Recent from talks
Nothing was collected or created yet.
QR code
View on Wikipedia

A QR code, short for quick-response code,[1] is a type of two-dimensional matrix barcode invented in 1994 by Masahiro Hara of the Japanese company Denso Wave for labelling automobile parts.[2][3] It features black squares on a white background with fiducial markers, readable by imaging devices like cameras, and processed using Reed–Solomon error correction until the image can be appropriately interpreted. The required data is then extracted from patterns that are present in both the horizontal and the vertical components of the QR image.[4]
Whereas a barcode is a machine-readable optical image that contains information specific to the labeled item, the QR code contains the data for a locator, an identifier, and web tracking. To store data efficiently, QR codes use four standardized modes of encoding: numeric, alphanumeric, byte or binary, and kanji.[5] Compared to standard UPC barcodes, the QR labeling system was applied beyond the automobile industry because of faster reading of the optical image and greater data-storage capacity in applications such as product tracking, item identification, time tracking, document management, and general marketing.[4]
History
[edit]The QR code system was invented in 1994, at the Denso Wave automotive products company in Japan.[6][7][8] The initial alternating-square design presented by the team of researchers, headed by Masahiro Hara, was influenced by the black counters and the white counters played on a Go board;[9] the pattern of the position detection markers was determined by finding the least-used sequence of alternating black-white areas on printed matter, which was found to be (1:1:3:1:1).[10][6] The functional purpose of the QR code system was to facilitate keeping track of the types and numbers of automobile parts, by replacing individually-scanned bar-code labels on each box of auto parts with a single label that contained the data of each label. The quadrangular configuration of the QR code system consolidated the data of the various bar-code labels with kanji, kana, and alphanumeric codes printed onto a single label.[11][10][6]
Adoption
[edit]
During June 2011, 14 million American mobile users scanned a QR code or a barcode. Some 58% of those users scanned a QR or barcode from their homes, while 39% scanned from retail stores; 53% of the 14 million users were men between the ages of 18 and 34.[12]
In 2022, 89 million people in the United States scanned a QR code using their mobile devices, up by 26 percent compared to 2020. The majority of QR code users used them to make payments or to access product and menu information.[13]
In September 2020, a survey found that 18.8 percent of consumers in the United States and the United Kingdom strongly agreed that they had noticed an increase in QR code use since the then-active COVID-19-related restrictions had begun several months prior.[14]
As of 2024,[update] QR codes are used in a much broader context, including both commercial tracking applications and convenience-oriented applications aimed at mobile phone users (termed mobile tagging). QR codes may be used to display text to the user, to open a webpage on the user's device, to add a vCard contact to the user's device, to open a Uniform Resource Identifier (URI), to connect to a wireless network, or to compose an email or text message. There are a great many QR code generators available as software or as online tools that are either free or require a paid subscription.[15] The QR code has become one of the most-used types of two-dimensional code.[16]
Standards
[edit]
Several standards cover the encoding of data as QR codes:[17]
- October 1997 – AIM (Association for Automatic Identification and Mobility) International[18]
- January 1999 – JIS X 0510
- June 2000 – ISO/IEC 18004:2000 Information technology – Automatic identification and data capture techniques – Bar code symbology – QR code (now withdrawn)
Defines QR code models 1 and 2 symbols. - 1 September 2006 – ISO/IEC 18004:2006 Information technology – Automatic identification and data capture techniques – QR Code 2005 bar code symbology specification (now withdrawn)[19]
Defines QR code 2005 symbols, an extension of QR code model 2. Does not specify how to read QR code model 1 symbols, or require this for compliance. - 1 February 2015 – ISO/IEC 18004:2015 Information – Automatic identification and data capture techniques – QR Code barcode symbology specification (now withdrawn)
Renames the QR Code 2005 symbol to QR Code and adds clarification to some procedures and minor corrections. It was withdrawn and updated to 18004:2024 in August 2024, which optimizes encoding efficiency, improves error correction, and refines structured append functionality.[20] - May 2022 – ISO/IEC 23941:2022 Information technology – Automatic identification and data capture techniques – Rectangular Micro QR Code (rMQR) bar code symbology specification[21]
Defines the requirements for Micro QR Code. - August 2024 – ISO/IEC 18004:2024 Information technology — Automatic identification and data capture techniques — QR code bar code symbology specification
At the application layer, there is some variation between most of the implementations. Japan's NTT DoCoMo has established de facto standards for the encoding of URLs, contact information, and several other data types.[22] The open-source "ZXing" project maintains a list of QR code data types.[23]
Uses
[edit]
QR codes have become common in consumer advertising. Typically, a smartphone is used as a QR code scanner, displaying the code and converting it to some useful form (such as a standard URL for a website, thereby obviating the need for a user to type it into a Web browser).
QR codes have become a focus of advertising strategy to provide a way to access a brand's website more quickly than by manually entering a URL.[24][25] Beyond mere convenience to the consumer, the importance of this capability is the belief that it increases the conversion rate: the chance that contact with the advertisement will convert to a sale. It coaxes interested prospects further down the conversion funnel with little delay or effort, bringing the viewer to the advertiser's website immediately, whereas a longer and more targeted sales pitch may lose the viewer's interest.
Although initially used to track parts in vehicle manufacturing, QR codes are used over a much wider range of applications. These include commercial tracking, warehouse stock control, entertainment and transport ticketing, product and loyalty marketing, and in-store product labeling.[citation needed] Examples of marketing include where a company's discounted and percent discount can be captured using a QR code decoder that is a mobile app, or storing a company's information such as address and related information alongside its alpha-numeric text data as can be seen in telephone directory yellow pages.[citation needed]

They can also be used to store personal information for organizations. An example of this is the Philippines National Bureau of Investigation (NBI) where NBI clearances now come with a QR code. Many of these applications target mobile-phone users (via mobile tagging). Users may receive text, add a vCard contact to their device, open a URL, or compose an e-mail or text message after scanning QR codes. They can generate and print their own QR codes for others to scan and use by visiting one of several pay or free QR code-generating sites or apps. Google had an API, now deprecated, to generate QR codes,[26] and apps for scanning QR codes can be found on nearly all smartphone devices.[27]

QR codes storing addresses and URLs may appear in magazines, on signs, on buses, on business cards, or on almost any object about which users might want information. Users with a camera phone equipped with the correct reader application can scan the image of the QR code to display text and contact information, connect to a wireless network, or open a web page in the phone's browser. This act of linking from physical world objects is termed hardlinking or object hyperlinking. QR codes also may be linked to a location to track where a code has been scanned. Either the application that scans the QR code retrieves the geo information by using GPS and cell tower triangulation (aGPS) or the URL encoded in the QR code itself is associated with a location. In 2008, a Japanese stonemason announced plans to engrave QR codes on gravestones, allowing visitors to view information about the deceased, and family members to keep track of visits.[29] Psychologist Richard Wiseman was one of the first authors to include QR codes in a book, in Paranormality: Why We See What Isn't There (2011).[30] Microsoft Office and LibreOffice have a functionality to insert QR code into documents.[31][32]
QR codes have been incorporated into currency. In June 2011, The Royal Dutch Mint (Koninklijke Nederlandse Munt) issued the world's first official coin with a QR code to celebrate the centenary of its current building and premises. The coin can be scanned by a smartphone and originally linked to a special website with content about the historical event and design of the coin.[33] In 2014, the Central Bank of Nigeria issued a 100-naira banknote to commemorate its centennial, the first banknote to incorporate a QR code in its design. When scanned with an internet-enabled mobile device, the code goes to a website that tells the centenary story of Nigeria.[34]
In 2015, the Central Bank of the Russian Federation issued a 100-rubles note to commemorate the annexation of Crimea by the Russian Federation.[35] It contains a QR code into its design, and when scanned with an internet-enabled mobile device, the code goes to a website that details the historical and technical background of the commemorative note. In 2017, the Bank of Ghana issued a 5-cedis banknote to commemorate 60 years of central banking in Ghana. It contains a QR code in its design which, when scanned with an internet-enabled mobile device, goes to the official Bank of Ghana website.
In September 2016, the Reserve Bank of India (RBI) launched the eponymously named BharatQR, a common QR code jointly developed by all the four major card payment companies – National Payments Corporation of India that runs RuPay cards along with Mastercard, Visa, and American Express. It will also have the capability of accepting payments on the Unified Payments Interface (UPI) platform.[36][37]
Augmented reality
[edit]QR codes are used in some augmented reality systems to determine the positions of objects in 3-dimensional space.[11]
Mobile operating systems
[edit]QR codes can be used on various mobile device operating systems. While initially requiring the installation and use of third-party apps, both Android and iOS (since iOS 11[38][39]) devices can now natively scan QR codes, without requiring an external app to be used.[40] The camera app can scan and display the kind of QR code along with the link. These devices support URL redirection, which allows QR codes to send metadata to existing applications on the device.
Virtual stores
[edit]QR codes have been used to establish "virtual stores", where a gallery of product information and QR codes is presented to the customer, e.g. on a train station wall. The customers scan the QR codes, and the products are delivered to their homes. This use started in South Korea,[41] and Argentina,[42] but is currently expanding globally.[43] Walmart, Procter & Gamble and Woolworths have already adopted the Virtual Store concept.[44]
QR code payment
[edit]QR codes can be used to store bank account information or credit card information, or they can be specifically designed to work with particular payment provider applications. There are several trial applications of QR code payments across the world.[45][46] In developing countries including China,[47][48] India[49] QR code payment is a very popular and convenient method of making payments. Since Alipay designed a QR code payment method in 2011,[50] mobile payment has been quickly adopted in China. As of 2018, around 83% of all payments were made via mobile payment.[51]
In November 2012, QR code payments were deployed on a larger scale in the Czech Republic when an open format for payment information exchange – a Short Payment Descriptor – was introduced and endorsed by the Czech Banking Association as the official local solution for QR payments.[52][53] In 2013, the European Payment Council provided guidelines for the EPC QR code enabling SCT initiation within the Eurozone.
In 2017, Singapore created a task force including government agencies such as the Monetary Authority of Singapore and Infocomm Media Development Authority to spearhead a system for e-payments using standardized QR code specifications. These specific dimensions are specialized for Singapore.[54]
The e-payment system, Singapore Quick Response Code (SGQR), essentially merges various QR codes into one label that can be used by both parties in the payment system. This allows for various banking apps to facilitate payments between multiple customers and a merchant that displays a single QR code. The SGQR scheme is co-owned by MAS and IMDA.[55] A single SGQR label contains e-payments and combines multiple payment options. People making purchases can scan the code and see which payment options the merchant accepts.[55]
Website login
[edit]QR codes can be used to log into websites: a QR code is shown on the login page on a computer screen, and when a registered user scans it with a verified smartphone, they will automatically be logged in. Authentication is performed by the smartphone, which contacts the server. Google deployed such a login scheme in 2012.[56]
Mobile ticket
[edit]There is a system whereby a QR code can be displayed on a device such as a smartphone and used as an admission ticket.[57][58] Its use is common for J1 League and Nippon Professional Baseball tickets in Japan.[59][60] In some cases, rights can be transferred via the Internet. In Latvia, QR codes can be scanned in Riga public transport to validate Rīgas Satiksme e-tickets.[61]

Restaurant ordering
[edit]Restaurants can present a QR code near the front door or at the table allowing guests to view an online menu, or even redirect them to an online ordering website or app, allowing them to order or possibly pay for their meal without having to use a cashier or waiter. QR codes can also link to daily or weekly specials that are not printed on the standardized menus,[62] and enable the establishment to update the entire menu without needing to print copies. At table-serve restaurants, QR codes enable guests to order and pay for their meals without a waiter involved – the QR code contains the table number so servers know where to bring the food.[63] This application has grown especially since the need for social distancing during the 2020 COVID-19 pandemic prompted reduced contact between service staff and customers.[63]
Joining a Wi‑Fi network
[edit]
By specifying the SSID, encryption type, password/passphrase, and if the SSID is hidden or not, mobile device users can quickly scan and join networks without having to manually enter the data.[64] A MeCard-like format is supported by Android and iOS 11+.[65]
- Common format:
WIFI:S:<SSID>;T:<WEP|WPA|nopass>;P:<PASSWORD>;H:<true|false|blank>;; - Sample:
WIFI:S:MySSID;T:WPA;P:MyPassW0rd;;
Funerary use
[edit]
A QR code can link to an obituary and can be placed on a headstone. In 2008, Ishinokoe in Yamanashi Prefecture, Japan began to sell tombstones with QR codes produced by IT DeSign, where the code leads to a virtual grave site of the deceased.[66][67][68] Other companies, such as Wisconsin-based Interactive Headstones, have also begun implementing QR codes into tombstones.[69] In 2014, the Jewish Cemetery of La Paz in Uruguay began implementing QR codes for tombstones.[70]
Electronic authentication
[edit]QR codes can be used to generate time-based one-time passwords for electronic authentication.
Loyalty programs
[edit]QR codes have been used by various retail outlets that have loyalty programs. Sometimes these programs are accessed with an app that is loaded onto a phone and includes a process triggered by a QR code scan. The QR codes for loyalty programs tend to be found printed on the receipt for a purchase or on the products themselves. Users in these schemes collect award points by scanning a code.
Counterfeit detection
[edit]Serialised QR codes have been used by brands[71] and governments[72] to let consumers, retailers and distributors verify the authenticity of the products and help with detecting counterfeit products, as part of a brand protection program.[73] However, the security level of a regular QR code is limited since QR codes printed on original products are easily reproduced on fake products, even though the analysis of data generated as a result of QR code scanning can be used to detect counterfeiting and illicit activity.[74] A higher security level can be attained by embedding a digital watermark or copy detection pattern into the image of the QR code. This makes the QR code more secure against counterfeiting attempts; products that display a code which is counterfeit, although valid as a QR code, can be detected by scanning the secure QR code with the appropriate app.[75]
The treaty regulating apostilles (documents bearing a seal of authenticity), has been updated to allow the issuance of digital apostilles by countries; a digital apostille is a PDF document with a cryptographic signature containing a QR code for a canonical URL of the original document, allowing users to verify the apostille from a printed version of the document.
Product tracing
[edit]Different studies have been conducted to assess the effectiveness of QR codes as a means of conveying labelling information and their use as part of a food traceability system. In a field experiment, it was found that when provided free access to a smartphone with a QR code scanning app, 52.6% of participants would use it to access labelling information.[76] A study made in South Korea showed that consumers appreciate QR code used in food traceability system, as they provide detailed information about food, as well as information that helps them in their purchasing decision.[77] If QR codes are serialised, consumers can access a web page showing the supply chain for each ingredient, as well as information specific to each related batch, including meat processors and manufacturers, which helps address the concerns they have about the origin of their food.[78]
COVID-19 pandemic
[edit]
After the COVID-19 pandemic began spreading, QR codes began to be used as a "touchless" system to display information, show menus, or provide updated consumer information, especially in the hospitality industry. Restaurants replaced paper or laminated plastic menus with QR code decals on the table, which opened an online version of the menu. This prevented the need to dispose of single-use paper menus, or institute cleaning and sanitizing procedures for permanent menus after each use.[79] Local television stations have also begun to utilize codes on local newscasts to allow viewers quicker access to stories or information involving the pandemic, including testing and immunization scheduling websites, or for links within stories mentioned in the newscasts overall.
In Australia, patrons were required to scan QR codes at shops, clubs, supermarkets, and other service and retail establishments on entry to assist contact tracing. Singapore, Taiwan, the United Kingdom, and New Zealand used similar systems.[80]
QR codes are also present on COVID-19 vaccination certificates in places such as Canada and the EU (EU Digital COVID certificate), where they can be scanned to verify the information on the certificate.[81]
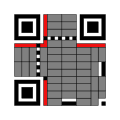
Design
[edit]Unlike the older, one-dimensional barcodes that were designed to be mechanically scanned by a narrow beam of light, a QR code is detected by a two-dimensional digital image sensor and then digitally analyzed by a programmed processor. The processor locates the three finder patterns, each consisting of three superimposed concentric squares of differing contrast at the upper left, upper right and lower left corners of the QR code image,[82] using a smaller square (or multiple squares) near the fourth corner to normalize the image for size, orientation, and angle of viewing. The small dots throughout the QR code are then converted to binary numbers and validated with an error-correcting algorithm.
Information capacity
[edit]The amount of data that can be represented by a QR code symbol depends on the data type (mode, or input character set), version (1, ..., 40, indicating the overall dimensions of the symbol, i.e. 4 × version number + 17 dots on each side), and error correction level. The maximum storage capacities occur for version 40 and error correction level L (low), denoted by 40-L:[16][83]
| Input mode | Max. characters | Bits/char. | Possible characters, default encoding |
|---|---|---|---|
| Numeric only | 7,089 | 31⁄3 | 0, 1, 2, 3, 4, 5, 6, 7, 8, 9 |
| Alphanumeric | 4,296 | 51⁄2 | 0–9, A–Z (upper-case only), space, $, %, *, +, -, ., /, : |
| Binary/byte | 2,953 | 8 | ISO/IEC 8859-1 |
| Kanji/kana | 1,817 | 13 | Shift JIS X 0208 |
Here are some samples of QR codes:
-
Version 1 (21×21). Content: "Ver1"
-
Version 2 (25×25). Content: "Version 2"
-
Version 3 (29×29). Content: "Version 3 QR Code"
-
Version 4 (33×33). Content: "Version 4 QR Code, up to 50 char"
-
Version 10 (57×57). Content: "VERSION 10 QR CODE, UP TO 174 CHAR AT H LEVEL, WITH 57X57 MODULES AND PLENTY OF ERROR CORRECTION TO GO AROUND. NOTE THAT THERE ARE ADDITIONAL TRACKING BOXES" (actually encoded in all capital letters). (Tracking boxes are more commonly called alignment patterns.)
-
Version 25 (117×117). Content: 1,269 characters of ASCII text describing QR codes
-
Version 40 (177×177). Content: "Version 40 QR Code can contain up to 1852 chars ..." (and followed by four paragraphs of ASCII text describing QR codes). The text refers to a QR Code with a "Level H" error correction. Other levels provide higher capacity.
Error correction
[edit]

QR codes use Reed–Solomon error correction over the finite field or GF(28), the elements of which are encoded as bytes of 8 bits; the byte with a standard numerical value encodes the field element where is taken to be a primitive element satisfying . The primitive polynomial is , corresponding to the polynomial number 285, with initial root = 0 to obtain generator polynomials.
The Reed–Solomon code uses one of 37 different polynomials over , with degrees ranging from 7 to 68, depending on how many error correction bytes the code adds. It is implied by the form of Reed–Solomon used (systematic BCH view) that these polynomials are all on the form . However, the rules for selecting the degree are specific to the QR standard.
For example, the generator polynomial used for the Version 1 QR code (21×21), when 7 error correction bytes are used, is: .
This is obtained by multiplying the first seven terms: .
The same may also be expressed using decimal coefficients (over ), as: .
The highest power of in the polynomial (the degree , of the polynomial) determines the number of error correction bytes. In this case, the degree is 7.
When discussing the Reed–Solomon code phase there is some risk for confusion, in that the QR ISO/IEC standard uses the term codeword for the elements of , which with respect to the Reed–Solomon code are symbols, whereas it uses the term block for what with respect to the Reed–Solomon code are the codewords. The number of data versus error correction bytes within each block depends on (i) the version (side length) of the QR symbol and (ii) the error correction level, of which there are four. The higher the error correction level, the less the storage capacity. The following table lists the approximate error correction capability at each of the four levels:
| Level L (Low) | 7% of data bytes can be restored. |
| Level M (Medium) | 15% of data bytes can be restored. |
| Level Q (Quartile)[84] | 25% of data bytes can be restored. |
| Level H (High) | 30% of data bytes can be restored. |
In larger QR symbols, the message is broken up into several Reed–Solomon code blocks. The block size is chosen so that no attempt is made at correcting more than 15 errors per block; this limits the complexity of the decoding algorithm. The code blocks are then interleaved together, making it less likely that localized damage to a QR symbol will overwhelm the capacity of any single block.
The Version 1 QR symbol with level L error correction, for example, consists of a single error correction block with a total of 26 code bytes (made of 19 message bytes and seven error correction bytes). It can correct up to 2 byte errors. Hence, this code is known as a (26,19,2) error correction code over GF(28) . It is also sometimes represented in short, as a (26,19) code.
Due to error correction, it is possible to create artistic QR codes with embellishments to make them more readable or attractive to the human eye, and to incorporate colors, logos, and other features into the QR code block; the embellishments are treated as errors, but the codes still scan correctly.[85][86]
It is also possible to design artistic QR codes without reducing the error correction capacity by manipulating the underlying mathematical constructs.[87][88] Image processing algorithms are also used to reduce errors in QR-code.[89]
Encoding
[edit]Format information and masking
[edit]The format information records two things: the error correction level and the mask pattern used for the symbol. Masking is used to break up patterns in the data area that might confuse a scanner, such as large blank areas or misleading features that look like the locator marks. The mask patterns are defined on a grid that is repeated as necessary to cover the whole symbol. Modules corresponding to the dark areas of the mask are inverted. The 5-bit format information is protected from errors with a BCH code, and two complete copies are included in each QR symbol.[4] A (15,5) triple error-correcting BCH code over GF(24) is used, having the generator polynomial . It can correct at most 3 bit-errors out of the 5 data bits. There are a total of 15 bits in this BCH code (10 bits are added for error correction). This 15-bit code is itself X-ORed with a fixed 15-bit mask pattern (101010000010010) to prevent an all-zero string.
Error correction bytes
[edit]To obtain the error correction (EC) bytes for a message "www.wikipedia.org", the following procedure may be carried out:
The message is 17 bytes long, hence it can be encoded using a (26,19,2) Reed-Solomon code to fit in a Ver1 (21×21) symbol, which has a maximum capacity of 19 bytes (for L level error correction).
The generator polynomial specified for the (26,19,2) code, is: , which may also be written in the form of a matrix of decimal coefficients:
[1 127 122 154 164 11 68 117]
The 17-byte long message "www.wikipedia.org" as hexadecimal coefficients (ASCII values), denoted by M1 through M17 is:
[77 77 77 2E 77 69 6B 69 70 65 64 69 61 2E 6F 72 67]
The encoding mode is "Byte encoding". Hence the 'Enc' field is [0100] (4 bits). The length of the above message is 17 bytes hence 'Len' field is [00010001] (8 bits). The 'End' field is End of message marker [0000] (4 bits).
The message code word (without EC bytes) is of the form:
['Enc' 'Len' w w w . w i k i p e d i a . o r g 'End']
Substituting the hexadecimal values, it can be expressed as:
[4 11 77 77 77 2E 77 69 6B 69 70 65 64 69 61 2E 6F 72 67 0]
This is rearranged as 19-byte blocks of 8 bits each:
[41 17 77 77 72 E7 76 96 B6 97 06 56 46 96 12 E6 F7 26 70]
Using the procedure for Reed-Solomon systematic encoding, the 7 EC bytes obtained (E1 through E7, as shown in the symbol) which are the coefficients (in decimal) of the remainder after polynomial division are:
[174 173 239 6 151 143 37]
or in hexadecimal values:
[AE AD EF 06 97 8F 25]
These 7 EC bytes are then appended to the 19-byte message. The resulting coded message has 26 bytes (in hexadecimal):
[41 17 77 77 72 E7 76 96 B6 97 06 56 46 96 12 E6 F7 26 70 AE AD EF 06 97 8F 25]
Note: The bit values shown in the Ver1 QR symbol below do not match with the above values, as the symbol has been masked using a mask pattern (001).
Message placement
[edit]The message dataset is placed from right to left in a zigzag pattern, as shown below. In larger symbols, this is complicated by the presence of the alignment patterns and the use of multiple interleaved error-correction blocks.
-
Meaning of format information. In the above figure, the format information is protected by a (15,5) BCH code, which can correct up to 3 bit errors. The total length of the code is 15 bits, of which 5 are data bits (2 EC level + 3 mask pattern) and 10 are extra bits for error correction. The format mask pattern for these 15 bits is: [101010000010010]. Note that we map the masked values directly to its meaning here, in contrast to image 4 "Levels & Masks" where the mask pattern numbers are the result of putting the 3rd to 5th mask bit, [101], over the 3rd to 5th format info bit of the QR code.
-
Message placement within a Ver 1 QR symbol (21×21). The message is encoded using a (255,248) Reed Solomon code (shortened to (26,19) code by using "padding") that can correct up to 2 byte-errors. A total of 26 code-words consist of 7 error-correction bytes, and 17 data bytes, in addition to the "Len" (8 bit field), "Enc" (4 bit field), and "End" (4 bit field). The symbol is capable of level L error correction. The EC level is 01(L), and mask pattern is 001. Hence the first 5 bits of the format information are 01001 (without the format mask). After masking, the 5 bits become 11100, as seen here.
-
Larger symbol (Ver 3, 29×29) illustrating interleaved blocks. The message has 26 data bytes and is encoded using two Reed-Solomon code blocks. Each block is a (255,233) Reed Solomon code (shortened to (35,13) code), which can correct up to 11 byte-errors in a single burst, containing 13 data bytes and 22 "parity" bytes appended to the data bytes. The two 35-byte Reed-Solomon code blocks are interleaved (resulting in a total of 70 code bytes), so it can correct up to 22 byte-errors. The symbol achieves level H error correction.
The general structure of a QR encoding is as a sequence of 4 bit indicators with payload length dependent on the indicator mode (e.g. byte encoding payload length is dependent on the first byte).[90]
| Mode indicator | Description | Typical structure '[ type : sizes in bits ]' |
|---|---|---|
| 1 = 0b0001 | Numeric | [0001 : 4] [ Character Count Indicator : variable ] [ Data Bit Stream : 31⁄3 × charcount ] |
| 2 = 0b0010 | Alphanumeric | [0010 : 4] [ Character Count Indicator : variable ] [ Data Bit Stream : 51⁄2 × charcount ] |
| 4 = 0b0100 | Byte encoding | [0100 : 4] [ Character Count Indicator : variable ] [ Data Bit Stream : 8 × charcount ] |
| 8 = 0b1000 | Kanji encoding | [1000 : 4] [ Character Count Indicator : variable ] [ Data Bit Stream : 13 × charcount ] |
| 3 = 0b0011 | Structured append | [0011 : 4] [ Symbol Position : 4 ] [ Total Symbols: 4 ] [ Parity : 8 ] |
| 7 = 0b0111 | ECI | [0111 : 4] [ ECI Assignment number : variable ] |
| 5 = 0b0101 | FNC1 in first position | [0101 : 4] [ Numeric/Alphanumeric/Byte/Kanji payload : variable ] |
| 9 = 0b1001 | FNC1 in second position | [1001 : 4] [ Application Indicator : 8 ] [ Numeric/Alphanumeric/Byte/Kanji payload : variable ] |
| 0 = 0b0000 | End of message | [0000 : 4] |
- Note:
- Character Count Indicator depends on how many modules are in a QR code (Symbol Version).
- ECI Assignment number Size:
- 8 × 1 bits if ECI Assignment Bitstream starts with '0'
- 8 × 2 bits if ECI Assignment Bitstream starts with '10'
- 8 × 3 bits if ECI Assignment Bitstream starts with '110'
Four-bit indicators are used to select the encoding mode and convey other information.
| Indicator | Meaning |
|---|---|
| 0001 | Numeric encoding (10 bits per 3 digits) |
| 0010 | Alphanumeric encoding (11 bits per 2 characters) |
| 0100 | Byte encoding (8 bits per character) |
| 1000 | Kanji encoding (13 bits per character) |
| 0011 | Structured append (used to split a message across multiple QR symbols) |
| 0111 | Extended Channel Interpretation (select alternate character set or encoding) |
| 0101 | FNC1 in first position (see Code 128 for more information) |
| 1001 | FNC1 in second position |
| 0000 | End of message (Terminator) |
Encoding modes can be mixed as needed within a QR symbol. (e.g., a url with a long string of alphanumeric characters )
[ Mode Indicator][ Mode bitstream ] --> [ Mode Indicator][ Mode bitstream ] --> etc... --> [ 0000 End of message (Terminator) ]
After every indicator that selects an encoding mode is a length field that tells how many characters are encoded in that mode. The number of bits in the length field depends on the encoding and the symbol version.
| Encoding | Ver. 1–9 | 10–26 | 27–40 |
|---|---|---|---|
| Numeric | 10 | 12 | 14 |
| Alphanumeric | 9 | 11 | 13 |
| Byte | 8 | 16 | 16 |
| Kanji | 8 | 10 | 12 |
Alphanumeric encoding mode stores a message more compactly than the byte mode can, but cannot store lower-case letters and has only a limited selection of punctuation marks, which are sufficient for rudimentary web addresses. Two characters are coded in an 11-bit value by this formula:
- V = 45 × C1 + C2
This has the exception that the last character in an alphanumeric string with an odd length is read as a 6-bit value instead.
| Code | Character | Code | Character | Code | Character | Code | Character | Code | Character |
|---|---|---|---|---|---|---|---|---|---|
| 00 | 0 | 09 | 9 | 18 | I | 27 | R | 36 | Space |
| 01 | 1 | 10 | A | 19 | J | 28 | S | 37 | $ |
| 02 | 2 | 11 | B | 20 | K | 29 | T | 38 | % |
| 03 | 3 | 12 | C | 21 | L | 30 | U | 39 | * |
| 04 | 4 | 13 | D | 22 | M | 31 | V | 40 | + |
| 05 | 5 | 14 | E | 23 | N | 32 | W | 41 | - |
| 06 | 6 | 15 | F | 24 | O | 33 | X | 42 | . |
| 07 | 7 | 16 | G | 25 | P | 34 | Y | 43 | / |
| 08 | 8 | 17 | H | 26 | Q | 35 | Z | 44 | : |
Decoding example
[edit]The following images offer more information about the QR code.
-
1 – Introduction
-
2 – Structure
-
3 – Layout & Encoding
-
4 – Levels & Masks
-
5 – Protocols
Variants
[edit]Model 1
[edit]Model 1 QR code is an older version of the specification. It is visually similar to the widely seen model 2 codes, but lacks alignment patterns. Differences are in the bottom right corner, and in the midsections of the bottom and right edges are additional functional regions.
-
Model 1 QR code example
-
Model 1 QR code functional regions
Micro QR code
[edit]Micro QR code is a smaller version of the QR code standard for applications where symbol size is limited. There are four different versions (sizes) of Micro QR codes: the smallest is 11×11 modules; the largest can hold 35 numeric characters,[91] or 21 ASCII alphanumeric characters, or 15 bytes (120 bits).
-
Micro QR code example
-
Micro QR code functional regions
Rectangular Micro QR Code
[edit]Rectangular Micro QR Code (also known as rMQR Code) is a two-dimensional (2D) matrix barcode invented and standardized in 2022 by Denso Wave as ISO/IEC 23941. rMQR Code is designed as a rectangular variation of the QR code and has the same parameters and applications as original QR codes; however, rMQR Code is more suitable for rectangular areas, and has a difference between width and height up to 19 in the R7x139 version.
-
Rectangular Micro QR Code (rMQR Code) example
iQR code
[edit]iQR code is an alternative to existing square QR codes developed by Denso Wave. iQR codes can be created in square or rectangular formations; this is intended for situations where a longer and narrower rectangular shape is more suitable, such as on cylindrical objects. iQR codes can fit the same amount of information in 30% less space. There are 61 versions of square iQR codes, and 15 versions of rectangular codes. For squares, the minimum size is 9 × 9 modules; rectangles have a minimum of 19 × 5 modules. iQR codes add error correction level S, which allows for 50% error correction.[92] iQR Codes had not been given an ISO/IEC specification as of 2015, and only proprietary Denso Wave products could create or read iQR codes.[93]
-
iQR code example
Secure QR code
[edit]Secure Quick Response Code (SQRC) is a QR code that contains a "private data" segment after the terminator instead of the specified filler bytes "ec 11".[94] This private data segment must be deciphered with an encryption key. This can be used to store private information and to manage a company's internal information.[95]
Frame QR
[edit]Frame QR is a variant of the QR code standard which arranges the code in a frame around a central empty area. It is intended to be used in applications where an image, artwork, or branding is desired to be part of the code. It is a completely separate variant and is unrelated to the use of the standard QR code's error correction to insert artwork. As a variant, some QR code readers are unable to read Frame QR.[96]
-
Frame QR example
-
Frame QR code example with a circular frame and the Wikipedia logo composed into its interior
HCC2D
[edit]Researchers have proposed a new High Capacity Colored 2-Dimensional (HCC2D) Code, which builds upon a QR code basis for preserving the QR robustness to distortions and uses colors for increasing data density (as of 2014 it is still in the prototyping phase). The HCC2D code specification is described in details in Querini et al. (2011),[97] while techniques for color classification of HCC2D code cells are described in detail in Querini and Italiano (2014),[98] which is an extended version of Querini and Italiano (2013).[99]
Introducing colors into QR codes requires addressing additional issues. In particular, during QR code reading only the brightness information is taken into account, while HCC2D codes have to cope with chromatic distortions during the decoding phase. In order to ensure adaptation to chromatic distortions that arise in each scanned code, HCC2D codes make use of an additional field: the Color Palette Pattern. This is because color cells of a Color Palette Pattern are supposed to be distorted in the same way as color cells of the Encoding Region. Replicated color palettes are used for training machine-learning classifiers.
-
HCC2D code examples: (a) 4-color HCC2D code and (b) 8-color HCC2D code
Accessible QR (AQR)
[edit]Accessible QR (AQR) is a type of QR code that combines a standard QR code with a dot-dash pattern positioned around one corner of the code to provide product information for people who are blind and partially sighted. The codes, announce product categories and product details such as instructions, ingredients, safety warnings, and recycling information. The data is structured for the needs of users who are blind or partially sighted and offers larger text or audio output. It can read QR codes from a metre away, activating the smartphone's accessibility features like VoiceOver to announce product details.
tQR
[edit]tQR (also known as tQR code) is a QR code specially designed for rail transport to distinguish between the different opening and closing positions of platform screen doors, which vary depending on rolling stock.[100] The initial "t" stands for "toughness" and "train".[101] It has an outer frame, and its main feature is that it can be restored even if up to 50% of data bytes is missing.[100] It was jointly developed by Denso Wave and the Tokyo Metropolitan Bureau of Transportation.[100][102] It is stuck to the outside of the doors of rolling stock and stores the train composition number and the car number. The tQR reader installed on the platform detects the position of tQR, which allows it to detect the opening and closing of doors and the movement of rolling stock. If it is easily readable, it could be exploited for mischiefs, so it is not compatible with existing QR codes and cannot be read by standard cameras on smartphones or other devices.[103]
-
tQR stuck to the door of rolling stock
License
[edit]The use of QR code technology is freely licensed as long as users follow the standards for QR code documented with JIS or ISO/IEC. Non-standardized codes may require special licensing.[104]
Denso Wave owns a number of patents on QR code technology, but has chosen to exercise them in a limited fashion.[104] In order to promote widespread usage of the technology Denso Wave chose to waive its rights to a key patent in its possession for standardized codes only.[17] In the US, the granted QR code patent, 5726435, expired on March 14, 2015. In Japan, the corresponding patent, 2938338, expired on March 14, 2014. The European Patent Office granted patent 0672994 to Denso Wave, which was then validated into French, UK, and German patents, all of which expired in March 2015.[105]
The text QR Code itself is a registered trademark and wordmark of Denso Wave Incorporated.[106] In UK, the trademark is registered as E921775, the term QR Code, with a filing date of 3 September 1998.[107] The UK version of the trademark is based on the Kabushiki Kaisha Denso (DENSO CORPORATION) trademark, filed as Trademark 000921775, the term QR Code, on 3 September 1998 and registered on 16 December 1999 with the European Union OHIM (Office for Harmonization in the Internal Market).[108] The U.S. Trademark for the term QR Code is Trademark 2435991 and was filed on 29 September 1998 with an amended registration date of 13 March 2001, assigned to Denso Corporation.[109] In South Korea, trademark application filed on 18 November 2011 was refused on 20 March 2012, because the Korean Intellectual Property Office viewed that the phrase was genericized among South Korean people to refer to matrix barcodes in general.[110]
Risks
[edit]The only context in which common QR codes can carry executable data is the URL data type. These URLs may host JavaScript code, which can be used to exploit vulnerabilities in applications on the host system, such as the reader, the web browser, or the image viewer, since a reader will typically send the data to the application associated with the data type used by the QR code.
In the case of no software exploits, malicious QR codes combined with a permissive reader can still put a computer's contents and user's privacy at risk. This practice is known as "attagging", a portmanteau of "attack tagging".[111] They are easily created and can be affixed over legitimate QR codes.[112][failed verification][113] On a smartphone, the reader's permissions may allow use of the camera, full Internet access, read/write contact data, GPS, read browser history, read/write local storage, and global system changes.[114][115][116][improper synthesis?]
Risks include linking to dangerous web sites with browser exploits, enabling the microphone/camera/GPS, and then streaming those feeds to a remote server, analysis of sensitive data (passwords, files, contacts, transactions),[117] and sending email/SMS/IM messages or packets for DDoS as part of a botnet, corrupting privacy settings, stealing identity,[118] and even containing malicious logic themselves such as JavaScript[119] or a virus.[120][121] These actions could occur in the background while the user is only seeing the reader opening a seemingly harmless web page.[122] In Russia, a malicious QR code caused phones that scanned it to send premium texts at a fee of $6 each.[111] QR codes have also been linked to scams in which stickers are placed on parking meters and other devices, posing as quick payment options, as seen in Austin, San Antonio and Boston, among other cities across the United States and Australia.[123][124][125]
See also
[edit]References
[edit]- ^ Hara, Masahiro (1 October 2024). "I used to hate QR codes. But they're actually genius" (Interview). Interviewed by Muller, Derek. 34:09. Retrieved 1 October 2024.
The biggest feature of QR codes is that they can be read quickly. It's called Quick Response because it reacts quickly.
- ^ Hung, Shih-Hsuan; Yao, Chih-Yuan; Fang, Yu-Jen; Tan, Ping; Lee, RuenRone; Sheffer, Alla; Chu, Hung-Kuo (1 September 2020). "Micrography QR Codes". IEEE Transactions on Visualization and Computer Graphics. 26 (9): 2834–2847. Bibcode:2020ITVCG..26.2834H. doi:10.1109/TVCG.2019.2896895. ISSN 1077-2626. PMID 30716038. S2CID 73433883.
- ^ Chen, Rongjun; Yu, Yongxing; Xu, Xiansheng; Wang, Leijun; Zhao, Huimin; Tan, Hong-Zhou (11 December 2019). "Adaptive Binarization of QR Code Images for Fast Automatic Sorting in Warehouse Systems". Sensors. 19 (24): 5466. Bibcode:2019Senso..19.5466C. doi:10.3390/s19245466. PMC 6960674. PMID 31835866.
- ^ a b c "QR Code Essentials". Denso ADC. 2011. Archived from the original on 12 May 2013. Retrieved 12 March 2013.
- ^ "QR Code features". Denso-Wave. Archived from the original on 29 January 2013. Retrieved 3 October 2011.
- ^ a b c "QRコード開発|テクノロジー|デンソーウェーブ" [QR code development]. Denso Wave (in Japanese). Archived from the original on 26 October 2021. Retrieved 26 October 2021.
- ^ "2D Barcodes". NHK World-Japan. 26 March 2020. Archived from the original on 7 April 2020. Retrieved 7 April 2020.
- ^ "From Japanese Auto Parts to Ubiquity: A Look at the History of QR Codes". Mainichi Daily News. 9 November 2021. Archived from the original on 11 November 2021. Retrieved 11 November 2021.
- ^ "The Little-Known Story of the Birth of the QR Code". 10 February 2020. Archived from the original on 4 March 2020.
- ^ a b "History of QR Code". Denso Wave. Retrieved 30 April 2023.
- ^ a b Furht, Borko (2011). Handbook of Augmented Reality. Springer. p. 341. ISBN 9781461400646. Archived from the original on 21 December 2016.
- ^ "14m Americans scanned QR and bar codes with their mobiles in June 2011". 16 August 2011. Archived from the original on 5 April 2016. Retrieved 27 May 2016.
- ^ "Mobile QR scanner usage in the U.S. 2025". Statista. Retrieved 24 December 2023.
- ^ "U.S. and UK increase of QR code use 2020". 6 July 2021. Archived from the original on 14 August 2021. Retrieved 13 August 2021.
- ^ Waters, Joe. "How to Use the Top QR Code Generators". Dummies.com. Archived from the original on 11 September 2017. Retrieved 5 June 2017.
- ^ a b "QR Code—About 2D Code". Denso-Wave. Archived from the original on 5 June 2016. Retrieved 27 May 2016.
- ^ a b "QR Code Standardization". QR Code.com. Denso-Wave. Archived from the original on 10 May 2016. Retrieved 23 May 2016.
- ^ "ISS QR Code|AIM Store: Historical Archive". Aimglobal.org. Archived from the original on 8 August 2016. Retrieved 26 May 2016.
- ^ "ISO/IEC 18004:2006 - Information technology – Automatic identification and data capture techniques – QR Code 2005 bar code symbology specification". ISO. 5 February 2009. Archived from the original on 8 March 2017. Retrieved 7 March 2017.
- ^ "ISO/IEC 18004:2024". International Organization for Standardization. Retrieved 1 April 2025.
- ^ "ISO/IEC 23941:2022 Information technology — Automatic identification and data capture techniques — Rectangular Micro QR Code (rMQR) bar code symbology specification". ISO. Archived from the original on 3 January 2023. Retrieved 3 January 2023.
- ^ "Synchronization with Native Applications". NTT DoCoMo. Archived from the original on 6 August 2016. Retrieved 26 May 2016.
- ^ Sean Owen (17 January 2014). "Barcode contents". GitHub. Archived from the original on 15 February 2016. Retrieved 26 May 2016.
- ^ Rimma Kats (23 January 2012). "Starbucks promotes coffee blend via QR codes". Archived from the original on 3 June 2016. Retrieved 26 May 2016.
- ^ Jenny Lee (4 January 2012). "Tesco's cool QR code advertising campaign". Vancouversun. Archived from the original on 3 June 2016. Retrieved 26 May 2016.
- ^ "Getting Started with Infographics (deprecated)". google-developers.appspot.com. 26 May 2015. Archived from the original on 29 June 2016. Retrieved 27 May 2016.
- ^ "QR Code Readers for iPhone, Android, Blackberry and Windows Phone 7". 7 December 2010. Archived from the original on 25 August 2011.
- ^ "QR codes on China's train tickets may leak personal information". Want China Times. Archived from the original on 12 December 2013. Retrieved 16 March 2013.
- ^ Novak, Asami (23 March 2008). "Japanese Gravestones Memorialize the Dead With QR Codes". Wired. Archived from the original on 15 February 2013. Retrieved 8 May 2013.
- ^ Skepticality (16 August 2011). "Paranormality: Why we see what isn't there". theguardian.com. Retrieved 13 September 2025.
- ^ "Field codes: DisplayBarcode". Microsoft Support. Retrieved 22 April 2023.
- ^ "LibreOffice 6.4: Release Notes". The Document Foundation Wiki. Retrieved 22 April 2023.
- ^ "Herdenkingsmunt met QR code volop in het nieuws!" [Commemorative QR code in the news!]. Koninklijke Nederlandse Munt (in Dutch). 21 June 2011. Archived from the original on 29 June 2016. Retrieved 27 May 2016.
- ^ "New ₦100 Commemorative Centenary Celebration". Archived from the original on 8 September 2015. Retrieved 10 September 2015.
- ^ "Russia Marks Crimea Annexation With A Banknote Rapidly Losing Value". NPR. 23 December 2015. Archived from the original on 23 December 2015. Retrieved 20 June 2024.
- ^ "With IndiaQR launch, retail payments to get digital edge". ET Retail. Archived from the original on 15 February 2017. Retrieved 15 February 2017.
- ^ "IndiaQR to debut on Feb 20". The Times of India. Archived from the original on 16 February 2017. Retrieved 15 February 2017.
- ^ "Apple hid a QR Code scanner in iOS 11 — here's how to use it". CNET. Retrieved 1 October 2024.
- ^ Lopez, Napier (7 June 2017). "iOS 11 makes QR codes cool again". TNW | Apple. Retrieved 1 October 2024.
- ^ Lacoma, Tyler (3 October 2018). "How to Scan a QR Code". Digital Trends. Archived from the original on 22 April 2019. Retrieved 28 May 2019.
- ^ "Tesco QR Code Virtual Store". 14 April 2012. Archived from the original on 25 May 2016. Retrieved 26 May 2016.
- ^ Sebastián Campanario (16 September 2011). "Marketing futurista: ya se puede comprar con la cámara del celular" [Futuristic marketing: it's already possible to purchase with a cellphone's camera]. Clarin.com (in Spanish). Archived from the original on 23 September 2011.
- ^ "Marketers scatter phone-friendly codes across ads". 11 November 2010. Archived from the original on 12 January 2023. Retrieved 26 May 2016.
- ^ "Top 10 QR Code Store examples". 14 April 2012. Archived from the original on 6 June 2016. Retrieved 26 May 2016.
- ^ "SCVNGR Unveils QR Code Payment System". Mashable. 12 October 2011. Archived from the original on 8 December 2012.
- ^ Kim, Ryan (26 January 2012). "MasterCard starts piloting QkR mobile payment app". Gigaom. Archived from the original on 8 January 2014.
- ^ Jacobs, Harrison. "One photo shows that China is already in a cashless future". Business Insider. Archived from the original on 5 May 2019. Retrieved 14 October 2019.
- ^ Mozur, Paul (16 July 2017). "In Urban China, Cash Is Rapidly Becoming Obsolete". The New York Times. ISSN 0362-4331. Archived from the original on 21 October 2019. Retrieved 14 October 2019.
- ^ "Paying With Your Mobile Wallet To Get Simpler With Interoperable QR Codes". Moneycontrol. 28 October 2020. Archived from the original on 1 November 2020. Retrieved 22 December 2020.
- ^ "A Hangzhou Story: The Development of China's Mobile Payment Revolution" (PDF). Archived (PDF) from the original on 26 June 2020. Retrieved 23 June 2020.
- ^ "Payment methods in China: How China became a mobile-first nation". Daxue Consulting. Archived from the original on 29 June 2020. Retrieved 23 June 2020.
- ^ "Standard - Formát pro sdílení platebních údajů v rámci tuzemského platebního styku v CZK prostřednictvím QR kódů" [Standard No. 26: Format for exchanging payment information for domestic payments in CZK using QR codes] (in Czech). Czech Banking Association. November 2012. Archived from the original on 3 June 2016. Retrieved 27 May 2016.
- ^ "Formát pro sdílení platebních údajů v CZK - QR kódy" [Format for exchanging payment information in CZK - QR codes] (in Czech). Czech Banking Association. August 2015. Archived from the original on 2020-02-16. Retrieved 2020-02-17.
- ^ IMDA (9 November 2022). "Annex A – Fact sheet on Singapore Quick Response Code (SGQR)" (PDF). Archived (PDF) from the original on 5 December 2022. Retrieved 10 November 2022.
- ^ a b Monetary Authority of Singapore (9 November 2022). "Singapore Quick Response Code (SGQR)". Archived from the original on 26 July 2022. Retrieved 10 November 2022.
- ^ Naraine, Ryan (17 January 2012). "Google testing login authentication via QR codes". ZDNet. Archived from the original on 15 June 2013.
- ^ "【公式】チケットの使い方 東京ディズニーリゾート" (in Japanese). Archived from the original on 20 October 2022. Retrieved 20 October 2022.
- ^ "ダイレクトイン(QRコード)の使い方|USJ WEBチケットストア". USJ (in Japanese). Archived from the original on 20 October 2022. Retrieved 20 October 2022.
- ^ "QRチケットレス入場について". サンフレッチェ広島 オフィシャルサイト (in Japanese). 6 June 2025.
- ^ "スマートスタジアム". 東北楽天ゴールデンイーグルス (in Japanese). Archived from the original on 20 October 2022. Retrieved 20 October 2022.
- ^ "New Riga public transport tickets are on sale now | Rīgas valstspilsētas pašvaldība". riga.lv. Retrieved 13 September 2023.
- ^ "The Business of Eating & Restaurant Management News". Modern Restaurant Management. 22 October 2020. Archived from the original on 1 November 2020. Retrieved 1 November 2020.
- ^ a b Kastrenakes, Jacob (29 September 2020). "Square launches QR codes that let you order from your table at a restaurant". Verge.com. VOX Media LLC. Archived from the original on 23 November 2020. Retrieved 24 November 2020.
- ^ Bhattacharjee, Mrinmay (19 July 2015). "Share your Wi-Fi SSID & Password using a QR Code". Technostarry. Archived from the original on 12 January 2023. Retrieved 6 January 2018.
- ^ "zxing documentation: barcode contents". GitHub. zxing. Archived from the original on 15 February 2016. Retrieved 26 May 2016.
- ^ "モノウォッチは生まれ変わります". Archived from the original on 13 November 2015. Retrieved 10 September 2015.
- ^ Michael Keferl (20 March 2008). "QR code graves give a "Memorial Window"". Japan Trends. Archived from the original on 2 May 2012.
- ^ "供養の窓 - 石の声 株式会社" (in Japanese). Archived from the original on 13 November 2015. Retrieved 10 September 2015.
- ^ "Quiring Monuments adds smartphone codes to gravestones". Puget Sound Business Journal. 26 April 2011. Archived from the original on 23 June 2015. Retrieved 10 September 2015.
- ^ "Uruguayan Jewish Cemetery QR-ified" (in Spanish). EL PAIS. 24 March 2014. Archived from the original on 3 August 2016.
- ^ "Exclusive - CHINA: Pernod Ricard to use QR codes on all China packaging". just-drinks.com. 17 September 2013. Retrieved 24 April 2020.
- ^ "Digital tax stamps will curb fake goods - URA". Daily Monitor. Archived from the original on 12 January 2023. Retrieved 24 April 2020.
- ^ "The power of smart packaging". bakingbusiness.com. Archived from the original on 12 January 2023. Retrieved 3 May 2020.
- ^ Baldini, Gianmarco; Nai Fovino, Igor; Satta, Riccardo; Tsois, Aris; Checchi, Enrico (2015). Survey of techniques for the fight against counterfeit goods and Intellectual Property Rights (IPR) infringement. Luxembourg: European Commission. Joint Research Centre, Publications Office. pp. 28, 89–92. ISBN 978-92-79-54543-6. OCLC 948769705.
- ^ Carron, Cecilia (6 May 2015). "Combatting counterfeiting using QR codes". phys.org. Archived from the original on 12 January 2023. Retrieved 16 June 2020.
- ^ Li, Tongzhe; Messer, Kent D.; Li, Tongzhe; Messer, Kent D. (2019). Li, Tongzhe; Messer, Kent D. (eds.). "To Scan or Not to Scan: The Question of Consumer Behavior and QR Codes on Food Packages". Journal of Agricultural and Resource Economics. 44 (2): 311–327. doi:10.22004/ag.econ.287977. ISSN 1068-5502. Archived from the original on 1 November 2020. Retrieved 24 June 2020.
- ^ Kim, Yeong Gug; Woo, Eunju (1 July 2016). "Consumer acceptance of a quick response (QR) code for the food traceability system: Application of an extended technology acceptance model (TAM)". Food Research International. 85: 266–272. doi:10.1016/j.foodres.2016.05.002. ISSN 0963-9969. PMID 29544844.
- ^ "Behind Every Smart Product is Smart Packaging | Future Food Asia". futurefoodasia.com. Archived from the original on 21 June 2020. Retrieved 24 June 2020.
- ^ Leger, Benjamin (27 October 2020). "QR codes are replacing physical menus at restaurants". [225]. Archived from the original on 1 November 2020. Retrieved 1 November 2020.
- ^ Purtill, James (19 November 2020). "The proliferation of QR code check-ins is a 'dog's breakfast'. Is there a better way?". Australian Broadcasting Corporation. Archived from the original on 30 January 2021. Retrieved 15 January 2021.
- ^ Hristova, Bobby (28 December 2021). "Ontarians need QR code to prove vaccination next week. Here's what you need to know". Archived from the original on 31 December 2021. Retrieved 30 December 2021.
- ^ "ISO/IEC 18004:2024(en) - QR code bar code symbology specification". International Organization for Standardization. Archived from the original on 20 June 2025. Retrieved 22 June 2025.
- ^ "Information capacity and versions of QR Code". Denso-Wave. Archived from the original on 29 May 2016.
- ^ "2D Barcode: QR-Code". Archived from the original on 15 September 2012. — TEC-IT
- ^ Hamilton Chan (18 April 2011). "HOW TO: Make Your QR Codes More Beautiful". Mashable. Archived from the original on 10 July 2012. Retrieved 29 July 2011.
- ^ Orli Sharaby (18 October 2010). "Form Meets Function: Extreme Makeover QR Code Edition". Archived from the original on 8 July 2012. Retrieved 29 July 2011.
- ^ Russ Cox (12 April 2012). "QArt Codes: How to make pictures with QR codes, part II". Archived from the original on 21 March 2015. Retrieved 8 May 2015.
- ^ Russ Cox (12 April 2012). "QArt Coder". Archived from the original on 24 April 2015. Retrieved 8 May 2015.
- ^ Gupta, Kishor Datta; Ahsan, Md Manjurul; Andrei, Stefan (January 2018). "Extending the Storage Capacity And Noise Reduction of a Faster QR-Code". Brain Broad Research in Artificial Intelligence and Neuroscience. 9 (1): 59–71.
- ^ ISO/IEC 18004:2006(E) § 6.4 Data encoding; Table 3 – Number of bits in character count indicator for QR code 2005
- ^ Information technology – Automatic identification and data capture techniques – QR Code 2005 bar code symbology specification, ISO/IEC 18004:2006 cor. 2009, pages 3, 6.
- ^ "QR Code Overview & Progress of QR Code Applications" (PDF). Archived (PDF) from the original on 20 May 2013. Retrieved 26 June 2014.
- ^ "iQR Code – QRcode.com – DENSO WAVE". Archived from the original on 7 September 2015. Retrieved 10 September 2015.
- ^ "Embedding Secret Data in QR Code". Archived from the original on 30 October 2018. Retrieved 29 October 2018.
- ^ "SQRC". qrcode.com. Archived from the original on 1 January 2018. Retrieved 26 December 2017.
- ^ "Frame QR". qrcode.com. Archived from the original on 20 December 2017. Retrieved 26 December 2017.
- ^ Querini, M; Grillo, A; Lentini, A; Italiano, GF (2011). "2D Color Barcodes for Mobile Phones" (PDF). International Journal of Computer Science and Applications. 8 (1). Technomathematics Research Foundation: 136–155. Archived from the original (PDF) on 4 March 2016. Retrieved 21 December 2024.
- ^ Querini, Marco; Italiano, Giuseppi F (2014). "Reliability and Data Density in High Capacity Color Barcodes" (PDF). Computer Science and Information Systems. 11 (4): 1595–1615. doi:10.2298/CSIS131218054Q. Archived from the original (PDF) on 24 July 2015. Retrieved 21 December 2024.
- ^ Querini, Marco; Italiano, Giuseppi F (2013). "Color classifiers for 2D color barcodes" (PDF). Federated Conference on Computer Science and Information System. Archived from the original (PDF) on 24 July 2015.
- ^ a b c "地下鉄初!デンソーウェーブと東京都交通局が開発した 新型QRコードを用いたホームドア開閉制御システムが運用開始|お知らせ|DENSOWAVE". www.denso-wave.com (in Japanese). 3 October 2019. Archived from the original on 20 June 2025. Retrieved 10 October 2025.
- ^ 原戸, 晃; 荒井, 亮 (15 December 2023). "QRコード®️は行動変容の入り口に。知財のオープン・クローズ戦略が導くイノベーション". 知財図鑑 (in Japanese). Archived from the original on 14 August 2025. Retrieved 10 October 2025.
- ^ "独自の「QRコード」を編み出した理由を聞いてみると…ホームドア設置率100%を達成する都営地下鉄:東京新聞デジタル". 東京新聞デジタル (in Japanese). 21 December 2023. Archived from the original on 14 January 2025. Retrieved 10 October 2025.
- ^ 大泉, 勝彦 (22 December 2020). "【謎】電車の窓に「謎の大きなQRコード」が貼られている これは何?(1/2)". ねとらぼ (in Japanese). Archived from the original on 10 October 2025. Retrieved 10 October 2025.
- ^ a b "About the patent". Denso-Wave. Archived from the original on 25 June 2016. Retrieved 26 June 2016.
- ^ "DPA". Archived from the original on 26 July 2018. Retrieved 28 July 2016."INPI". Archived from the original on 13 August 2016."UK IPO". 9 March 2013. Archived from the original on 14 June 2019. Retrieved 28 July 2016.
- ^ "QR Code.com". Denso-Wave. 6 November 2003. Archived from the original on 15 September 2012. Retrieved 23 April 2009.
- ^ "UK QR Code Trademark". Archived from the original on 15 September 2012.
- ^ "EU QR Code Trademark". Archived from the original on 15 September 2012.
- ^ "US QR Code Trademark". Archived from the original on 15 September 2012.
- ^ "KR QR Code Trademark Application". 2010. doi:10.8080/4020100059499. Archived from the original on 18 November 2023.
- ^ a b "Jargon Watch", Wired, vol. 20, no. 1, p. 22, January 2012.
- ^ "Malicious Images: What's a QR Code". SANS Technology Institute. 3 August 2011. Archived from the original on 13 July 2012. Retrieved 31 August 2011.
- ^ Waqas, Iam (19 October 2021). "Risks of Using QR Codes and How To Mitigate it – Not As Safe as You Think". Institute of Electrical and Electronics Engineers (IEEE). Retrieved 21 October 2024.
- ^ "Barcode Scanner". 1 June 2011. Archived from the original on 15 September 2012. Retrieved 31 August 2011.
- ^ "QR Droid". 19 August 2011. Archived from the original on 15 September 2012. Retrieved 31 August 2011.
- ^ "ScanLife Barcode Reader". 24 May 2011. Archived from the original on 15 September 2012. Retrieved 31 August 2011.
- ^ "Consumer Alert: QR Code Safety". Better Business Bureau. 23 June 2011. Archived from the original on 15 July 2012. Retrieved 31 August 2011.
- ^ "AVG Cautions: Beware of Malicious QR Codes". PC World. 28 June 2011. Archived from the original on 7 September 2012. Retrieved 31 August 2011.
- ^ "EvilQR – When QRCode goes bad". AppSec-Labs Blog. 14 August 2011. Archived from the original on 15 September 2012. Retrieved 31 August 2011.
- ^ "QR Codes: A Recipe for a Mobile Malware Tsunami". Cyveillance, Inc. 20 October 2010. Archived from the original on 28 July 2012. Retrieved 31 August 2011.
- ^ QR codes hold up to 2.9 KB whereas the smallest known computer virus is about one-tenth that size "The Smallest Virus I Could Manage". Virus Labs and Distribution. 1995. Archived from the original on 15 September 2012. Retrieved 31 August 2011.
- ^ "Beware of Malicious QR Codes". ABC. 8 June 2011. Archived from the original on 1 August 2012. Retrieved 31 August 2011.
- ^ Binder, Matt. "Beware the QR code scams". Mashable. Archived from the original on 17 January 2022. Retrieved 18 January 2022.
- ^ Vincent, James (12 January 2022). "The latest phishing scam to watch out for: fraudulent QR codes on parking meters". The Verge. Archived from the original on 17 January 2022. Retrieved 18 January 2022.
- ^ Wodinsky, Shoshana (12 January 2022). "Scammers Are Using QR Codes to Plunder Parking Meter Payments". Gizmodo. Archived from the original on 18 January 2022. Retrieved 18 January 2022.
Bibliography
[edit]- BS ISO/IEC 18004:2006. Information technology. Automatic identification and data capture techniques. Bar code symbology. QR Code. Geneva: ISO/IEC. 2000. p. 114. OCLC 60816353.
- BS ISO/IEC 18004:2006. Information technology. Automatic identification and data capture techniques. QR Code 2005 bar code symbology specification. London: BSI. 2007. p. 126. ISBN 978-0-580-67368-9. Retrieved 4 May 2023.
External links
[edit]- Reed Solomon Codes for Coders – an elaborate tutorial on Wikiversity, covering both QR code structure and the Reed Solomon codes used to encode the data.
QR code
View on GrokipediaHistory
Invention and Early Development
The QR code, a two-dimensional matrix barcode, was developed in 1994 by Denso Wave Incorporated, a subsidiary of Denso Corporation affiliated with Toyota, to enable faster and more reliable tracking of automotive parts during manufacturing.[1] Traditional one-dimensional barcodes were limited to about 20 alphanumeric characters and required precise linear scanning, which proved inefficient in flexible production lines where parts were often dirty or scanned at angles.[1] The name "QR" denotes "Quick Response," reflecting the primary design goal of high-speed readability exceeding that of prior codes by over tenfold.[9] Development originated in 1992 when manufacturing divisions requested improvements to barcode systems, prompting Masahiro Hara, an engineer specializing in barcode scanners and image processing, to lead a two-person team.[1] Hara addressed key constraints by creating a square grid layout with position detection patterns—large squares in three corners featuring a nested black-to-white module ratio of 1:1:3:1:1—for omnidirectional detection across 360 degrees without needing rotation.[9] This structure, combined with alignment patterns and timing coordinates, allowed robust positioning even under distortion or partial occlusion.[1] The code's capacity reached approximately 7,000 numeric digits or supported Kanji and Kana characters, enabling encoding of complex identifiers like part numbers and serial data.[9] Integrated Reed-Solomon error correction provided resilience against up to 30% data loss from damage or dirt, a critical advancement for industrial environments.[1] Initial deployment focused on Denso's internal automotive supply chain, where it streamlined inventory and assembly processes by reducing scan times and errors.[1]Adoption in Japan
The QR code was initially adopted in Japan within the automotive manufacturing sector following its invention in 1994 by Denso Wave, a subsidiary of Denso Corporation, to track vehicle parts more efficiently than traditional barcodes.[1] This industrial application addressed the need for rapid scanning and high data capacity in factory environments, where parts required detailed information such as serial numbers and specifications.[9] By making the QR code specification publicly available and royalty-free, Denso Wave encouraged broader implementation across logistics and supply chain operations in Japan during the late 1990s.[9] Consumer adoption accelerated in the early 2000s, driven by Japan's early proliferation of camera-equipped mobile phones, which integrated QR code reading capabilities by around 2002.[9] These devices enabled seamless access to URLs, electronic tickets, and product details encoded in QR codes printed on advertisements, magazines, and public signage, marking a shift from industrial to everyday use.[10] This integration aligned with Japan's advanced mobile infrastructure, where feature phones dominated and supported quick-response functionalities for marketing and information retrieval.[11] By 2002, QR codes had achieved widespread public usage in Japan, appearing on billboards, train tickets, and vending machines to facilitate payments and content delivery.[9] Their proliferation was further boosted by non-proprietary licensing, allowing companies to embed QR readers in devices without legal barriers, contrasting with more restricted barcode technologies.[1] In subsequent years, adoption extended to contactless payments; for instance, QR-based systems gained traction after 2018 with services like PayPay, reflecting a market response to cashless initiatives amid Japan's traditionally high cash usage.[12] This evolution underscored QR codes' role in Japan's digital transformation, from manufacturing efficiency to ubiquitous consumer interfacing.[13]Global Standardization and Expansion
Following its initial adoption within Japan's automotive sector and subsequent integration into consumer applications via camera-equipped mobile phones around 2002, QR code technology underwent formal internationalization to facilitate broader implementation. Denso Wave, the developer, actively pursued global standards, achieving registration with the Association for Automatic Identification and Mobility (AIM) International in October 1997, followed by Japanese Industrial Standards (JIS X 0510) approval in January 1999, and culminating in ISO/IEC 18004 ratification in June 2000.[5][14] This ISO standard defined the symbology's characteristics, including data encoding, error correction, and printing tolerances, enabling consistent interoperability across manufacturers and regions.[15] To accelerate diffusion beyond proprietary control, Denso Wave adopted a royalty-free policy, relinquishing patent enforcement and permitting unrestricted use without licensing fees, a deliberate strategy to prioritize societal benefit over revenue extraction.[16][17] This openness contrasted with licensed barcodes like DataMatrix, fostering industrial uptake in logistics, pharmaceuticals, and electronics worldwide by the mid-2000s, where QR codes' higher capacity—up to 7,089 numeric characters versus 2,335 for PDF417—provided advantages in supply chain tracking.[11] Public expansion lagged industrial applications until smartphone proliferation; by 2010, dedicated scanning apps on iOS and Android platforms reduced barriers, spurring marketing uses such as event ticketing and product information links in Europe and North America.[18] Adoption intensified during the COVID-19 pandemic from 2020, with contactless implementations for menus, payments, and health passes driving usage; surveys indicated 90% familiarity in the UK by 2021, alongside billions of annual scans globally.[19] By 2025, projections estimated over 2.9 billion users worldwide, reflecting entrenched roles in digital payments (e.g., in China and Southeast Asia) and augmented reality integrations, though vulnerabilities to counterfeiting prompted ongoing security enhancements like dynamic codes.[20]Standards
ISO and International Standards
The QR Code symbology is specified in the international standard ISO/IEC 18004, which was first approved in June 2000.[5] This standard outlines the core requirements for QR Code implementation, including symbology characteristics such as matrix layout, finder patterns, and alignment structures; data character encoding methods for numeric, alphanumeric, byte/binary, and Kanji modes; symbol formats and dimensions across 40 versions; error correction using Reed-Solomon codes at four levels (L, M, Q, H); and a reference decoding algorithm to ensure reliable scanning.[15][6] The standard encompasses both legacy QR Code Model 1 (limited to version 14 with basic error correction) and the predominant Model 2 (up to version 40 with enhanced capacity and alignment patterns for larger sizes), promoting backward compatibility while favoring Model 2 for new applications due to its superior data density and robustness.[21] It also incorporates the Micro QR Code variant from the second edition onward, a compact format with fewer modules (11x11 to 17x17) and a single finder pattern, suitable for space-constrained uses like small packaging labels.[22] ISO/IEC 18004 has undergone revisions to address evolving needs: the 2006 edition (second) integrated Micro QR Code and refined encoding for better efficiency; the 2015 edition (third) consolidated specifications and improved verification guidelines; and the 2024 edition (fourth) introduced optimizations in encoding, enhanced error correction capabilities, and refinements to structured append features for linking multiple symbols.[23][24] These updates maintain interoperability across devices while adapting to higher data demands, with the standard purchasable from ISO for detailed technical implementation.[25] Related international efforts include adoption by bodies like AIM International for barcode guidelines and GS1 for supply chain applications, but ISO/IEC 18004 remains the foundational reference for global QR Code compliance.[5] In Japan, where QR Code originated, complementary national standards such as JIS X 0500 (for standard QR Code) and JIS X 0510 (for Micro QR Code) align closely with ISO specifications, facilitating early domestic adoption before full internationalization.[5] A distinct extension, the Rectangular Micro QR Code (rMQR), is covered under ISO/IEC 23941:2022, supporting elongated formats for narrow printing surfaces like receipts.[5]Capacity and Compatibility Specifications
QR Codes are defined in 40 versions, ranging from Version 1 (21×21 modules) to Version 40 (177×177 modules), with each subsequent version increasing the side length by 4 modules to accommodate greater data density.[4] The data capacity of a QR Code symbol varies according to its version, the encoding mode (numeric, alphanumeric, byte/binary, or Kanji), and the selected error correction level, which trades usable data space for redundancy to enable recovery from damage or occlusion.[4][5] Error correction is implemented using Reed-Solomon codes at four levels: Level L (approximately 7% data recovery), Level M (15%), Level Q (25%), and Level H (30%), allowing the symbol to remain readable despite partial destruction or poor printing.[3] Higher correction levels reduce effective capacity; for instance, in Version 40 (the largest standard size), Level L supports up to 7,089 numeric characters, while Level H drops to about 3,273 in the same mode.[5][26] The following table summarizes maximum capacities for Version 40 across encoding modes and error correction levels, based on the ISO/IEC 18004 specification for Model 2 symbols:| Encoding Mode | Level L | Level M | Level Q | Level H |
|---|---|---|---|---|
| Numeric | 7,089 | 5,596 | 4,576 | 3,273 |
| Alphanumeric | 4,296 | 3,391 | 2,773 | 1,983 |
| Byte/Binary | 2,953 | 2,330 | 1,906 | 1,363 |
| Kanji | 1,817 | 1,433 | 1,172 | 838 |
Design
Module Structure and Patterns
A QR code symbol comprises a square grid of black and white modules, with sizes ranging from 21×21 modules in Version 1 to 177×177 modules in Version 40.[4] The modules form fixed patterns for detection and variable areas for data encoding, adhering to the ISO/IEC 18004 standard.[22] These patterns ensure reliable scanning by providing reference points for position, orientation, and size determination.[29] The three finder patterns, positioned at the top-left, top-right, and bottom-left corners, enable initial detection of the symbol's location and coarse alignment.[30] Each finder pattern consists of a 7×7 array of modules structured as nested squares: a central 3×3 dark block surrounded by a 1-module light frame and an outer 5×5 dark frame, allowing scanners to identify the pattern from multiple angles due to its concentric design.[31] A separator pattern of light modules borders each finder to distinguish it from adjacent areas.[24] Timing patterns, consisting of alternating dark and light modules, extend horizontally between the top-left and top-right finder patterns and vertically between the top-left and bottom-left finder patterns.[29] These lines assist scanners in determining the exact number of modules per side and establishing the grid's coordinate system.[14] Alignment patterns, present in versions 2 and larger, are smaller square markers distributed across the symbol to compensate for warping or distortion in larger codes.[29] Each alignment pattern features a 5×5 dark block with a 1-module light frame and an outer light border, positioned according to version-specific tables to normalize the module grid.[14] Versions exceeding 45 modules include multiple such patterns for enhanced correction.[29] Format information areas, located adjacent to the finder patterns (specifically, below the top-left and top-right finders, and to the right of the bottom-left finder), encode the error correction level and data mask pattern used.[32] These 15-bit fields include BCH error correction for redundancy and are mirrored in protected positions to ensure readability.[32] For versions 7 through 40, version information modules appear in the bottom-left (above the alignment pattern) and top-right (below the finder pattern) areas, encoding an 18-bit BCH-coded value indicating the symbol version.[32] The entire symbol is enclosed by a quiet zone, a minimum 4-module-wide border of light modules that isolates the QR code from surrounding elements, facilitating accurate edge detection by scanners.[33] This margin prevents interference and is essential for compliance with scanning specifications. The remaining modules in the central area store encoded data interleaved with Reed-Solomon error correction codewords.[14]Data Encoding Process
The data encoding process in QR codes converts input information into a compact binary bitstream, optimized for the selected version's capacity and error correction level. This begins with mode selection, where the input data determines the encoding scheme: numeric for digit sequences (0-9), alphanumeric for digits plus uppercase letters (A-Z) and symbols ($%*+-./: space), byte for arbitrary ISO-8859-1 characters, or Kanji for Shift JIS double-byte characters.[30] [34] Mode choice prioritizes efficiency, as numeric mode maximizes capacity (up to 7,089 characters in version 40, low error correction) over byte mode (up to 2,953 characters).[35] A mode indicator precedes the data, using 4 bits for versions 1-9 (0001 binary for numeric, 0010 for alphanumeric, 0100 for byte, 1000 for Kanji), extending to 8 or 12 bits in larger versions to accommodate extended modes.[35] [34] This is followed by a character count indicator, whose bit length varies by version and mode (e.g., 10 bits for numeric in versions 1-9, up to 16 bits in version 40).[34] Data encoding then maps input to bits per mode rules:- Numeric: Digits grouped in threes, each group converted to a 10-bit binary value (000 to 999 fits 10 bits); remainders encoded as 4-bit (one digit) or 7-bit (two digits) values.
- Alphanumeric: Character pairs mapped to a 45x45 table (11 bits per pair, as ); single trailing character uses 6 bits.
- Byte: Direct 8 bits per character.
- Kanji: Each character to 13 bits after subtracting 0x8140/0xa1a0 offsets and multiplying by appropriate factors.[30] [35]
Error Correction and Reed-Solomon Codes
QR codes employ Reed-Solomon codes, a class of non-binary cyclic error-correcting codes, to detect and correct errors arising from physical damage, dirt, or poor printing.[3] These codes operate over the finite field GF(256), where each symbol consists of 8 bits, enabling correction of symbol-level errors rather than individual bits.[36] The redundancy introduced by parity symbols allows scanners to reconstruct missing or corrupted data, ensuring readability even when up to 30% of the code is obscured, depending on the selected level.[5] Four error correction levels are specified: L (approximately 7% of codewords recoverable), M (15%), Q (25%), and H (30%).[5][24] Higher levels allocate more modules to parity data, reducing the effective information capacity but enhancing robustness against environmental degradation, such as in industrial settings or printed media exposed to wear.[3] The level is encoded in the code's format information, allowing decoders to apply the appropriate correction parameters.[37] During encoding, binary data is first converted to a sequence of GF(256) symbols via BCH or other preprocessing, then divided into multiple blocks to distribute errors and improve burst error correction.[3] For each block, a Reed-Solomon encoder computes parity symbols using a generator polynomial derived from the primitive element α of GF(256), defined by the irreducible polynomial .[38] The code is RS(n, k), where n is the total symbols per block (data plus parity), k is data symbols, and the number of parity symbols 2t = n - k permits correction of up to t erroneous symbols per block via syndrome decoding and error locator polynomials. Interleaving of codewords across blocks further mitigates consecutive errors, as a single burst affects only one symbol per block, which can be corrected independently if within the t limit.[3] This mechanism, standardized in ISO/IEC 18004, enables QR codes to achieve higher reliability than one-dimensional barcodes, which lack comparable redundancy.[24] In practice, level H codes have demonstrated recovery from severe damage, such as partial burning or heavy soiling, as tested in early development by Denso Wave.[1]Masking and Readability Optimization
Masking in QR codes involves applying one of eight predefined patterns to invert specific data and error correction modules, thereby disrupting uniform regions of black or white that could hinder scanner detection and improving overall contrast balance for reliable reading under varied conditions. This step occurs after data encoding and error correction placement but excludes fixed functional patterns like finders, timing, and alignment markers. Each mask pattern is defined by a condition evaluated at each module's row index and column index ; if true, the module's color is inverted via XOR operation.[39][40] The eight patterns follow these rules:| Pattern | Inversion Condition |
|---|---|
| 0 | |
| 1 | |
| 2 | |
| 3 | |
| 4 | |
| 5 | |
| 6 | |
| 7 |
Capacity and Variants
Information Capacity Limits
The information capacity of QR codes is constrained by the symbol version, data encoding mode, and error correction level, with maximum storage achieved in version 40 at the lowest error correction.[5] QR code versions range from 1 (21×21 modules) to 40 (177×177 modules), where larger versions accommodate more data at the expense of physical size.[4] Data modes include numeric (highest density, 3.33 bits per character), alphanumeric (5.5 bits per character), byte/binary (8 bits per character), and kanji (13.25 bits per character), with numeric mode yielding the greatest capacity for digit-only content.[5] Error correction employs Reed-Solomon codes at four levels: L (approximately 7% data recovery), M (15%), Q (25%), and H (30%), where higher levels allocate more codewords to redundancy, reducing usable data capacity.[5] For version 40 at level L, maximum capacities are 7,089 numeric characters, 4,296 alphanumeric characters, 2,953 bytes, and 1,817 kanji characters, equivalent to roughly 23,624 bits of binary data.[5] [42] At level H, capacities drop significantly, such as to approximately 1,852 alphanumeric characters in practical encodings.[4]| Data Mode | Level L (Version 40) | Level H (Version 40, approx.) |
|---|---|---|
| Numeric | 7,089 characters | 3,597 characters |
| Alphanumeric | 4,296 characters | 2,237 characters |
| Byte | 2,953 bytes | 1,527 bytes |
| Kanji | 1,817 characters | 923 characters |























![Meaning of format information. In the above figure, the format information is protected by a (15,5) BCH code, which can correct up to 3 bit errors. The total length of the code is 15 bits, of which 5 are data bits (2 EC level + 3 mask pattern) and 10 are extra bits for error correction. The format mask pattern for these 15 bits is: [101010000010010]. Note that we map the masked values directly to its meaning here, in contrast to image 4 "Levels & Masks" where the mask pattern numbers are the result of putting the 3rd to 5th mask bit, [101], over the 3rd to 5th format info bit of the QR code.](http://upload.wikimedia.org/wikipedia/commons/thumb/3/3b/QR_Format_Information.svg/330px-QR_Format_Information.svg.png)