code. As a result, when the function returns, the computer executes that code. This kind of an attack can be blocked with W^X,[citation needed] but similar attacks can succeed even with W^X protection enabled, including the return-to-libc attack or the attacks coming from return-oriented programming. Various mitigations have been proposed, such as storing arrays in a completely separate location from the return stack, as is the case in the Forth programming language.[7]
See also
[edit]References
[edit]- ^ "Examining the Stack". University of Utah. Archived from the original on September 12, 2019. Retrieved April 3, 2025.
- ^ Krzyzanowski, Paul (February 16, 2018). "Stack frames". Rutgers University. Archived from the original on 2021-08-28. Retrieved December 19, 2021.
- ^ "Understanding the Stack". cs.umd.edu. 2003-06-22. Archived from the original on 2013-02-25. Retrieved 2014-05-21.
- ^ Alternative Microprocessor Design
- ^ McMaster, S.; Memon, A. (2006). Call Stack Coverage for GUI Test-Suite Reduction (PDF). 17th International Symposium on Software Reliability Engineering (ISSRE '06). pp. 33–44. CiteSeerX 10.1.1.88.873. doi:10.1109/ISSRE.2006.19. ISBN 0-7695-2684-5.
- ^ "Debugging with GDB: Examining the Stack". chemie.fu-berlin.de. 1997-10-17. Archived from the original on 2021-04-14. Retrieved 2014-12-16.
- ^ Doug Hoyte. "The Forth Programming Language - Why YOU should learn it".
Further reading
[edit]- Dijkstra, E. W. (1960). "Recursive Programming". Numerische Mathematik. 2 (1): 312–318. doi:10.1007/BF01386232.
- Wilson, P. R.; Johnstone, M. S.; Neely, M.; Boles, D. (1995). "Dynamic storage allocation: A survey and critical review". Memory Management. Lecture Notes in Computer Science. Vol. 986. pp. 1–116. CiteSeerX 10.1.1.47.275. doi:10.1007/3-540-60368-9_19. ISBN 978-3-540-60368-9.
- "2.4. The Stack". MCS-4 Assembly Language Programming Manual - The INTELLEC 4 Microcomputer System Programming Manual (PDF) (Preliminary ed.). Santa Clara, California, USA: Intel Corporation. December 1973. pp. 2-7 – 2-8. MCS-030-1273-1. Archived (PDF) from the original on 2020-03-01. Retrieved 2020-03-02. (NB. Intel's 4-bit processor 4004 implements an internal stack rather than an in-memory stack.)
External links
[edit]- Function Calling and Frame Pointer Operations in 68000 Archived 2010-07-24 at the Wayback Machine
- The libunwind project - a platform-independent unwind API
Call stack
View on GrokipediaFundamentals
Definition and Purpose
A call stack is a stack data structure that stores information about the active subroutines of a computer program, typically consisting of a series of frames each representing a function call with its arguments, local variables, and return address.[4] This structure operates on a last-in, first-out (LIFO) principle, where the most recent subroutine call is placed on top and removed first upon completion.[4] The primary purpose of the call stack is to track the point of execution within a program, enabling the processor to resume the calling routine correctly after a subroutine finishes, which is essential for handling nested calls and recursion without losing the execution context.[5] By maintaining this ordered record, it supports modular programming by allowing subroutines to invoke one another while preserving the integrity of the overall program flow.[4] The concept of the call stack originated in the context of subroutine calls in early computing machines, with roots in the von Neumann architecture's emphasis on sequential instruction execution and the need for mechanisms to handle jumps and returns in stored-program computers.[5] Early computers like EDSAC (1949) developed mechanisms for subroutines by manually saving return addresses, laying the groundwork for stack-based management of nested routines.[5] Commonly analogized to a stack of plates, the call stack adds a new "plate" (frame) for each subroutine entry and removes the top one upon return, ensuring that deeper nested calls are resolved in reverse order of invocation.[6]Role in Program Execution
The call stack integrates with the CPU by managing the program counter and return addresses during jumps to subroutines, allowing the processor to save the address of the next instruction before transferring control and restore it upon return to ensure seamless continuity of execution.[7][8] When a subroutine is called, the CPU pushes the return address—derived from the current program counter—onto the stack, and upon completion, pops it to resume the caller, preventing loss of execution context.[7] This mechanism supports recursion by enabling nested subroutine calls, where each invocation creates a new entry on the stack to maintain independent states until stack limits are reached, as seen in the factorial computation example.[9] For instance, computing factorial(3) involves successive calls: factorial(3) pushes a frame, calls factorial(2), which pushes another and calls factorial(1), reaching the base case factorial(0) that returns 1; the stack then unwinds, with each level multiplying and returning (factorial(1) returns 1, factorial(2) returns 2, factorial(3) returns 6).[9] Stack frames briefly store local variables like the parameter n in each recursive level to isolate computations.[9] In multi-threaded programs, each thread has its own call stack to maintain isolation of subroutine states, ensuring that each thread's control flow and local data remain separate without interference. In single-threaded execution, a single call stack manages the program's subroutine states.[10] Without a call stack, programs would lose return addresses during subroutine jumps, leading to inability to resume prior execution, resulting in crashes, infinite loops, or complete failure to handle nested calls like recursion.[7][8]Structure and Components
Stack Frames
A stack frame, also known as an activation record, represents the data structure allocated on the call stack for a single subroutine invocation, encapsulating all elements required for its execution. It serves as a self-contained unit that isolates the subroutine's state from other active calls, ensuring proper management of resources during program flow.[11] The primary components of a stack frame include the return address, which specifies the instruction to resume execution in the caller after the subroutine completes; function parameters, passed from the caller to provide input values; local variables, which store temporary data scoped to the subroutine; and saved registers, which preserve the caller's register values to allow restoration upon return. These elements collectively enable the subroutine to operate independently while maintaining continuity with the broader program context.[12][13] Stack frames are dynamically allocated upon subroutine entry, typically by decrementing the stack pointer to reserve space on the stack, and deallocated upon exit by incrementing the stack pointer to release the memory. This push-and-pop mechanism ensures efficient reuse of stack space without manual intervention by the programmer.[11] The size of a stack frame varies based on the specific needs of the subroutine, including the quantity and data types of parameters and local variables, as well as any saved registers. In C-like languages, frames for subroutines with fixed-size local variables and parameters have sizes determined at compile time, allowing for predictable allocation. However, when variable-length arrays (VLAs) are used, the frame size becomes dynamic, computed at runtime based on the array's length to accommodate flexible data structures.[12][14] A typical stack frame layout organizes components at specific offsets relative to a base reference point, such as the frame pointer, to facilitate access. From higher to lower memory addresses, the structure often appears as follows:Higher address
+--------------------+
| Parameters | (e.g., offsets +8 to +20)
+--------------------+
| Return address | (e.g., offset +4)
+--------------------+
| Saved FP (dynamic link) | (offset 0)
+--------------------+
| Saved registers | (e.g., offsets -4 to -8)
+--------------------+
| Local variables | (e.g., offsets -12 to -20)
+--------------------+
Lower address
Higher address
+--------------------+
| Parameters | (e.g., offsets +8 to +20)
+--------------------+
| Return address | (e.g., offset +4)
+--------------------+
| Saved FP (dynamic link) | (offset 0)
+--------------------+
| Saved registers | (e.g., offsets -4 to -8)
+--------------------+
| Local variables | (e.g., offsets -12 to -20)
+--------------------+
Lower address
Pointers and Frame Management
In the management of the call stack, the stack pointer (SP) serves as a register that points to the current top of the stack, facilitating the dynamic allocation and deallocation of space through push and pop operations that adjust its value accordingly.[16] This adjustment ensures that each new stack frame occupies contiguous memory immediately above the previous top, with the SP decrementing on pushes to allocate space and incrementing on pops to reclaim it.[11] The frame pointer (FP), commonly referred to as the base pointer (BP) in x86 architectures, provides a fixed reference to the base address of the current stack frame once established, enabling consistent relative addressing for local variables, parameters, and saved registers regardless of subsequent SP movements within the frame.[16] By anchoring access to the frame's beginning, the FP simplifies code generation for compilers, as offsets from FP remain stable even as the SP varies for temporary allocations.[17] To support navigation through the call stack, each frame includes a saved copy of the caller's frame pointer, termed the dynamic link, which is stored at the base of the new frame and allows sequential traversal backward to parent frames during debugging, exception handling, or unwinding.[18] This linking mechanism forms a chain of frames connected via these pointers, preserving the runtime call hierarchy without requiring global knowledge of the stack layout.[18] During function entry, the SP and FP are adjusted to establish the new frame, typically involving saving the old FP, updating the FP to the current SP, and then decrementing the SP to reserve space for locals while adhering to architecture-specific alignment rules. In x86-64, the stack must be aligned to a 16-byte boundary at the point of function entry to optimize performance for instructions like those in SSE/AVX extensions.[19] The following pseudocode illustrates a standard x86 prologue for frame setup:# Function prologue (x86 assembly equivalent)
push %ebp # Save caller's FP (dynamic link)
mov %esp, %ebp # Set FP to current SP (base of new frame)
sub $frame_size, %esp # Allocate space for [locals](/page/Locals) (adjust SP)
# Ensure alignment: if needed, add padding so %esp % 16 == 8 (post-call alignment)
# Function prologue (x86 assembly equivalent)
push %ebp # Save caller's FP (dynamic link)
mov %esp, %ebp # Set FP to current SP (base of new frame)
sub $frame_size, %esp # Allocate space for [locals](/page/Locals) (adjust SP)
# Ensure alignment: if needed, add padding so %esp % 16 == 8 (post-call alignment)
Nested Routines and Overlap
In languages supporting lexical nesting of routines, such as Pascal and Ada, an inner routine defined within an outer routine can access variables from the outer routine's scope during execution.[20] This access is facilitated by mechanisms that link the activation records (stack frames) of nested routines, ensuring the inner routine can reference non-local variables correctly under static scoping rules.[21] Common implementations include static links or display structures to traverse the lexical hierarchy without relying solely on dynamic call chains. The static chain method, widely used in Pascal and Ada compilers, involves each activation record containing a static link pointer to the activation record of the immediately enclosing routine in the source code.[20] When an inner routine is called, the static link is copied from the caller's record, forming a chain that allows the routine to follow pointers back through the nesting levels to access outer variables. Alternatively, display structures maintain an array of pointers in each activation record, directly indexing to the most recent activation of each enclosing lexical level, which can reduce traversal overhead for deep nesting at the cost of additional space. Overlap scenarios arise in certain calling conventions where stack frames do not fully nest but temporarily share space, such as in tail calls or coroutines. In tail calls, the called routine reuses the current stack frame by overwriting the caller's frame before invoking the callee, preventing stack growth and enabling efficient recursion without additional depth.[22] Coroutines, which support suspension and resumption, can implement overlapping frames by saving and restoring partial stack states, allowing multiple routines to share stack space without complete nesting, as seen in implementations where yields transfer control while preserving lexical context.[23] Deep lexical nesting, particularly in recursive calls, causes progressive stack growth as each inner activation record allocates space atop the previous ones, potentially leading to stack overflow if the nesting depth exceeds available stack memory.[24] This limitation is exacerbated in languages like Pascal, where unbounded recursion in nested routines can exhaust stack resources before completing, necessitating careful design or tail-call optimization to mitigate overflow risks.[24]Operations
Function Call Processing
When a program invokes a subroutine, the call site performs a series of actions to prepare for the transfer of control. This typically involves pushing function arguments onto the stack in a specific order (often right-to-left to allow the leftmost to be at the lowest address), saving the return address (the address of the instruction following the call) onto the stack or into a dedicated register, and then executing an unconditional jump to the subroutine's entry point. These steps ensure that the subroutine can access its parameters and return control to the caller upon completion. Parameter passing mechanisms vary by calling convention and language semantics, influencing how data is transferred to the subroutine. In pass-by-value, the call site pushes copies of the argument values onto the stack, ensuring the subroutine receives independent data without affecting the caller's originals; this is common in C for scalar types. Conversely, pass-by-reference passes the memory addresses of arguments, allowing the subroutine to modify the caller's data indirectly, as seen in C++ references or pointers. Calling conventions dictate implementation: stack-based ones, like the System V ABI for x86, push all arguments onto the stack, while register-based conventions, such as x86-64's System V (which uses registers RDI, RSI, RDX, RCX, R8, R9 for the first six integer/pointer arguments before spilling to the stack), optimize for speed by minimizing memory accesses. In the Microsoft x64 calling convention, the first four integer arguments go into RCX, RDX, R8, and R9, with floating-point args in XMM0-XMM3, followed by stack usage for additional parameters. Before the jump, the call site may perform prologue-like preparations to align the stack pointer (often to a 16-byte boundary in x86-64 for SIMD instructions) and reserve shadow space—a fixed 32-byte area on the stack in Microsoft x64 for the callee to spill registers without immediate conflicts. This setup facilitates smooth entry into the subroutine while adhering to ABI requirements. Arguments not fitting in registers are stored in stack frames allocated for this purpose. Compilers often apply optimizations to streamline or eliminate these steps. Inlining replaces the call with the subroutine's body directly at the site, bypassing stack operations entirely for small, frequently called functions, which reduces overhead and enables further optimizations like constant propagation. Tail call optimization may transform a call into a direct jump if it's the last operation, reusing the current stack frame and avoiding new allocations, as supported in languages like Scheme per tail-call elimination standards.Subroutine Entry and Setup
Upon entering a subroutine, the entry sequence begins by saving the caller's state to preserve the execution context, followed by allocating a new stack frame and initializing local variables. This process ensures that the subroutine can operate independently without corrupting the caller's environment. The saving of the caller's state typically involves storing the return address, which was pushed onto the stack by the call instruction, and preserving any callee-saved registers that the subroutine might modify.[25][26] The prologue code, executed at the start of the subroutine, handles the core setup using assembly instructions to manage the stack frame. A common sequence in x86-64 architecture pushes the frame pointer (e.g.,push rbp) to save the caller's frame pointer, sets the new frame pointer to the current stack pointer (e.g., mov rbp, rsp), and reserves space for local variables by subtracting from the stack pointer (e.g., sub rsp, 8*l where l is the number of words needed). This establishes a reference point for accessing locals and parameters relative to the frame pointer, as detailed further in stack frame management.[25][26]
For variadic functions in C, which accept a variable number of arguments, the entry setup incorporates mechanisms to access the additional arguments beyond the fixed ones. The <stdarg.h> header provides macros like va_start to initialize a va_list object, typically implemented as a pointer to the location on the stack immediately following the last fixed argument, allowing sequential access via va_arg. No distinct prologue instructions are added solely for variadics; instead, the function's code uses these macros after standard frame setup to traverse the argument list stored on the stack.[27]
Error conditions during entry primarily arise from stack overflow when allocating the frame, such as subtracting a large value from the stack pointer that exceeds available stack space. Operating systems detect this via page faults when the process attempts to access unmapped memory beyond the allocated stack guard pages, triggering a segmentation fault or similar exception to prevent corruption. In some runtime environments, explicit checks may compare the stack pointer against predefined limits before allocation, but hardware-assisted detection via memory management units is standard in modern OSes.[28][29]
Return and Unwinding
When a subroutine completes its execution, the return sequence begins by preparing the return value, if any, which is typically placed in a designated register such as %rax in x86-64 architectures.[26] The callee then restores any saved registers, such as callee-saved registers like %ebx, %esi, and %edi, to their previous states before the call.[30] Finally, the return instruction (RET) pops the return address from the top of the stack and jumps to it, resuming execution in the caller.[30] This process ensures the program's control flow returns precisely to the point after the original call site.[31] The epilogue code, executed at the end of the subroutine, handles the cleanup symmetric to the prologue's setup. It deallocates the stack frame by adjusting the stack pointer (%esp or %rsp) to release local variables and temporary storage, often using instructions like LEAVE, which first restores the frame pointer (%ebp or %rbp) by popping its saved value and then sets the stack pointer to match.[30] This restoration repositions the frame pointer to point to the caller's frame, effectively dismantling the current activation record.[32] Return values are adjudicated during this phase, with the stack pointer incremented to remove the return address after the jump.[32] In assembly, this might appear as:leave
ret
leave
ret
Applications and Analysis
Inspection Techniques
Inspection techniques for the call stack enable developers to examine the sequence of active function calls during program execution, aiding in debugging and performance analysis. These methods typically involve traversing the stack frames from the current execution point back to the program's entry, revealing the call hierarchy, local variables, and execution context. Such inspection is crucial for diagnosing issues like infinite recursion, memory leaks, or unexpected control flow, without halting the program entirely in some cases. Stack traces provide a textual report of the active stack frames, listing functions, source files, and line numbers in reverse chronological order from the most recent call. In Java, theThread.dumpStack() method generates such a trace for the current thread, printing it to the standard error stream for immediate debugging of runtime errors.[38] This output helps identify the path leading to exceptions, such as in error reporting where the trace captures the state at the point of failure. Similarly, in C# via the .NET framework, the Environment.StackTrace property retrieves a string representation of the stack trace, useful for logging and post-mortem analysis.[39]
Debuggers like the GNU Debugger (GDB) facilitate interactive stack inspection by walking the call stack using frame pointers or unwinding information. The backtrace (or bt) command in GDB displays the stack frames, allowing users to switch between them with frame n to inspect local variables, arguments, and registers in each frame. This technique relies on the program's frame pointer register or DWARF debugging data to navigate the stack accurately, even in optimized code where frame pointers may be omitted. For instance, during a breakpoint, GDB can reveal variable values across nested calls, helping trace data flow issues.
Runtime APIs offer programmatic access to the call stack for custom inspection within the application code. In the GNU C Library (glibc), the backtrace() function captures an array of return addresses representing the current stack frames, which can then be symbolized using backtrace_symbols() to produce human-readable strings including function names and offsets. This is particularly useful in signal handlers or logging routines to generate traces on demand without external tools, though it requires linking against the libexecinfo or similar for symbol resolution. The function returns the number of frames captured, limited by the provided buffer size to avoid overflows.
Visualization tools in integrated development environments (IDEs) enhance stack inspection by providing graphical representations of the call hierarchy. In Visual Studio, the Call Stack window displays the active frames during debugging sessions, with options to view on a code map for a visual trace of method calls and dependencies.[40] Users can annotate these maps to note execution states, facilitating the identification of bugs in complex call graphs, such as circular dependencies or deep recursion. This graphical approach contrasts with textual traces by allowing interactive navigation and filtering of frames, improving usability for large-scale applications.
